DumpMe
What is the SHA1 hash of Triage-Memory.mem (memory dump)?
c95e8cc8c946f95a109ea8e47a6800de10a27abd
What volatility profile is the most appropriate for this machine? (ex: Win10x86_14393)
using volatility to be specific in the “suggested profile”, the first profile is the most appropriate for your machine. Make sure you’re in the same directory where the file is located.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# python2 tools/volatility/vol.py -f Triage-Memory.mem imageinfo
Volatility Foundation Volatility Framework 2.6.1
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/sire/Documents/CTFs/cyberdefender/memorydump/Triage-Memory.mem)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf800029f80a0L
Number of Processors : 2
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff800029f9d00L
KPCR for CPU 1 : 0xfffff880009ee000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2019-03-22 05:46:00 UTC+0000
Image local date and time : 2019-03-22 01:46:00 -0400
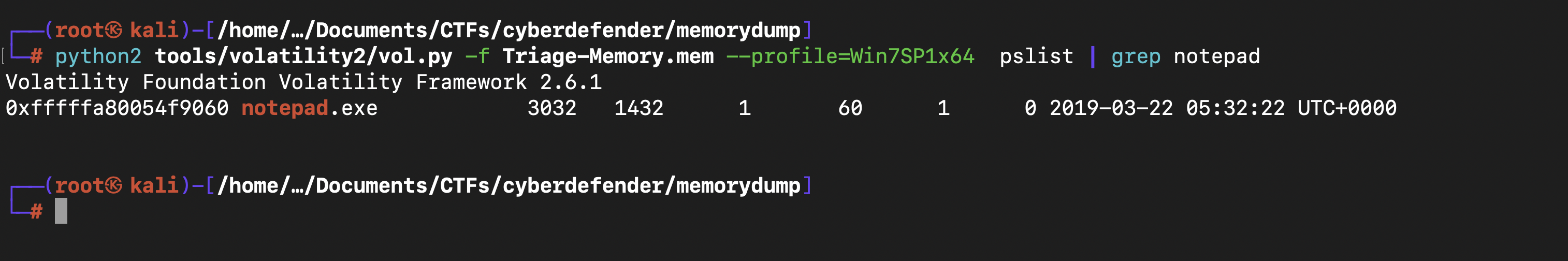
What was the process ID of notepad.exe?
The “pslist” plugin shows all of the processes and their PIDs. So carefully look for the PID of the corresponding desired process. In this case it is “notepad.exe”. Make sure you use double hyphen (-) before profile.
1
2
3
4
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 pslist | grep notepad
Volatility Foundation Volatility Framework 2.6.1
0xfffffa80054f9060 notepad.exe 3032 1432 1 60 1 0 2019-03-22 05:32:22 UTC+0000
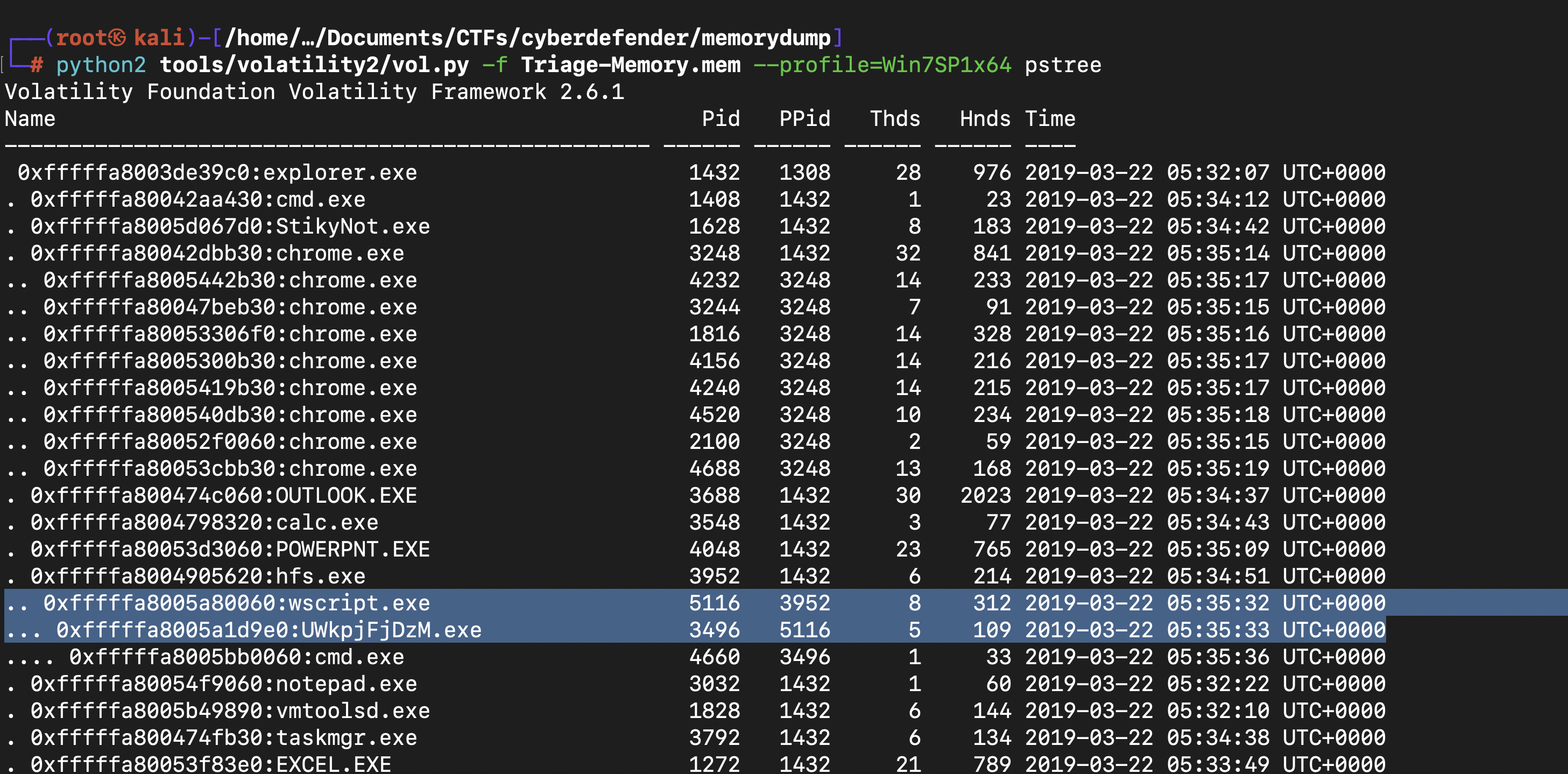
Name the child process of wscript.exe.
