retro
Introduction
Information Gathering
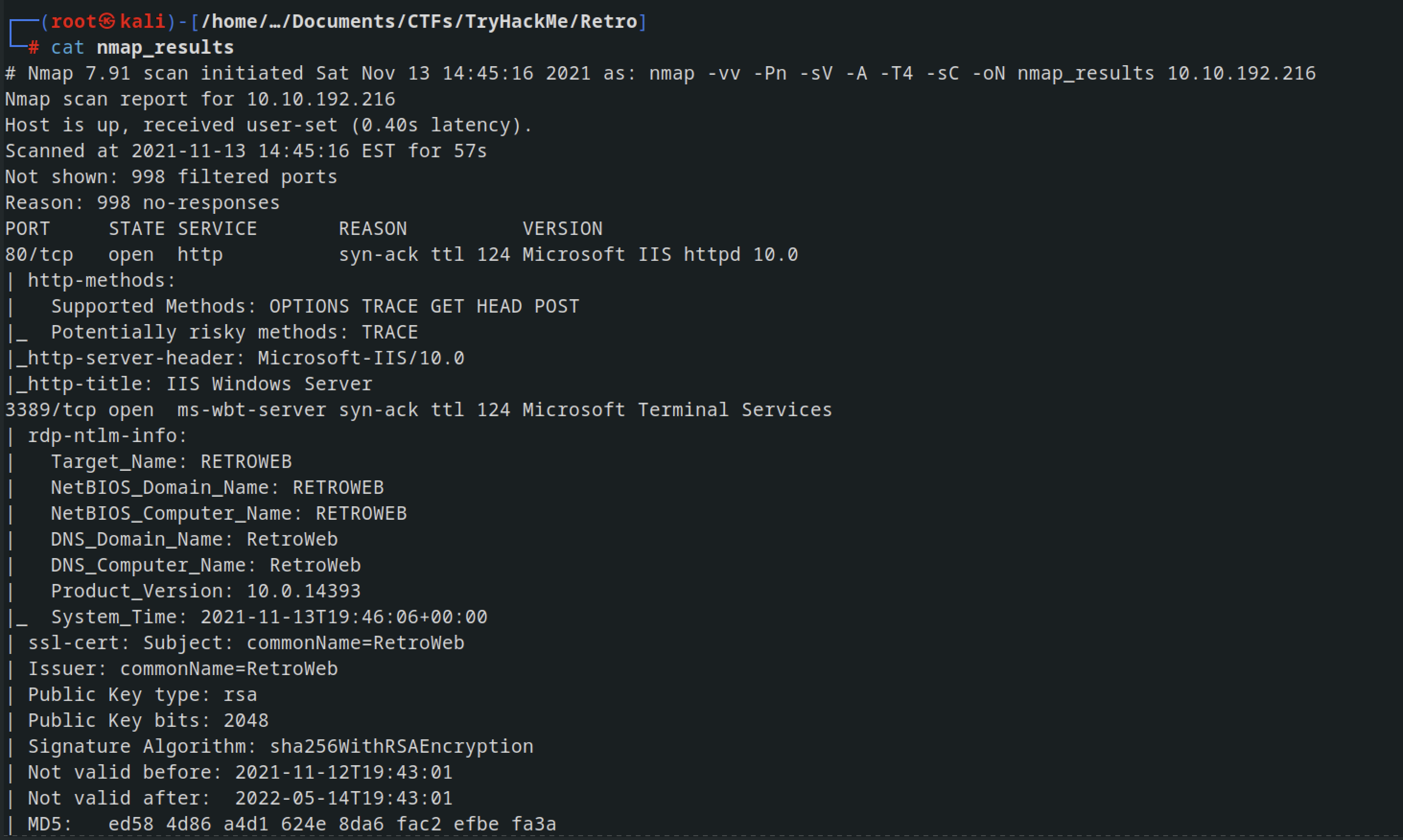
Started with an Nmap scan and discovered that two ports were open:
1
nmap -Pn -sV -A -vv -oN nmap_scans 10.10.104.203
Here are the details:
- Port 80 (HTTP): Likely used for web traffic.
- Port 3389 (RDP): Identified as Remote Desktop Protocol (RDP).
