MS17-010
Table of content
- Intoduction
Hacking Phases in Bizness HTB
Let’s Begin
- Information Gathering
- Directory Enumeration
- Vulnerability Analysis
- Exploitation
- Privilege Escalation
- Conclusion
Introduction
Information Gathering
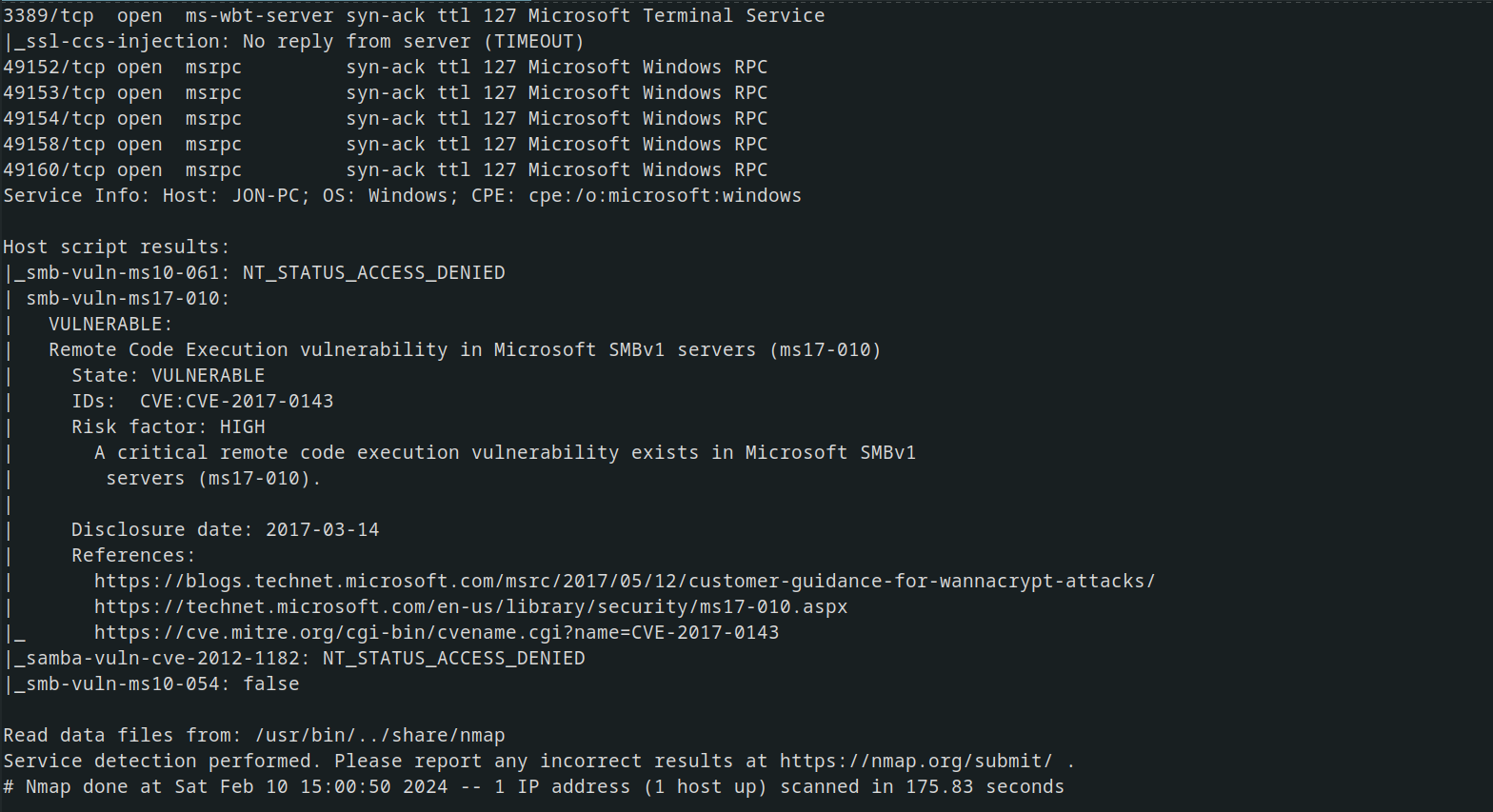
How about we begin by nmap a scans to check which ports are currently being used?
1
nmap -sV --script=vuln -T4 10.10.20.214 -oN nmap.scans2 -vv
…..
Directory Enumeration
………
Vulnerability Analysis
……………..
Exploitation
TOBE continues …..
CVE-2023-51467 and CVE-2023-49070
This post is licensed under CC BY 4.0 by the author.