The ‘pstree’ plugin is used to identify the parent and child processes. In this case we want to look for the child process of “wscript.exe”,which has been highlighted in the screenshot above.
python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 pstree
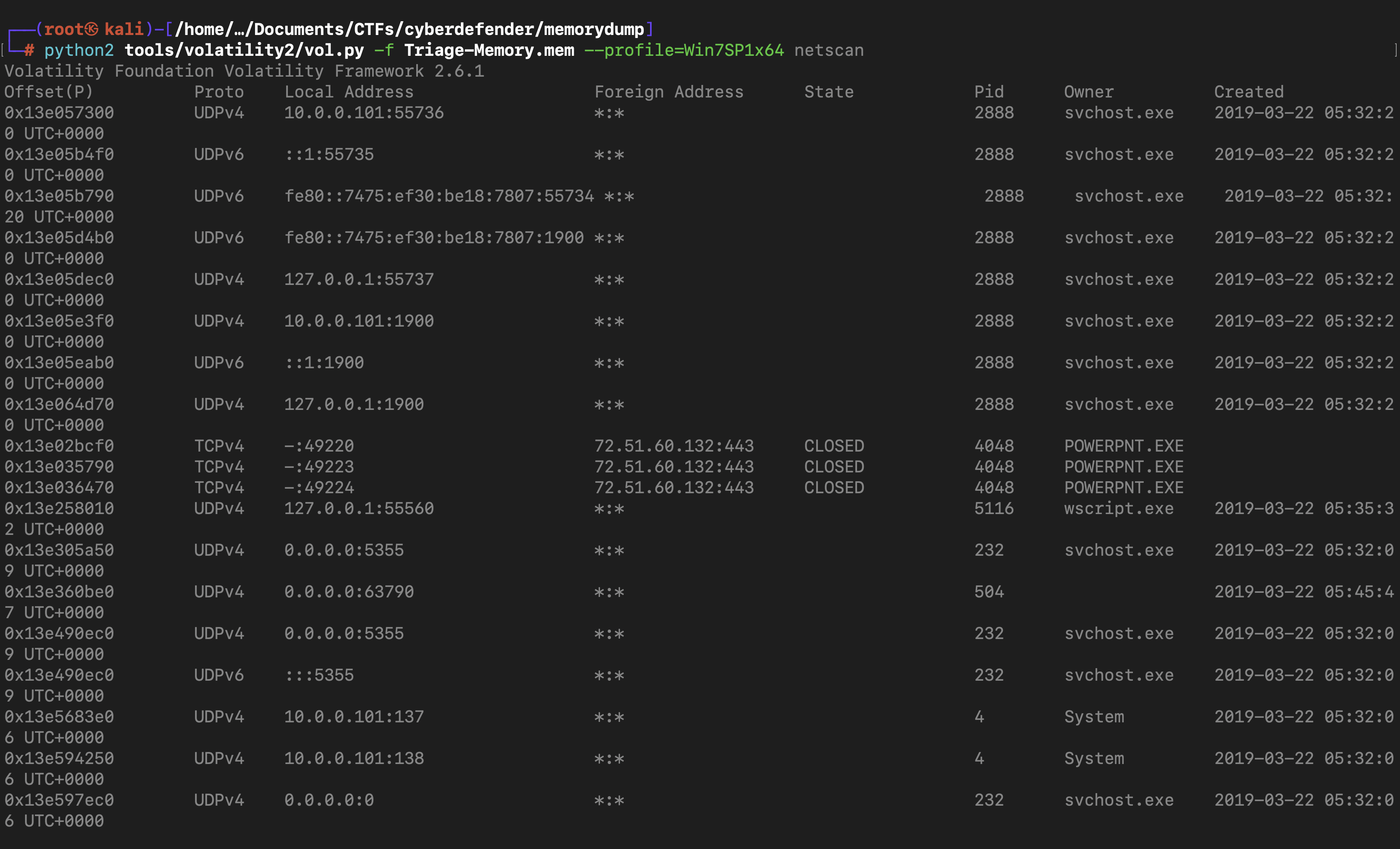
What was the IP address of the machine at the time the RAM dump was created?
The “netscan” plugin provides us with all the network connections of the system. The IP addresses are mentioned in the Local Address column. The IP address of the machine system has been highlighted in the screenshot attached above.
python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 netscan
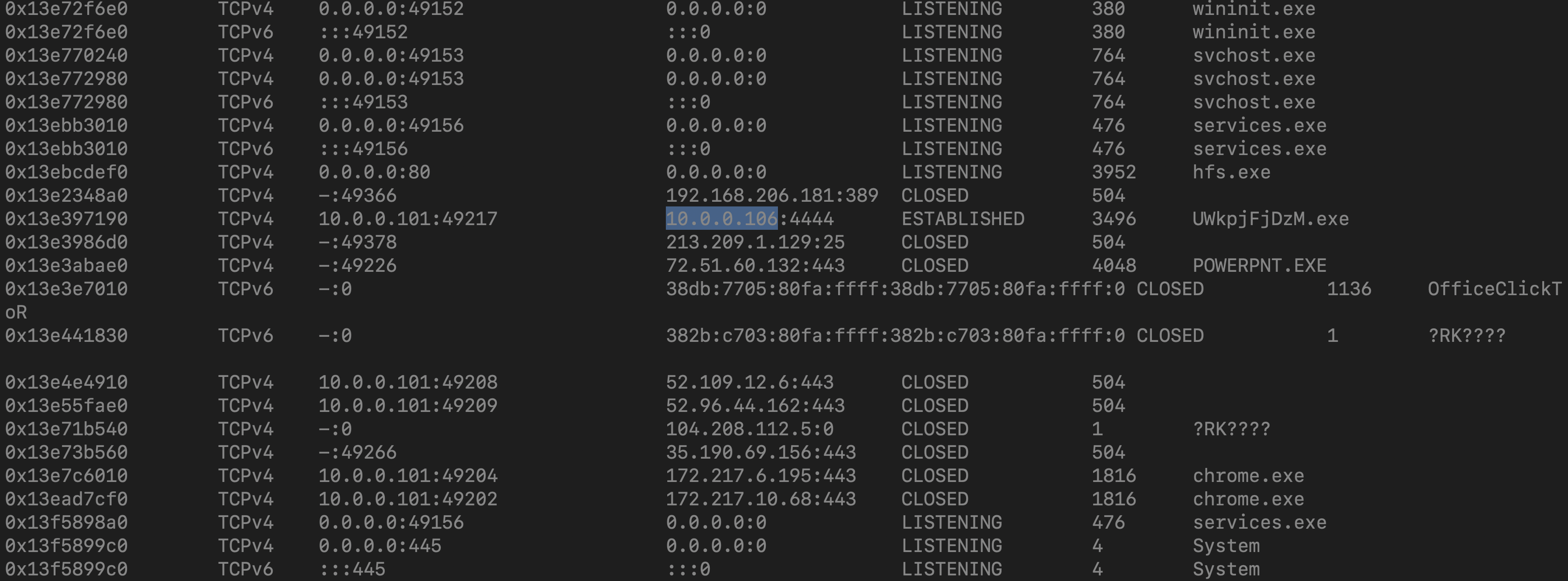
Based on the answer regarding the infected PID, can you determine the IP of the attacker?