Directory Enumeration
Did dirsearch but got nothing
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿kali)-[/home/sire/Downloads]
└─# dirsearch -u http://10.10.104.203 --exclude-status 403,404
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/sire/Downloads/reports/http_10.10.104.203/_24-02-14_14-36-09.txt
Target: http://10.10.104.203/
[14:36:09] Starting:
Task Completed
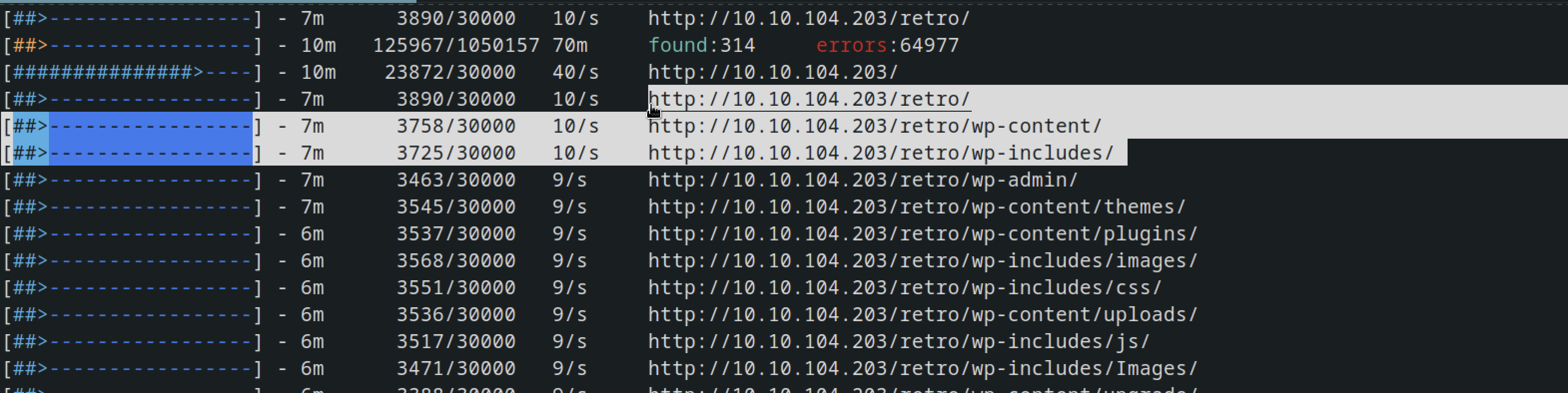
but when I tried feroxbuster I got something a hidden germ /retro
feroxbuster -u http://10.10.104.203
I checked the target website using my web browser and found out it was running on WordPress: 
Then, I tried using a tool called WPScan to learn more, but I got an error message:
1
2
can Aborted: The URL supplied redirects to http://localhost/retro/wp-login.php?redirect_to=http://10.10.104.203/retro/wp-admin/&reauth=1. Use the --ignore-main-redirect option to ignore the redirection and scan the target, or change the --url option value to the redirected URL.
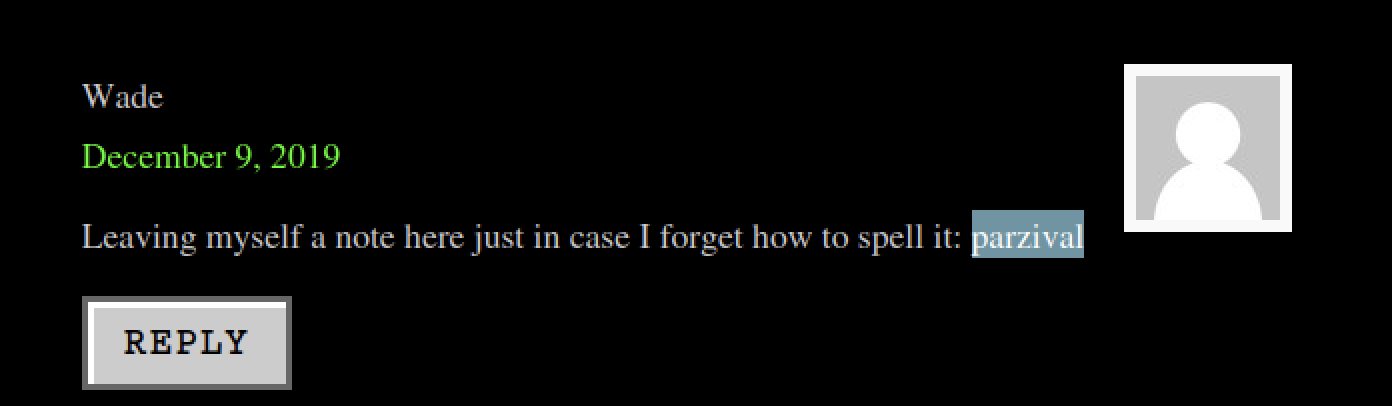
Still, I didn’t give up. I looked around the website carefully and found some potential login details:
- Username:
wade - Password:
parzival
Port 3389
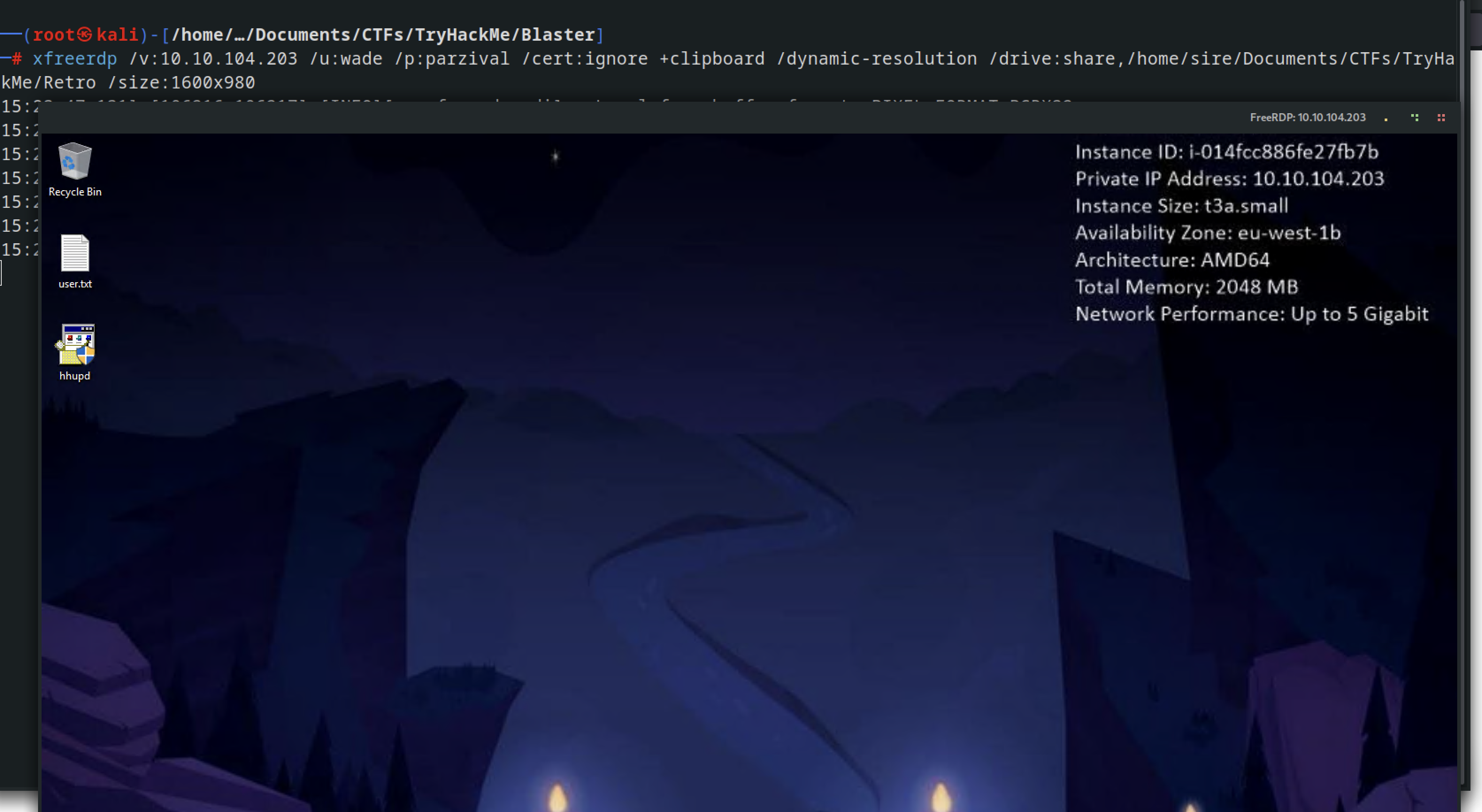
With the credentail acqured I tried to connect to the machine using the remote protocol port with the following command:
1
xfreerdp /v:10.10.104.203 /u:wade /p:parzival /cert:ignore +clipboard /dynamic-resolution /drive:share,/home/sire/Documents/CTFs/TryHackMe/Retro /size:1600x980
and walla, we are in
Vulnerability Analysis
After pockig around I came to this history that was in chrom browser CVE 2019-1388 
After doing some googling I found this
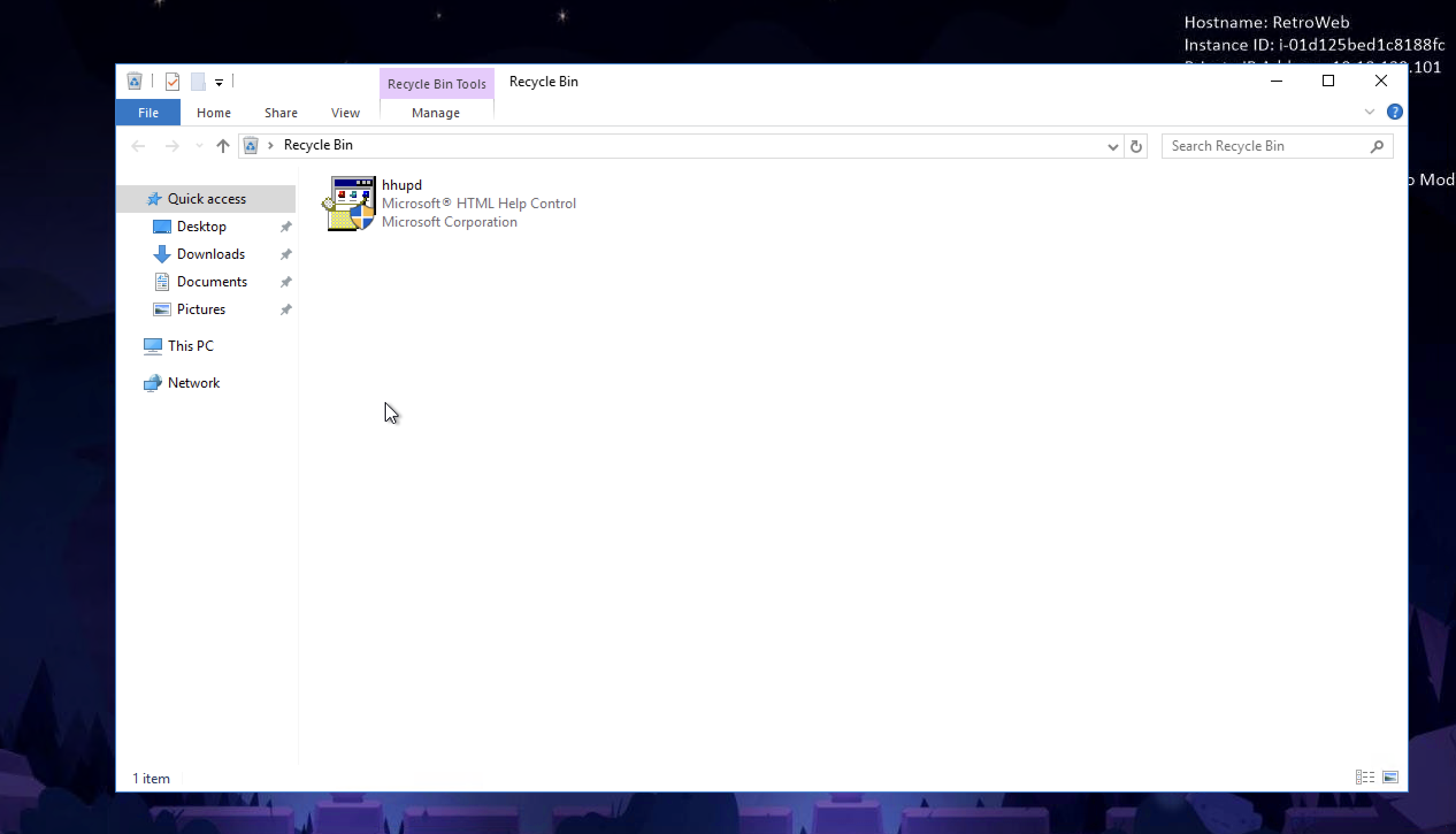
There was this file we had to download to the machine but we had no internet and looking at the trash folder I found it
Exploitation
I copied the file to the desktop and opened it, going to more brought me here