How many processes are associated with VCRUNTIME140.dll?
1
2
3
4
5
6
7
8
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 dlllist | grep VCRUNTIME140
Volatility Foundation Volatility Framework 2.6.1
0x000007fefa5c0000 0x16000 0xffff 2019-03-22 05:32:05 UTC+0000 C:\Program Files\Common Files\Microsoft Shared\ClickToRun\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0xffff 2019-03-22 05:33:49 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0xffff 2019-03-22 05:34:37 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0x3 2019-03-22 05:34:49 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
0x00000000745f0000 0x15000 0xffff 2019-03-22 05:35:09 UTC+0000 C:\Program Files (x86)\Microsoft Office\root\Office16\VCRUNTIME140.dll
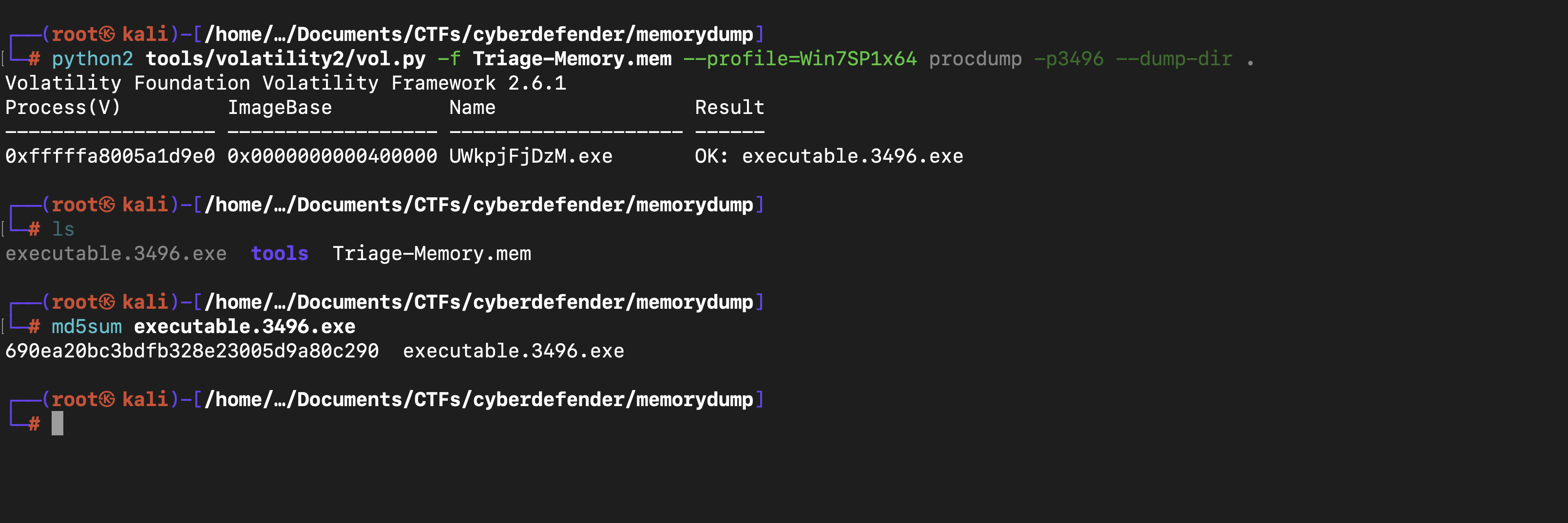
After dumping the infected process, what is its md5 hash?