To view the certificate details:
Click “Show more details” to expand the dialog box. Select “Show information about the publisher’s certificate.” A new window will appear with the certificate properties. Under the General tab, note the issuer is VeriSign Commercial Software Publishers CA. Click the link to view more information about the Issuer. 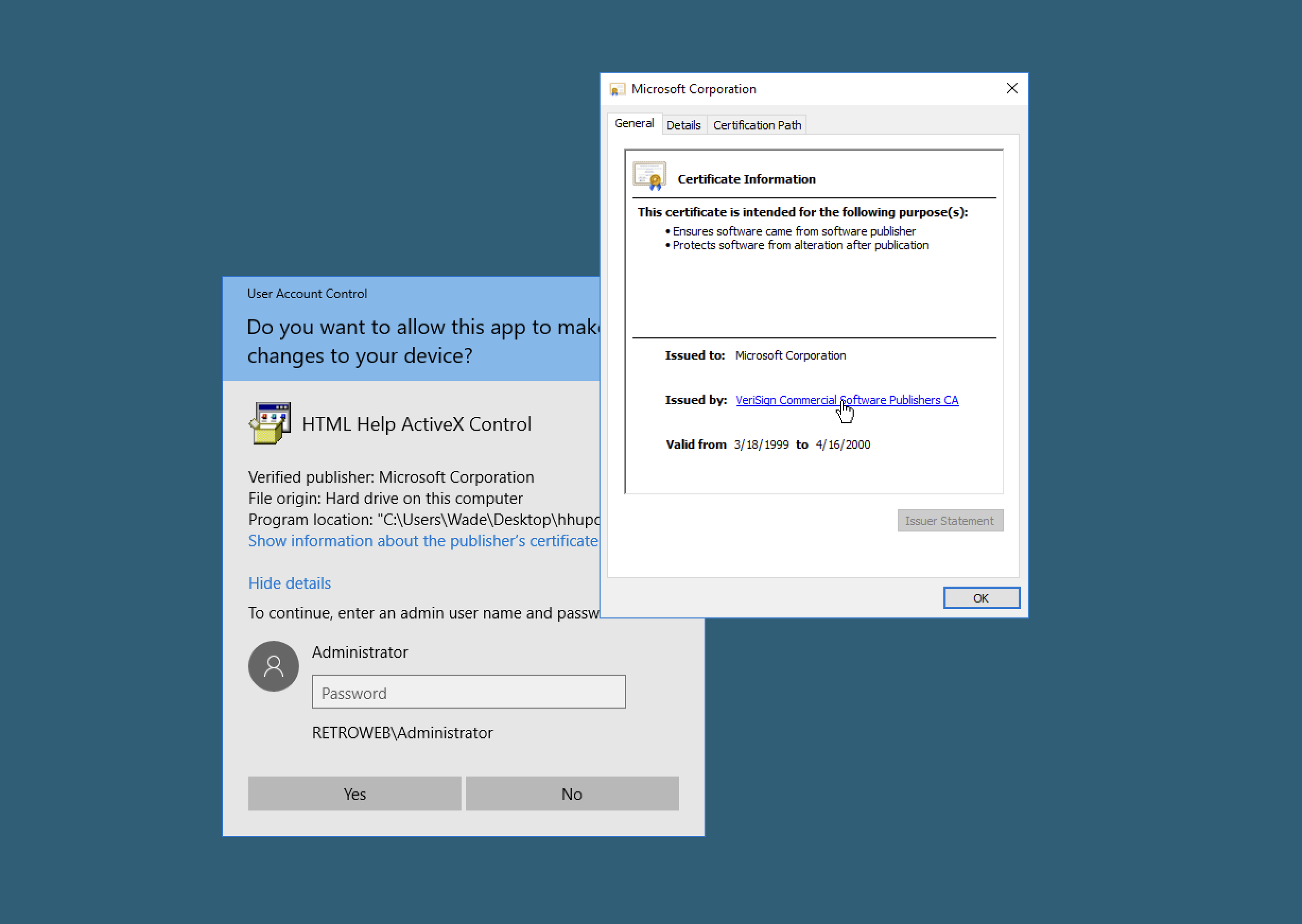
To exploit:
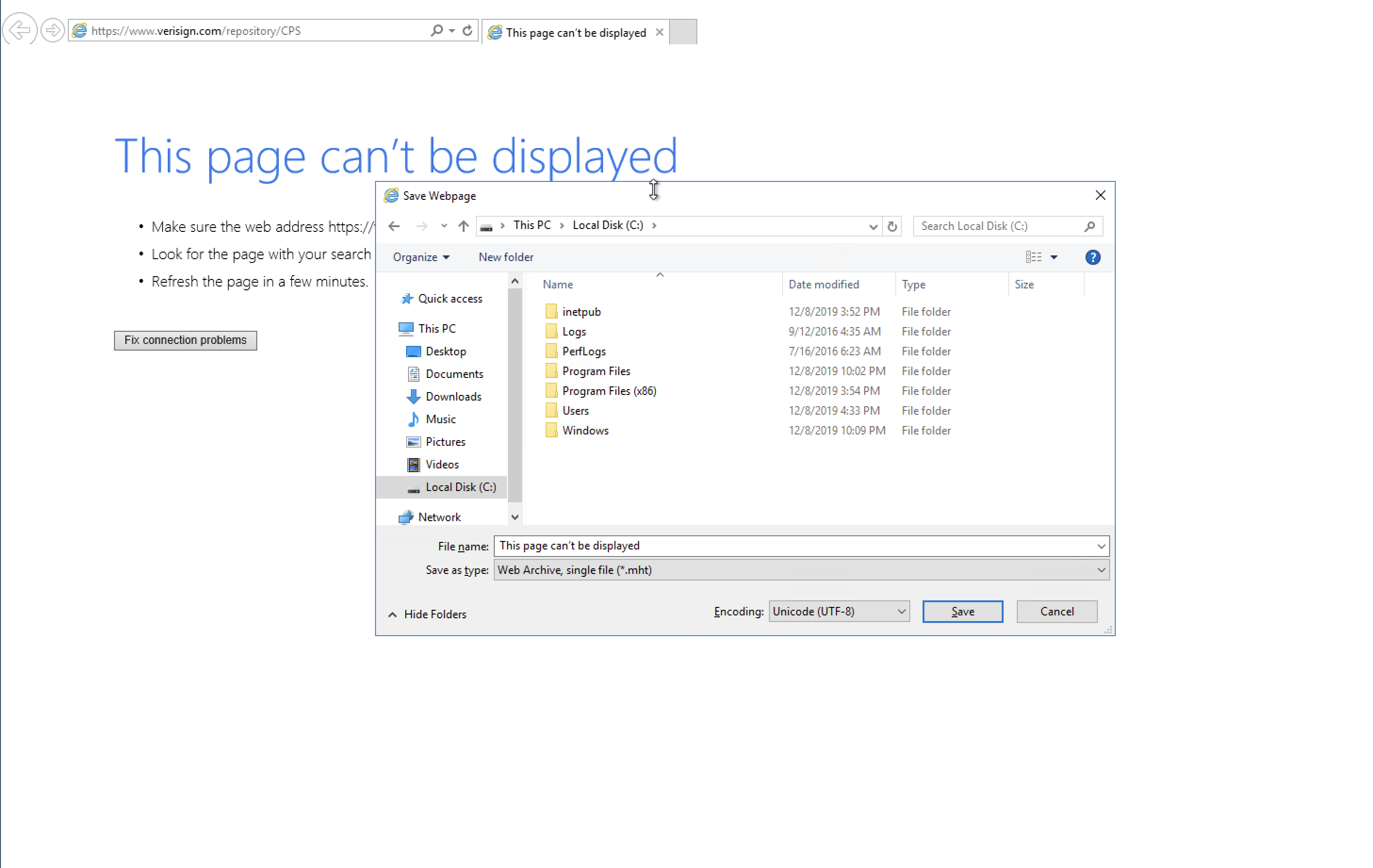