the suspicious process seems to be with the command python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 pstree
1
2
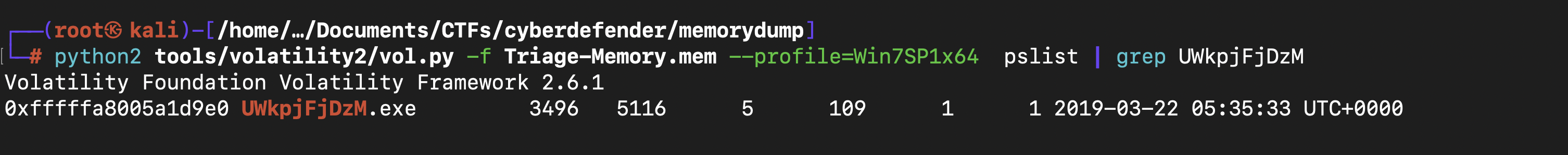
... 0xfffffa8005a1d9e0:UWkpjFjDzM.exe 3496 5116 5 109 2019-03-22 05:35:33 UTC+0000
You can see even the process wscript.exe is child process of hfs.exe which is not easily to see these process wscript.exe with pslist escecially if there are lot of processes. Then these process wscript.exe open another process UWkpjFjDzM.exe which inturn open cmd process which is very dangerous and with the following command python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 procdump -p3496 --dump-dir .
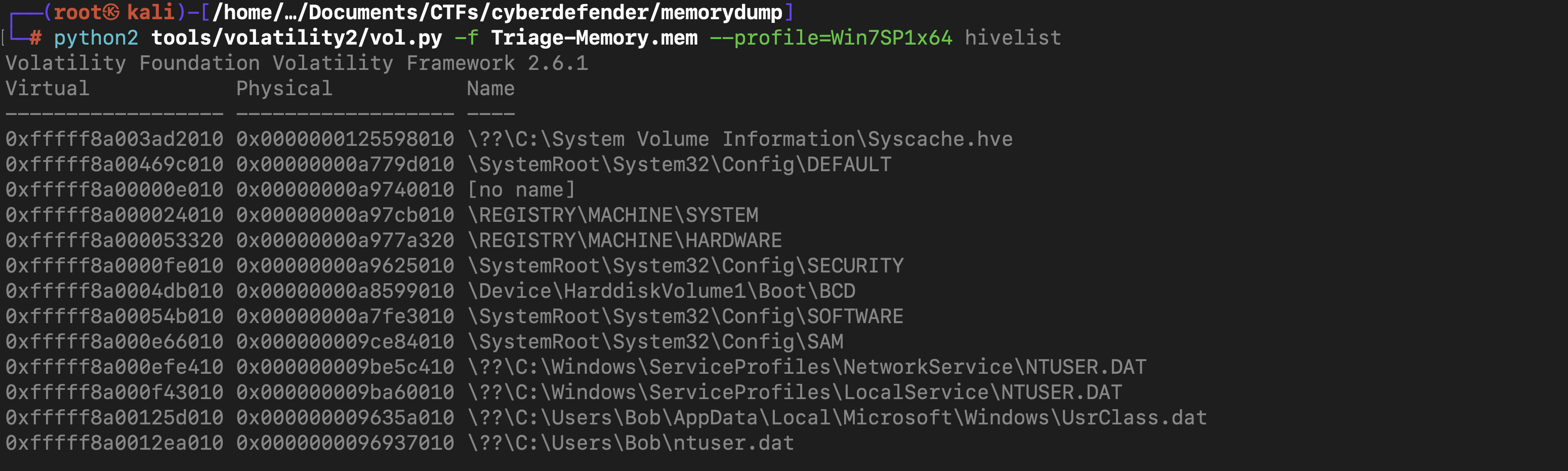
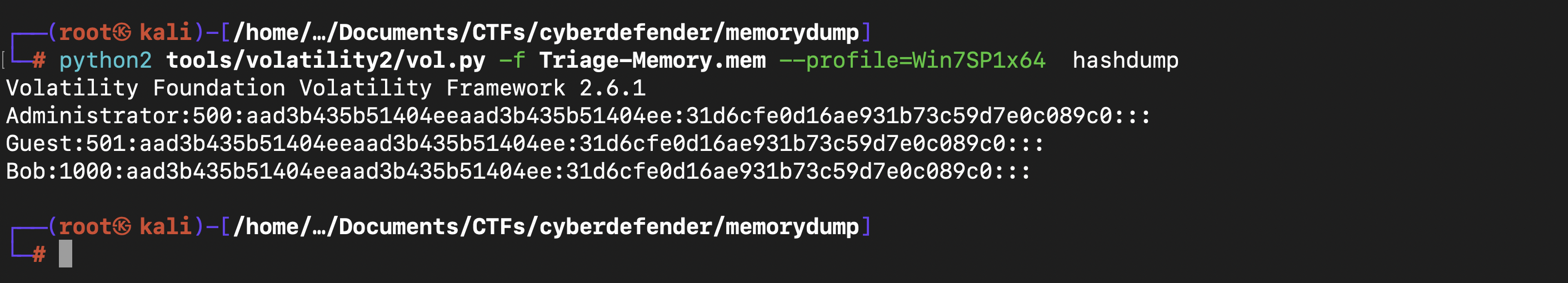
What is the LM hash of Bob’s account?
first we list the hives available with the command python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 hivelist
and with the command python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 hashdump
You can see two hashes, first hash from left side is LM hash and second hash is password hash. Then our LM hash of Bob is aad3b435b51404eeaad3b435b51404ee.
What memory protection constants does the VAD node at 0xfffffa800577ba10 have?
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 vadinfo|grep 0xfffffa800577ba10 -C 4
Volatility Foundation Volatility Framework 2.6.1
Control Flags: Commit: 1
First prototype PTE: fffff8a001021f78 Last contiguous PTE: fffff8a001021ff0
Flags2:
VAD node @ 0xfffffa800577ba10 Start 0x0000000000030000 End 0x0000000000033fff Tag Vad
Flags: NoChange: 1, Protection: 1
Protection: PAGE_READONLY