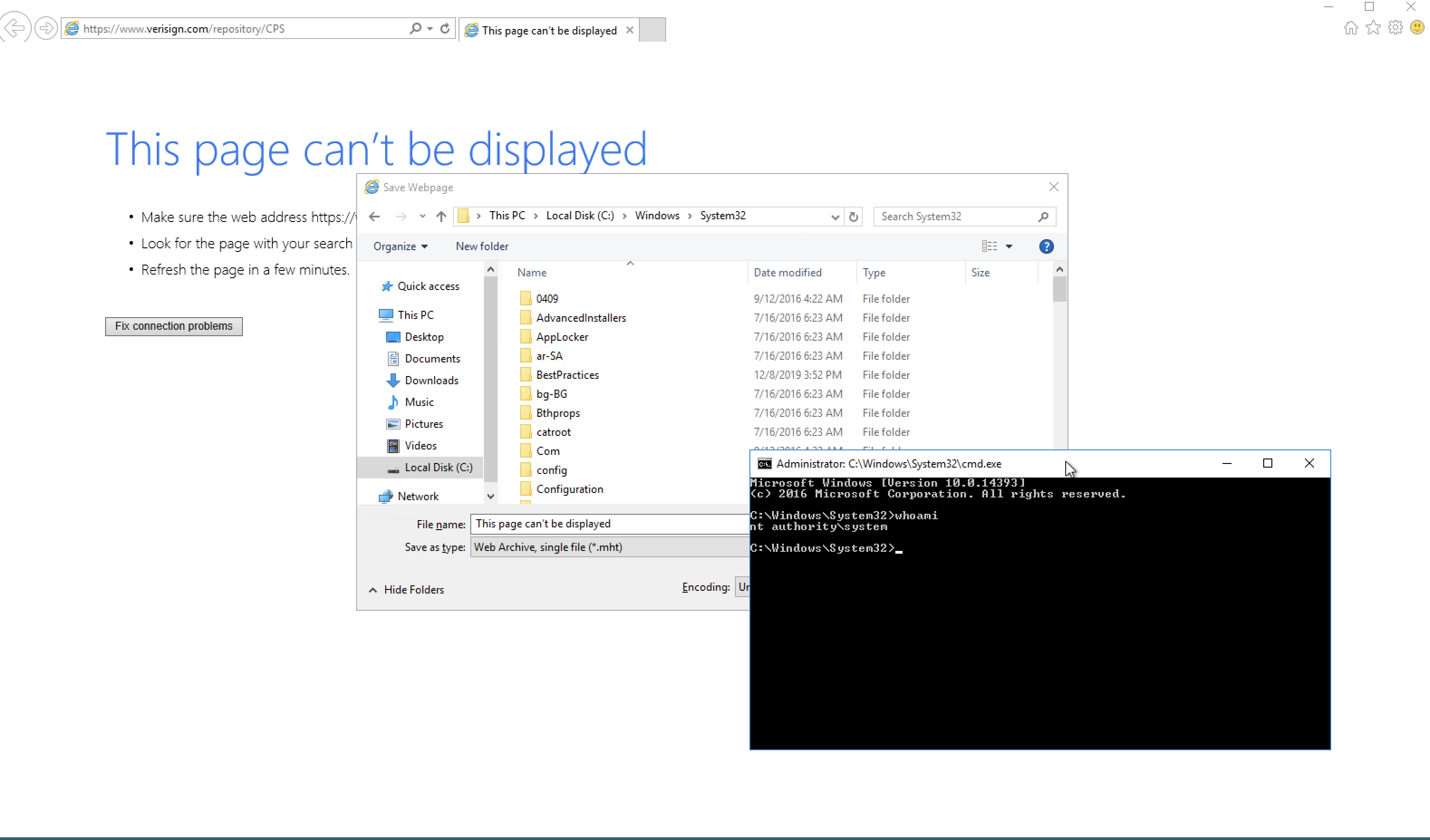
Choose to open the link with either Google Chrome or Internet Explorer. Opt for Internet Explorer for reliability. Internet Explorer will open as SYSTEM. Close other windows and wait for Internet Explorer to load. You may encounter a “This page can’t be displayed” error due to the lack of internet connection.
Crt + s to save the file and browse to C:\Windows\System32 where you will find cmd, run cmd by default and you will be root