Vad Type: VadNone
ControlArea @fffffa8005687a50 Segment fffff8a000c4f870
=> PAGE_READONLY
Command: volatility -f Triage-Memory.mem — profile=Win7SP1x64 vadinfo >vad.txt
What memory protection did the VAD starting at 0x00000000033c0000 and ending at 0x00000000033dffff have?
1
2
3
4
5
6
7
8
9
10
11
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 vadinfo|grep '0x00000000033c0000 End 0x00000000033dffff' -C 4
Volatility Foundation Volatility Framework 2.6.1
Flags: CommitCharge: 4, PrivateMemory: 1, Protection: 4
Protection: PAGE_READWRITE
Vad Type: VadNone
VAD node @ 0xfffffa80052652b0 Start 0x00000000033c0000 End 0x00000000033dffff Tag VadS
Flags: CommitCharge: 32, PrivateMemory: 1, Protection: 24
Protection: PAGE_NOACCESS
Vad Type: VadNone
In the same txt file (vad.txt) that we just created,search for the start address “0x00000000033c0000” and ending address“0x00000000033dffff”. We see the memory protection “PAGE_NOACCESS”.
There was a VBS script that ran on the machine. What is the name of the script? (submit without file extension)
Command: python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 cmdline
1
2
3
4
5
6
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 cmdline|grep -i vbs -B 2
Volatility Foundation Volatility Framework 2.6.1
************************************************************************
wscript.exe pid: 5116
Command line : "C:\Windows\System32\wscript.exe" //B //NOLOGO %TEMP%\vhjReUDEuumrX.vbs
The “cmdline” plugin shows the history of all the command-lines that were executed. So after running that command, we look for our required VBS script.
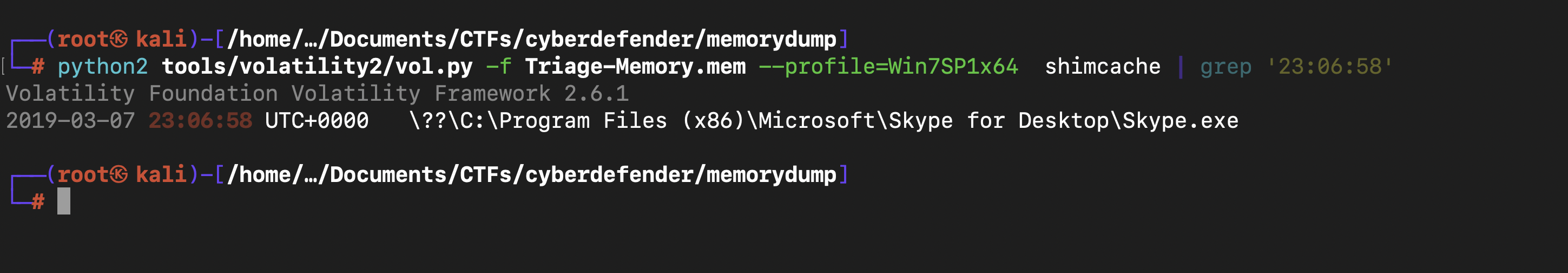
An application was run at 2019-03-07 23:06:58 UTC. What is the name of the program? (Include extension)
Now with CMDLINE: it fails because the program was closed and also they specified the word ‘was’
CONSOLES:It fails because the program was not only closed but the history of command for that process doesnot exist and maybe they turn off PC so i wont exist
with shimcache:
1
2
3
4
5
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 --help | grep shimcache
Volatility Foundation Volatility Framework 2.6.1
shimcache Parses the Application Compatibility Shim Cache registry key
and with grep, we can see the program
What was written in notepad.exe at the time when the memory dump was captured?
1st we find the PID for notepad.exe using the command python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 pslist | grep notepad
and with the command python2 tools/volatility2/vol.py -f Triage-Memory.mem --profile=Win7SP1x64 memdump -p3032 --dump-dir ., we have dumped notepad
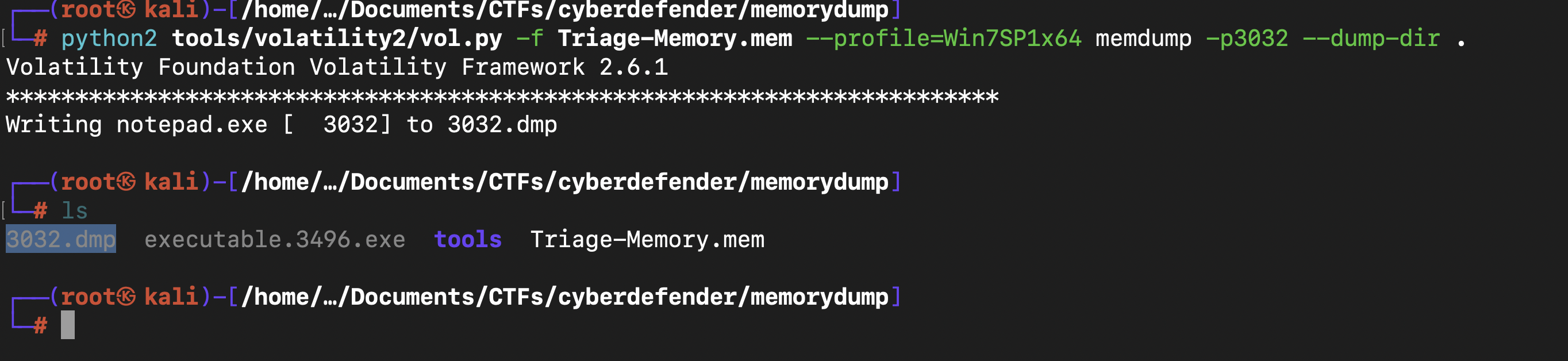 and with the command
and with the command strings 3032.dmp -e l | grep "flag<"
we have dumped notepad
1
2
3
4
5
6
7
┌──(root㉿kali)-[/home/…/Documents/CTFs/cyberdefender/memorydump]
└─# strings 3032.dmp -e l | grep "flag<"
flag<REDBULL_IS_LIFE>
flag<Th>
flag<Th>
flag<TheK>
flag<TheK>
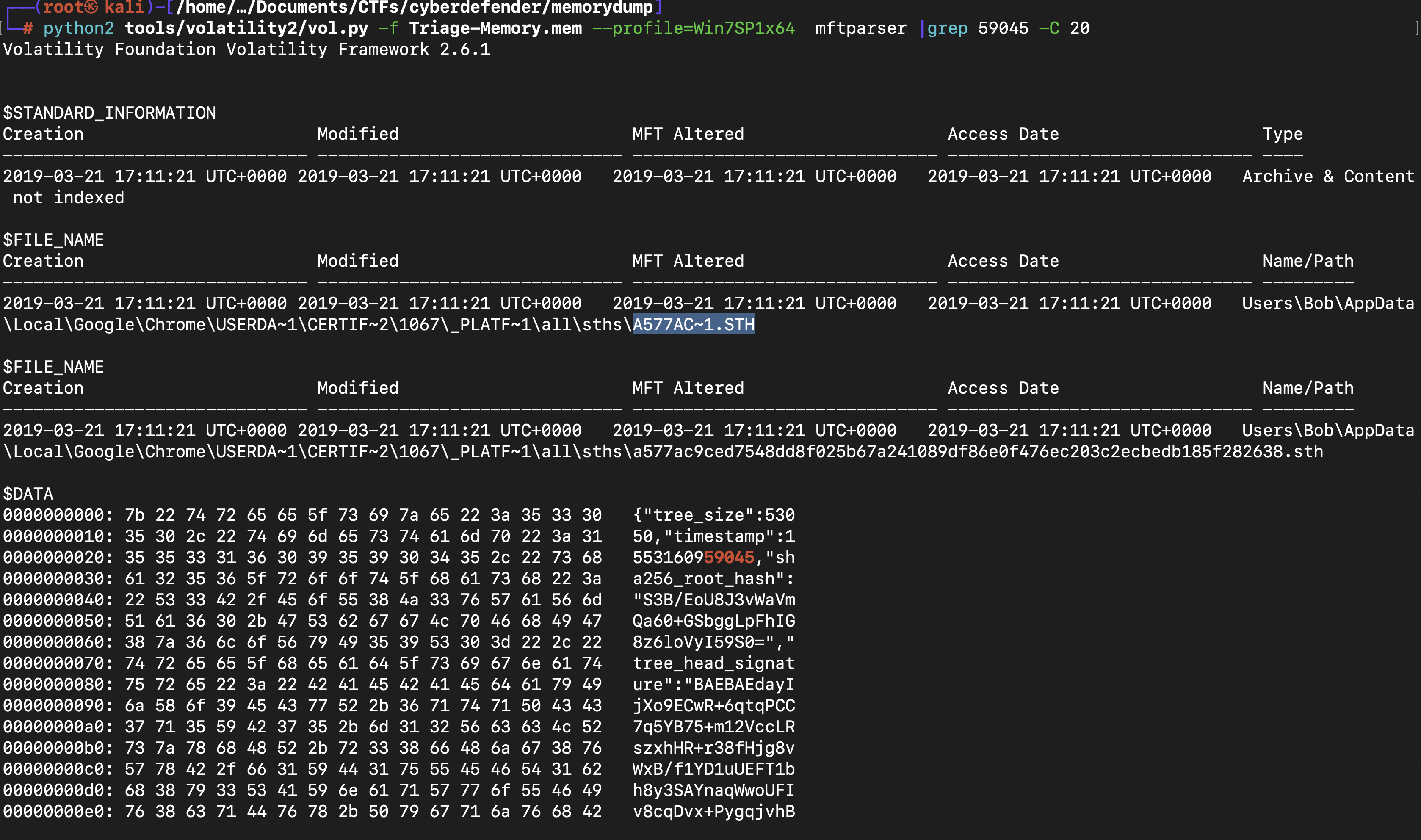
What is the short name of the file at file record 59045?
with mftparser, Scans for and parses potential MFT entries
The “mftparser” plugin is used to parse and analyze the Master File Table (MFT) in a Windows file system. So we store it in a text file. After that we search our required file name at the record “59045”.In this case it is “EMPLOY~1.XLS”.
This box was exploited and is running meterpreter. What was the infected PID?
s we found out earlier in the pslist that the process “UWkpjFjDzM.exe” was malicious whose PID was3496. So, the infected PID is “3496”.